Which Risk Assessment Methodology For Iso 27001 Iso27001 Guide
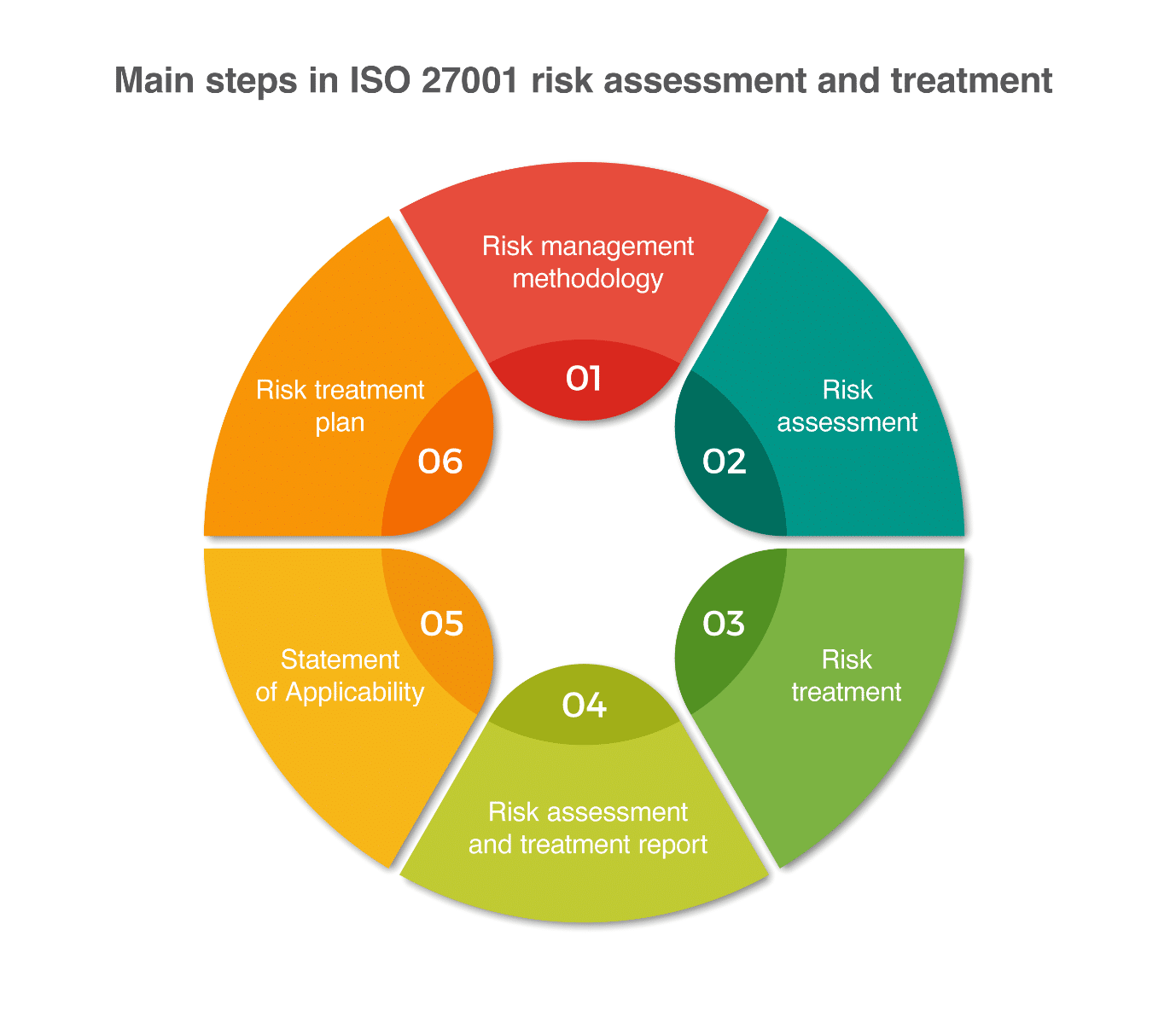
Iso 27001 Risk Assessment Risk Treatment The Complete Guide The current 2022 revision of iso 27001 allows you to identify risks using any methodology you like; however, the methodology called “asset based risk assessment” (defined by the old 2005 revision of iso 27001) is still dominating, and it requires identification of assets, threats, and vulnerabilities. 3. at least annually. an iso 27001 risk assessment really should be completed at least annually and recorded. it is a formal step but allows you to assess what, if anything has changed as well as what, if anything needs addressing. budgets and resources may be required and it allows the effective planning and control.
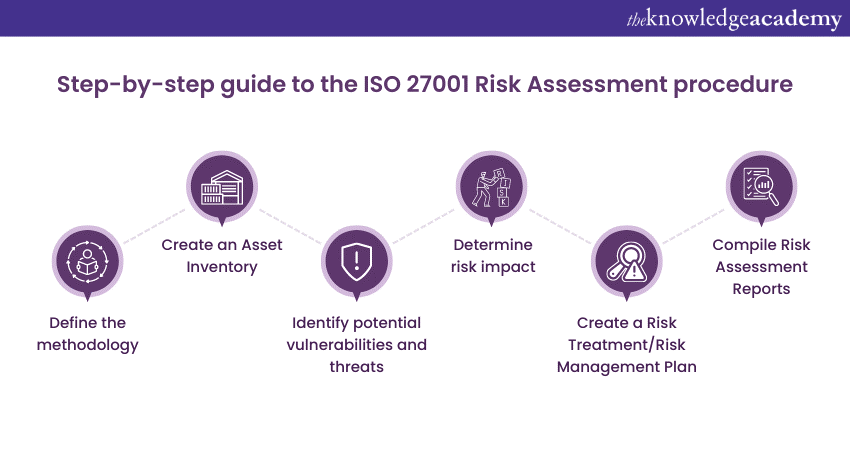
Iso 27001 Risk Assessment A Step By Step Guide Iso 27001 provides a structured approach to risk assessment and risk treatment, ensuring your business stays secure and compliant. in this comprehensive guide, we’ll demystify the entire process, offering clear, actionable steps to identify, assess, and mitigate risks effectively. by the end of this post, you’ll have the confidence and. To simplify risk management for small organisations, consider the following recommendations: a) choose the right framework: it is essential that you include all the five essential components that are required by iso 27001. b) select the appropriate tool: seek software or tools that align with your simplified approach. Clause 6.1.2 of iso 27001 outlines the requirements for an information security risk assessment, requiring that organizations: establish and maintain information security risk criteria. implement repeatable processes that produce consistent, valid, and comparable results. identify information security risks. Apply the information security risk assessment process to identify risks. identify risk owners. analyses the information security risks. assess the potential consequences that would result if the risks were to materialise. assess the realistic likelihood of the occurrence of the risks identified. determine the levels of risk.

Risk Assessment Iso 27001 Xls Clause 6.1.2 of iso 27001 outlines the requirements for an information security risk assessment, requiring that organizations: establish and maintain information security risk criteria. implement repeatable processes that produce consistent, valid, and comparable results. identify information security risks. Apply the information security risk assessment process to identify risks. identify risk owners. analyses the information security risks. assess the potential consequences that would result if the risks were to materialise. assess the realistic likelihood of the occurrence of the risks identified. determine the levels of risk. A risk assessment is a requirement for the iso 27001 standard. if you want to be iso 27001 certified, you’ll need to: identify the risks your organization faces. determine the probability of each risk actually occurring. estimate the potential impact on your business. a risk treatment plan involves deciding how you will respond to each risk. 1. asset identification: the foundation of risk assessment. the first step in the risk assessment process is identifying all assets within your organisation that need to be protected. this involves creating an inventory of your information assets, as well as the associated systems, facilities, and personnel that support their management.
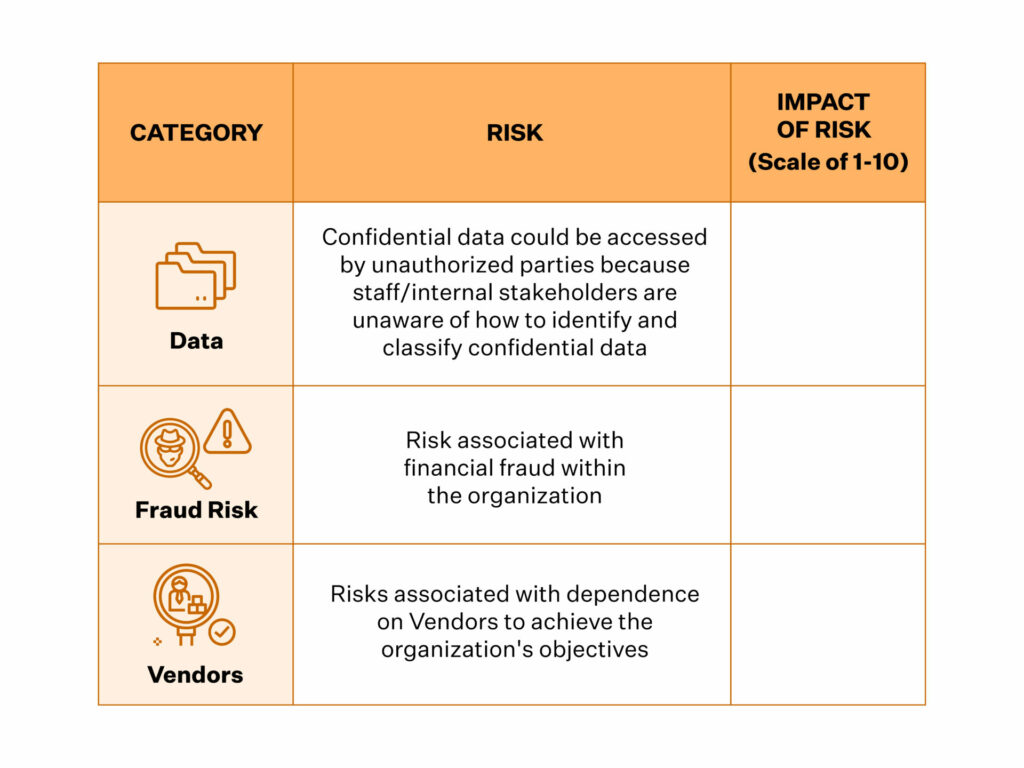
Iso 27001 Risk Assessment Guide To Implementation A risk assessment is a requirement for the iso 27001 standard. if you want to be iso 27001 certified, you’ll need to: identify the risks your organization faces. determine the probability of each risk actually occurring. estimate the potential impact on your business. a risk treatment plan involves deciding how you will respond to each risk. 1. asset identification: the foundation of risk assessment. the first step in the risk assessment process is identifying all assets within your organisation that need to be protected. this involves creating an inventory of your information assets, as well as the associated systems, facilities, and personnel that support their management.

Comments are closed.