What Is A Hipaa Security Risk Assessment Compliancy Group

What Is A Hipaa Security Risk Assessment Compliancy Group Performing a hipaa security risk assessment is the first step in identifying and implementing these safeguards. a security risk assessment consists of conducting an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of ephi. complete my risk assessment. The sixth step to conduct a security risk assessment is “determining the level of risk.”. in this last step, you evaluate your level of risk through the identified combinations of threat likelihood and threat impact. if it is determined that both threat likelihood and threat severity are high, the level of risk would be classified as.
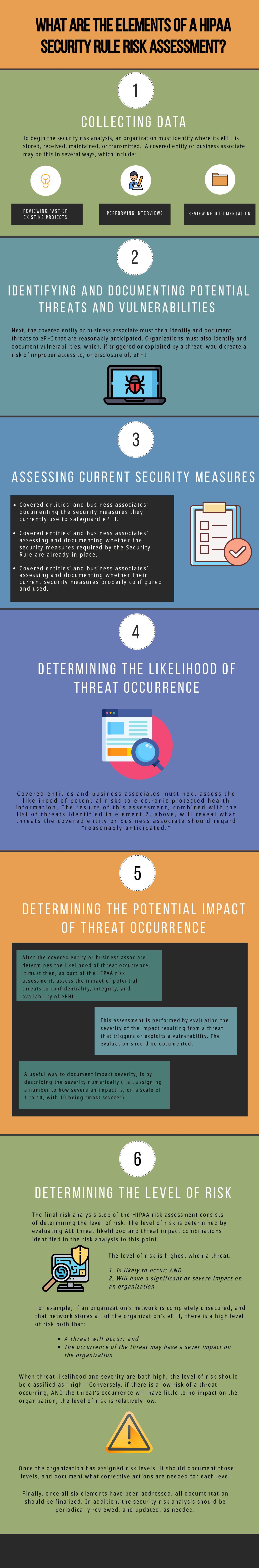
What Is A Hipaa Risk Assessment Checklist Compliancy Group What is a security risk assessment (sra)? the hipaa security rule contains a series of standards to ensure the protection of electronic protected health information. these standards fall into one of three categories: administrative safeguards, physical safeguards, and technical safeguards. A security risk analysis is required by 45 cfr 164.308. the purpose of a risk assessment checklist is to cover the basic implementation requirements of the assessment. the hipaa risk assessment checklist should be developed from the requirements contained in the 6 components. component one of the risk assessment is “collecting data.”. Conducting regular hipaa security risk assessments helps covered entities ensure compliance with hipaa’s administrative, physical and technical safeguards, and helps expose areas where an organization’s protected health information (phi) could be at risk. in today’s digitized healthcare environment, there is no limit to the places where. A risk management policy is a required administrative safeguard under the hipaa security rule. hipaa risk management concepts – vulnerabilities, threats, and risks. to understand what hipaa risk management is, let’s look at and define three terms: vulnerabilities, threats, and risks. vulnerabilities are weaknesses or gaps in an organization.

What Is A Hipaa Security Risk Assessment Compliancy Group Conducting regular hipaa security risk assessments helps covered entities ensure compliance with hipaa’s administrative, physical and technical safeguards, and helps expose areas where an organization’s protected health information (phi) could be at risk. in today’s digitized healthcare environment, there is no limit to the places where. A risk management policy is a required administrative safeguard under the hipaa security rule. hipaa risk management concepts – vulnerabilities, threats, and risks. to understand what hipaa risk management is, let’s look at and define three terms: vulnerabilities, threats, and risks. vulnerabilities are weaknesses or gaps in an organization. 4. use a risk assessment tool. you may be thinking, all of this sounds complicated. well, you wouldn’t be wrong. that’s why we provide security risk management software tools. compliancy group offers clients a guided risk assessment, as well as all other required hipaa self audits. when you work with compliancy group you can be confident. The final security rule general requirement is a “maintenance” requirement. to meet this requirement, the covered entity or business associate must review and modify the security measures it has implemented, as needed, to continue providing reasonable and appropriate protection of ephi. to meet the maintenance requirements, the covered.

How To Conduct A Hipaa Risk Assessment In 6 Steps Checklist 4. use a risk assessment tool. you may be thinking, all of this sounds complicated. well, you wouldn’t be wrong. that’s why we provide security risk management software tools. compliancy group offers clients a guided risk assessment, as well as all other required hipaa self audits. when you work with compliancy group you can be confident. The final security rule general requirement is a “maintenance” requirement. to meet this requirement, the covered entity or business associate must review and modify the security measures it has implemented, as needed, to continue providing reasonable and appropriate protection of ephi. to meet the maintenance requirements, the covered.

How To Conduct A Hipaa Risk Assessment Accountable

Comments are closed.