Threat Security Risk Analysis Risk Assessment Analysis Management
Threat Analysis And Risk Assessment Risk assessment and analysis methods: qualitative and quantitative. a risk assessment determines the likelihood, consequences and tolerances of possible incidents. “risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk related consequences.” 1 the. Cybersecurity risks, derived from system level assessments, are documented through cybersecurity risk registers (csrrs) that are aggregated and used to create an enterprise cybersecurity risk register (enterprise csrr) that, in turn, becomes part of a broader enterprise risk register (err), as depicted in figure 3.

Security Risk Management Threat Analysis Group These events range from natural disasters to public health issues to events caused by humans, including malicious or accidental insider threats. the first step in a risk analysis is to conduct a risk assessment survey. second, organizations identify and analyze the results. third, they develop and subsequently enact a risk management plan. An effective risk assessment helps organizations understand and prioritize potential threats by evaluating the impact of risks. here's a brief risk assessment template for reference: assessment type: tier 1: high risk (significant business exposure) tier 2: medium risk (moderate impact) tier 3: low risk (minimal impact) inherent risk: the risk. Employee awareness: train employees to recognize and respond to potential security threats. cyber security risk assessment examples example 1: large enterprise. large organizations more aptly take up multi site and multi system risk assessments. this involves wide ranging data collection, threat analysis, and active security measures. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security.

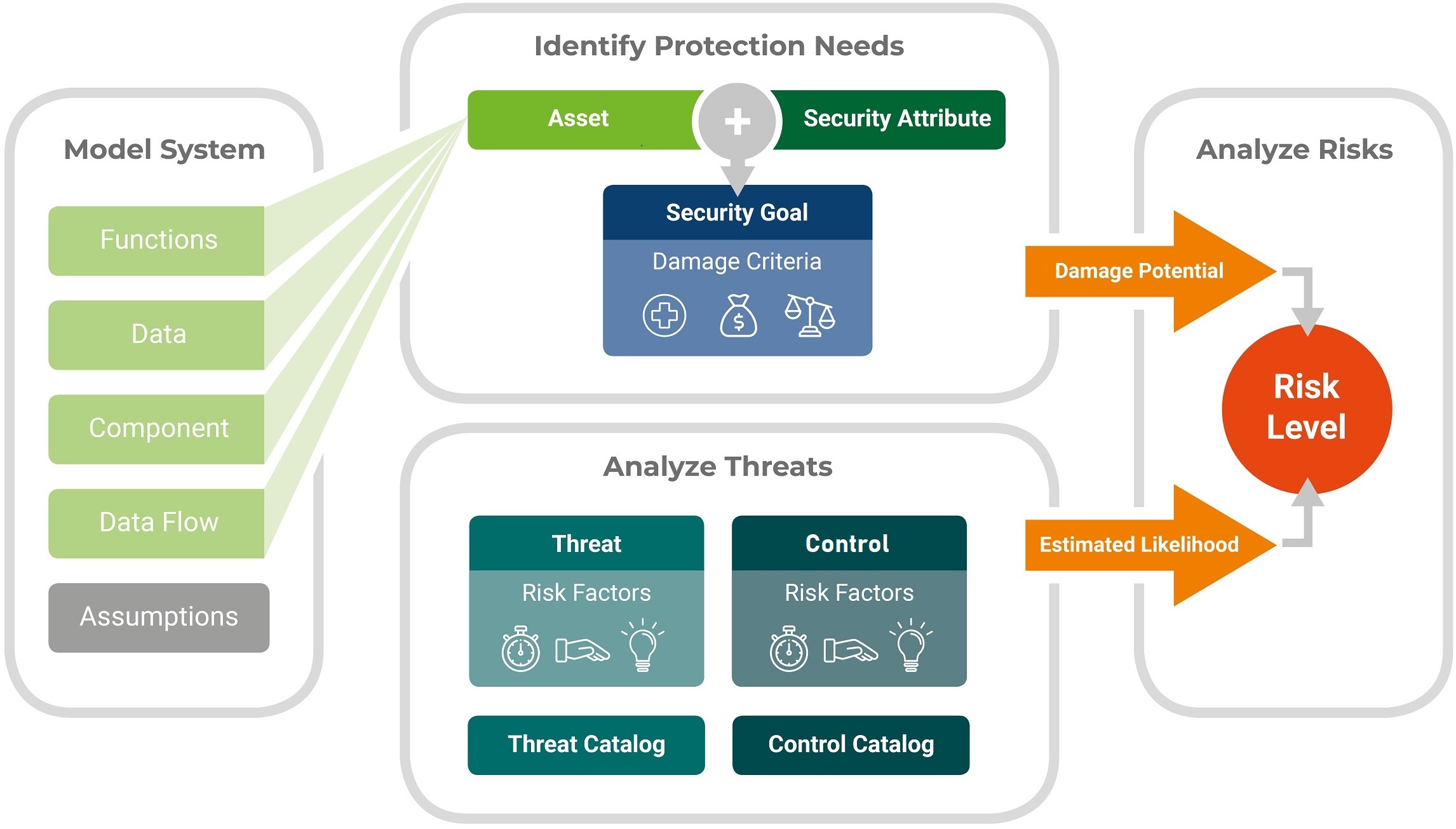
What Is Threat Analysis And Risk Assessment At David Chea Blog Employee awareness: train employees to recognize and respond to potential security threats. cyber security risk assessment examples example 1: large enterprise. large organizations more aptly take up multi site and multi system risk assessments. this involves wide ranging data collection, threat analysis, and active security measures. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security. Tara (threat analysis and risk assessment) is a structured process designed to identify potential cybersecurity threats, assess their impact, and implement strategies to mitigate them. it plays a crucial role in helping automotive companies meet industry standards like iso 21434, which governs cybersecurity risk management in vehicles. by. 1.3 security risk assessment and management process 8 1.3.1 facility characterization 9 1.3.2 threat analysis 10 1.3.3 consequence analysis 11 1.3.4 system effectiveness assessment 13 1.3.5 risk estimation 16 1.3.6 comparison of estimated risk levels 17 1.3.7 risk reduction strategies 17 1.4 presentation to management 18 1.5 risk management.

An 8 Step Risk Assessment For Your Facility S Security Facilities Tara (threat analysis and risk assessment) is a structured process designed to identify potential cybersecurity threats, assess their impact, and implement strategies to mitigate them. it plays a crucial role in helping automotive companies meet industry standards like iso 21434, which governs cybersecurity risk management in vehicles. by. 1.3 security risk assessment and management process 8 1.3.1 facility characterization 9 1.3.2 threat analysis 10 1.3.3 consequence analysis 11 1.3.4 system effectiveness assessment 13 1.3.5 risk estimation 16 1.3.6 comparison of estimated risk levels 17 1.3.7 risk reduction strategies 17 1.4 presentation to management 18 1.5 risk management.

Risk Assessment Matrices Tools To Visualise Risk

Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix

Comments are closed.