Threat And Vulnerability Assessment Business Protection Specialists

Security Risk Assessment Business Protection Specialists As professional physical security consultants, business protection specialists (bps) are committed to accurately evaluating your specific threat landscape and security vulnerabilities with unmatched diligence and expertise. our comprehensive and proactive approach to physical security is a key element of our service, allowing us to tailor state. Security audits, security threat and vulnerability assessment, security consulting, security design & construction administration, security program development, and regulatory security compliance.

Vulnerability Assessments 4 Crucial Steps For Identifying As a well respected physical security expert for more than 30 years, frank pisciotta, csc, has partnered with hundreds of organizations around the world as president and ceo of business protection specialists, inc. (bps). since founding bps in 1990, frank has guided nearly 5,000 threat assessment, risk analysis, security design, and related. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security. Security and risk management consulting. kroll’s team excels at proactive security consulting and expert advisory solutions, aligning our comprehensive offerings with your enterprise’s risk appetite. we offer personnel, expertise, advisory and bandwidth when our clients are challenged in ways that stress their comfort or internal capabilities. The national institute of standards and technology’s (nist) special publication 800 30 provides guidelines for how to conduct a threat assessment via implementing risk assessment methodologies—and will help optimize how you identify, analyze, and mitigate threat and vulnerability risks to your it assets. although the risk assessment.

Vulnerability Assessment Websec Services Security and risk management consulting. kroll’s team excels at proactive security consulting and expert advisory solutions, aligning our comprehensive offerings with your enterprise’s risk appetite. we offer personnel, expertise, advisory and bandwidth when our clients are challenged in ways that stress their comfort or internal capabilities. The national institute of standards and technology’s (nist) special publication 800 30 provides guidelines for how to conduct a threat assessment via implementing risk assessment methodologies—and will help optimize how you identify, analyze, and mitigate threat and vulnerability risks to your it assets. although the risk assessment. Vulnerability assessment is the ongoing, regular process of defining, identifying, classifying and reporting cyber vulnerabilities across endpoints, workloads, and systems. most often, vulnerability assessments are automated using a security tool provided by a third party security vendor. the purpose of this tool is to help the organization. The threat assessment is one of the most efficient tools security teams use to recognize and respond to physical security threats or information technology risks. one of the most significant benefits of threat vulnerability assessments is they standardize the approach to threat across a corporation. in a large company, for example, security.
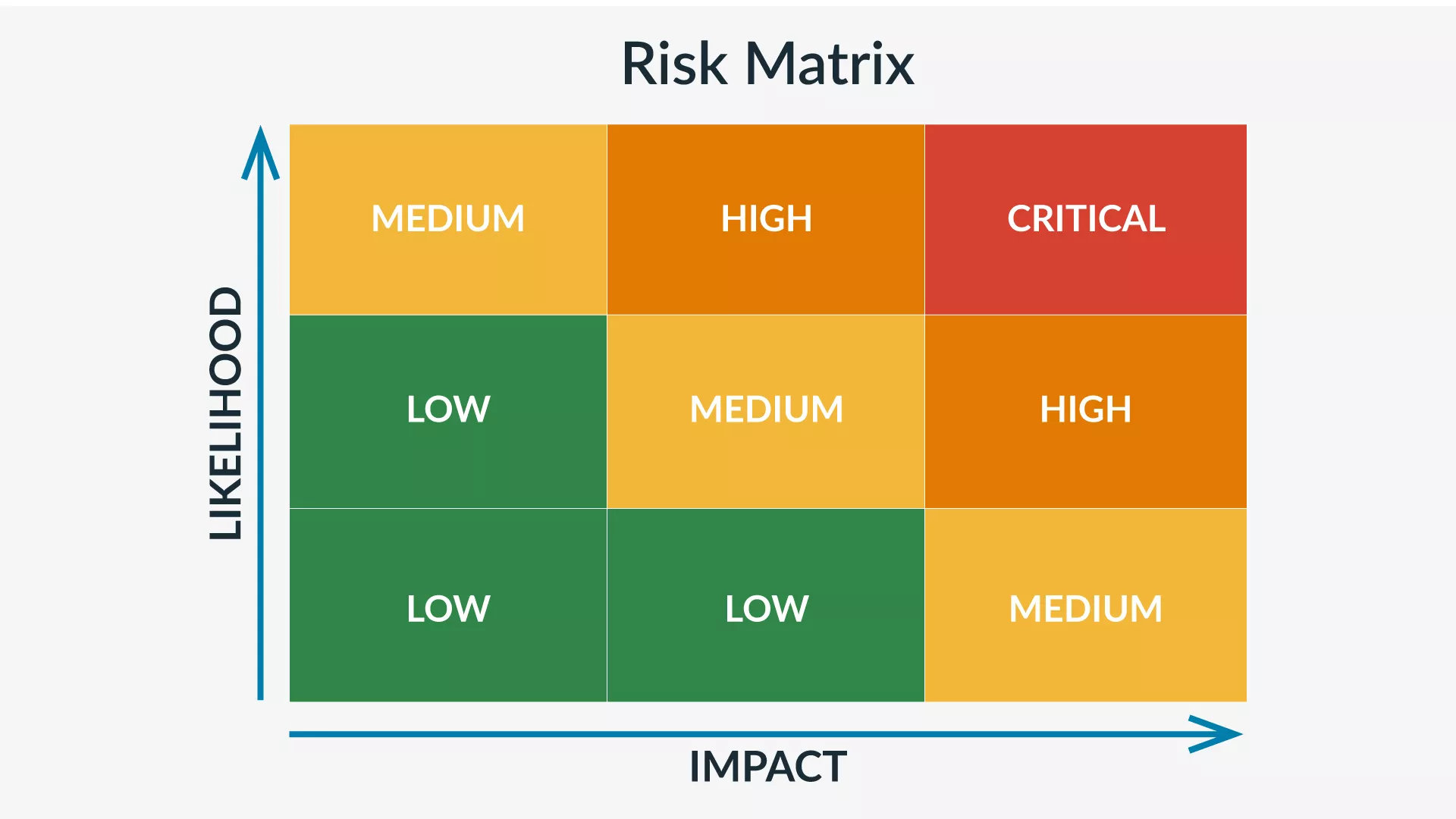
Threat And Vulnerability Assessment Free Template Vulnerability assessment is the ongoing, regular process of defining, identifying, classifying and reporting cyber vulnerabilities across endpoints, workloads, and systems. most often, vulnerability assessments are automated using a security tool provided by a third party security vendor. the purpose of this tool is to help the organization. The threat assessment is one of the most efficient tools security teams use to recognize and respond to physical security threats or information technology risks. one of the most significant benefits of threat vulnerability assessments is they standardize the approach to threat across a corporation. in a large company, for example, security.

Comments are closed.