Threat Analysis And Risk Assessment
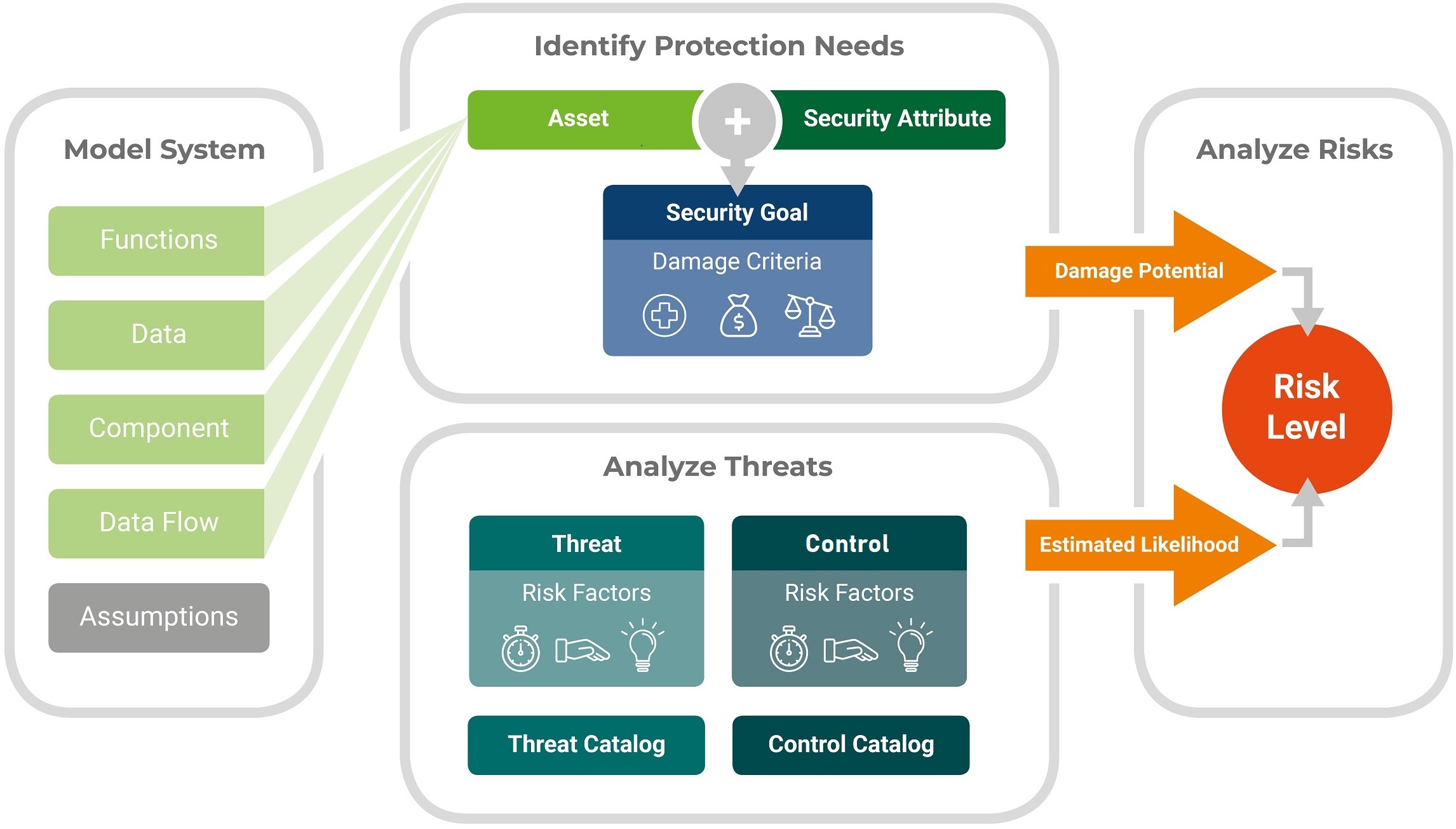
Threat Analysis And Risk Assessment Learn what threat and risk assessment is, why it is important, and how to conduct it. find out the goals, steps, methods, and best practices of threat and risk assessment for cybersecurity and compliance. Learn how to perform tara according to iso sae 21434 with security analyst, a tool that supports modeling, threat analysis and risk assessment. see the workflow, the entities, the criteria and the controls involved in tara.

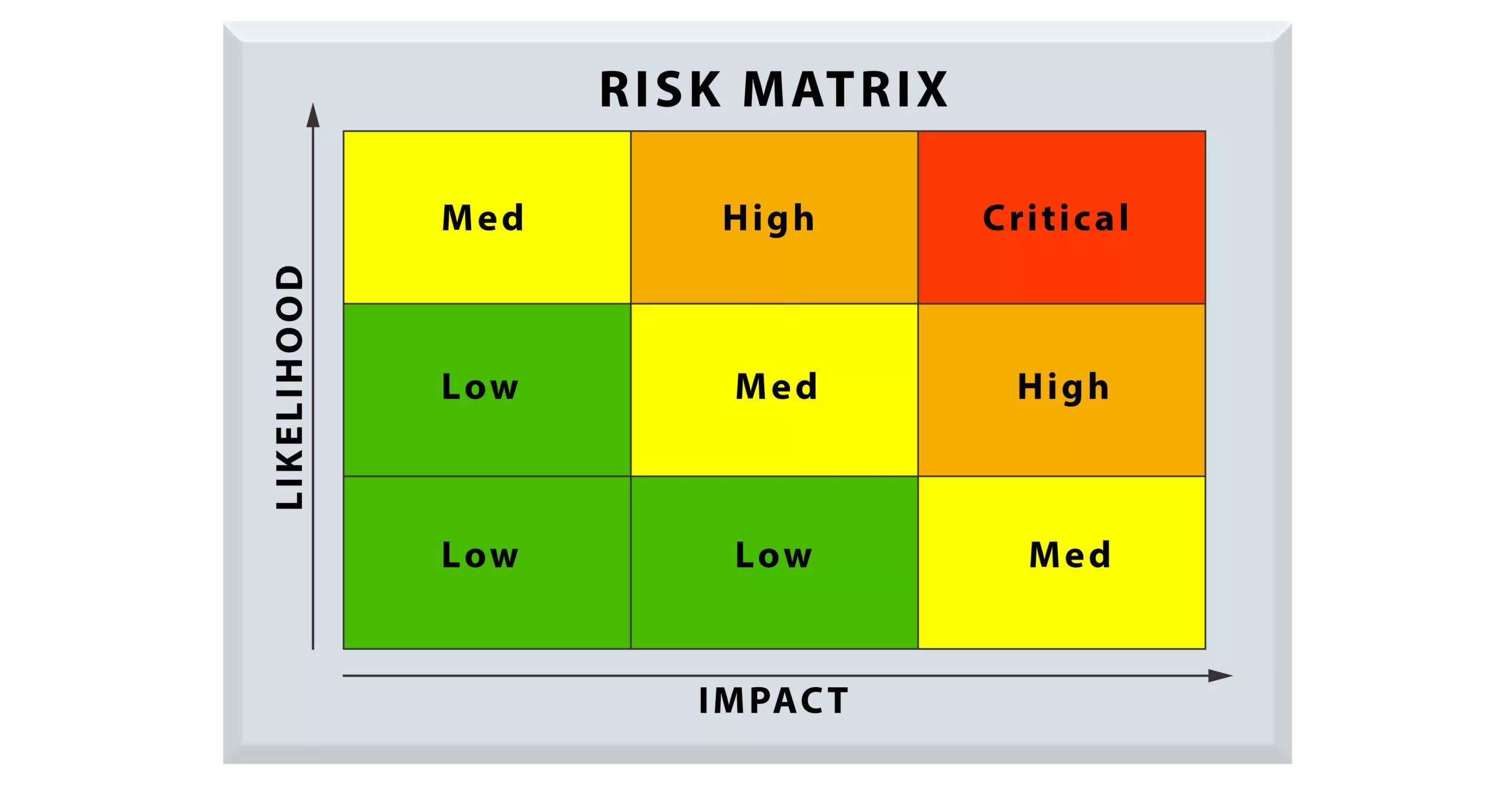
What Is Threat Analysis And Risk Assessment At David Chea Blog Learn how to perform risk assessment and analysis using qualitative and quantitative techniques. compare the advantages, disadvantages and applications of each method and see examples of risk matrices and scenarios. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security. The same threat risk assessment and analysis process can be applied to cybersecurity, which is a key component of overall risk assessment. a cybersecurity threat risk assessment focuses on protecting access to information (e.g., data, personal information), access to networks (e.g., the internet at your offices), software (e.g. Whether of “human” or “nonhuman” origin, a cyberthreat analysis must scrutinize each potential vector that may bring about conceivable security risk to a system or asset. to support an organization’s efforts to identify, remediate and prepare for potential threats, cyberthreat analysis provides a structured, repeatable process.

Risk Assessment Matrices Tools To Visualise Risk The same threat risk assessment and analysis process can be applied to cybersecurity, which is a key component of overall risk assessment. a cybersecurity threat risk assessment focuses on protecting access to information (e.g., data, personal information), access to networks (e.g., the internet at your offices), software (e.g. Whether of “human” or “nonhuman” origin, a cyberthreat analysis must scrutinize each potential vector that may bring about conceivable security risk to a system or asset. to support an organization’s efforts to identify, remediate and prepare for potential threats, cyberthreat analysis provides a structured, repeatable process. Learn how to build and optimize the threat assessment and management process to understand various threat landscapes. this article covers the importance, benefits, and key elements of threat assessment for different security functions and programs. A systematic review of threat analysis and risk assessment (tara) methodologies for connected automated vehicles (cavs) of different automation levels. the review evaluates the applicability, suitability and gaps of tara methods based on threat analysis avenues, risk metrics, privacy impact and standards compliance.
4 Steps To A Business Threat Assessment Template Learn how to build and optimize the threat assessment and management process to understand various threat landscapes. this article covers the importance, benefits, and key elements of threat assessment for different security functions and programs. A systematic review of threat analysis and risk assessment (tara) methodologies for connected automated vehicles (cavs) of different automation levels. the review evaluates the applicability, suitability and gaps of tara methods based on threat analysis avenues, risk metrics, privacy impact and standards compliance.

Tips For Your Cybersecurity Threat Assessment Bcngrafics

Comments are closed.