The 7 Steps To Developing A Cloud Security Plan Insight
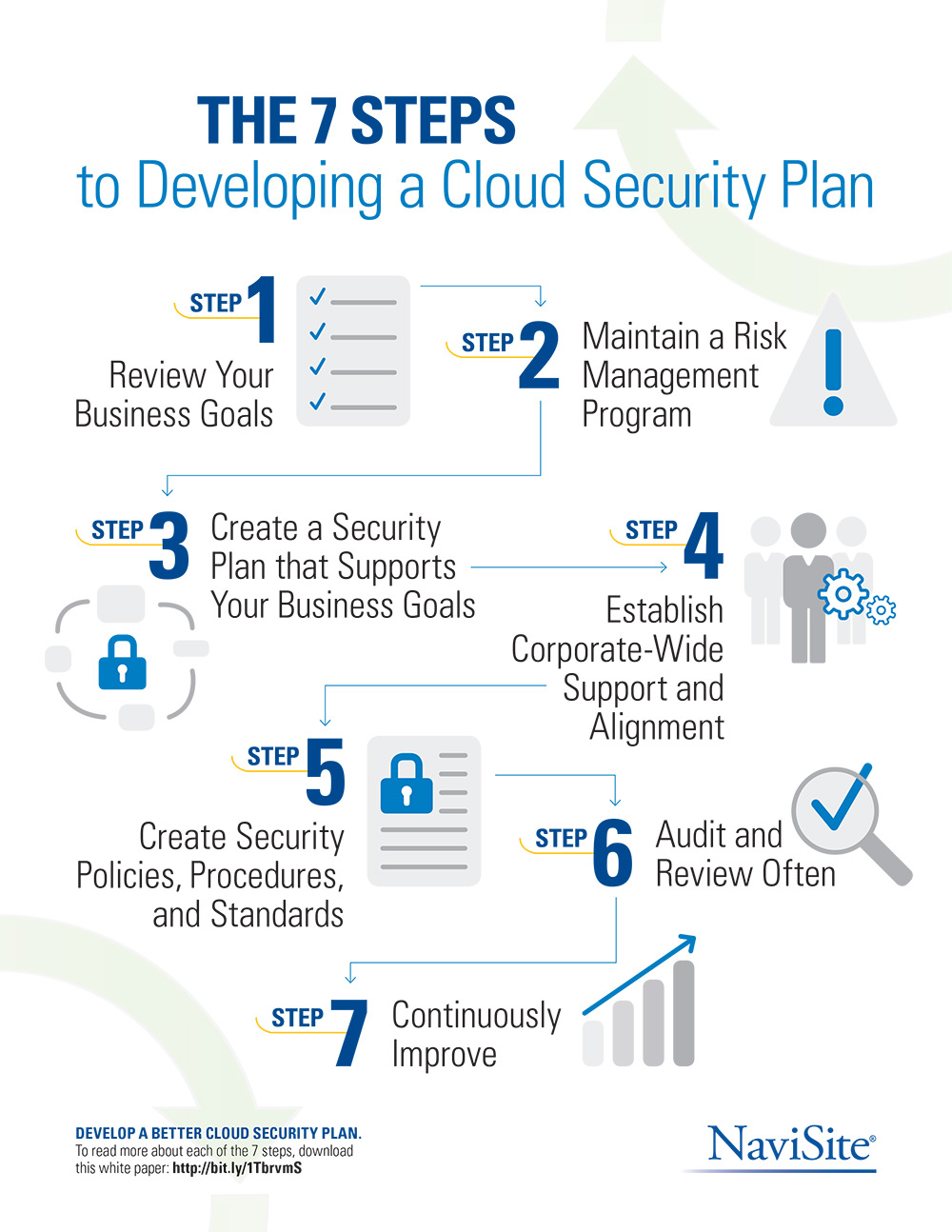
The 7 Steps To Developing A Cloud Security Plan Insight The seven cloud security plan steps are: 1. review your business goals: cleary defining how the cloud will support your business goals helps you make informed decisions throughout your cloud journey. without a clear understanding of how your cloud adoption supports the business, you can end up wasting resources, driving up costs and creating. These seven steps are meant to serve as a framework to guide companies as they develop a secure cloud computing plan. for the complete checklist of the above seven steps download the white paper titled 7 steps to developing a cloud security plan. david grimes is the chief technology officer at navisite.
The 7 Steps To Developing A Cloud Security Plan Insight The above checklist can serve as a manageable process framework for enterprise security, compliance and it professionals to craft a successful cloud computing security plan. to learn more about each of the seven steps, download the white paper 7 steps to developing a cloud security plan. A cloud security strategy is a framework of tools, policies, and procedures for keeping your data, applications, and infrastructure in the cloud safe and protected from security risks. it involves implementing robust security controls — such as encryption, identity and access management, network segmentation, and intrusion detection systems. Secure cloud services plan breaks down into the following seven steps: by following these steps organizations can structure security and compliance programs to take advantage of the economic advantages of managed cloud services while meeting organizational security and compliance objectives. 5 figure 1: 7 steps. step 6: audit and review often. Access and authentication controls. the foundational principle of cloud security is to ensure that only authorized users can access your environment. the emphasis should be on strong, adaptive authentication mechanisms that can respond to varying risk levels. build an authentication framework that is non static.

7 Steps To Developing A Cloud Security Plan Secure cloud services plan breaks down into the following seven steps: by following these steps organizations can structure security and compliance programs to take advantage of the economic advantages of managed cloud services while meeting organizational security and compliance objectives. 5 figure 1: 7 steps. step 6: audit and review often. Access and authentication controls. the foundational principle of cloud security is to ensure that only authorized users can access your environment. the emphasis should be on strong, adaptive authentication mechanisms that can respond to varying risk levels. build an authentication framework that is non static. The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (iam), network security, and compliance with relevant laws and regulations. it can be performed by internal security teams or by third party security experts who are specialized in cloud security. Step 1. identification and classification of sensitive data. the first step in planning a cloud security strategy is to identify and classify your sensitive data. this involves identifying all the data that is critical to your organization and classifying it according to its sensitivity and risk level. sensitive data may include financial.

Comments are closed.