Security Risk Assessment The Necessity Of This Report

Security Risk Assessment Report The Necessity Of This Report Moreover, this assessment doesn’t solely consider the physical aspects like hardware and structural layout but also extends to overlooked elements. subsequently, in depth, ongoing, and active research precedes the formulation of the security plan within the security assessment. read more independent security risk assessment know the difference. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization's it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security.
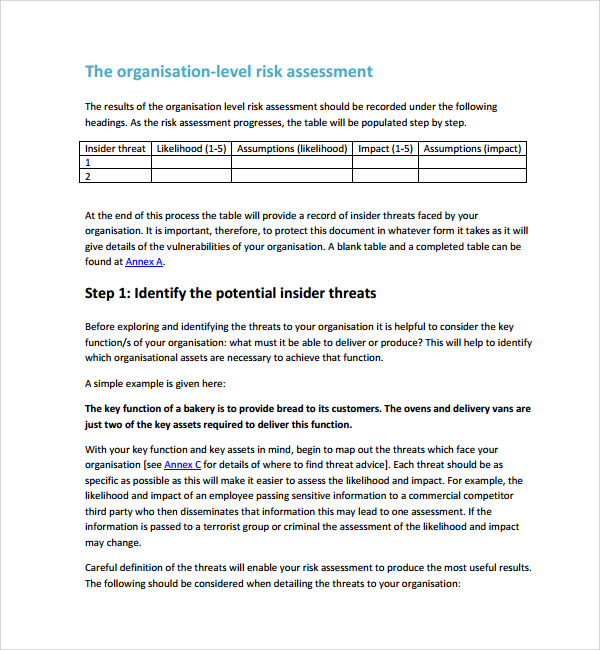
10 Sample Security Risk Assessment Templates Pdf Word Sample Identified security issues are ranked according to the risk they pose. a security risk assessment report identifies properly secured systems and those with issues, providing specific technical recommendations, such as firewall configuration and network scanning. risk management is the ongoing effort to identify and fix all the known issues. Security risk assessment training is a set of informational lessons to help employees develop skills for identifying, analyzing, and evaluating security risks. it is important to invest in this type of training to help your organization stay safe in the digital space, as c ybersecurity awareness training can serve as the starting point for. The process of determining inherent risks in an organization is via a risk assessment. while there are multiple best practices and frameworks (iso 27005, nist sp 800 30, fair) around conducting a risk assessment, the basics can be captured in the following steps: identify assets. determine the critical level of assets. 7. document the results clearly and concisely in a report. the next step is to document the results clearly and concisely. so, here’s how it goes: a good risk assessment report presents the findings of threat and vulnerability assessments in a way that helps prioritize your remediation plan.
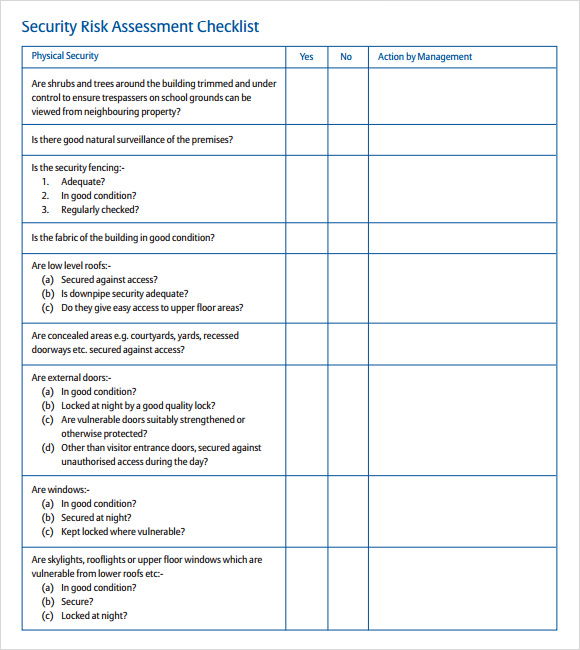
Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word Excel The process of determining inherent risks in an organization is via a risk assessment. while there are multiple best practices and frameworks (iso 27005, nist sp 800 30, fair) around conducting a risk assessment, the basics can be captured in the following steps: identify assets. determine the critical level of assets. 7. document the results clearly and concisely in a report. the next step is to document the results clearly and concisely. so, here’s how it goes: a good risk assessment report presents the findings of threat and vulnerability assessments in a way that helps prioritize your remediation plan. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help.

Comments are closed.