Phases Of Ethical Hacking Hith Blog Hackerinthehouse

Phases Of Ethical Hacking Hith Blog Hackerinthehouse Lets quickly see the phases of hacking. reconnaissance scanning gaining access maintaining access clearing track . 1.reconnaissance: its 1st step in ethical hacking attacker gather information about the victim here we usually collect information about three groups. a. network b. host. there are two types footprinting:. Operations security for red teams – hackerinthehouse.in shakshi tripathi december 5, 2022 operations security for red teams opsec in military opsec overview opsec or operations security is a military based concept which can….

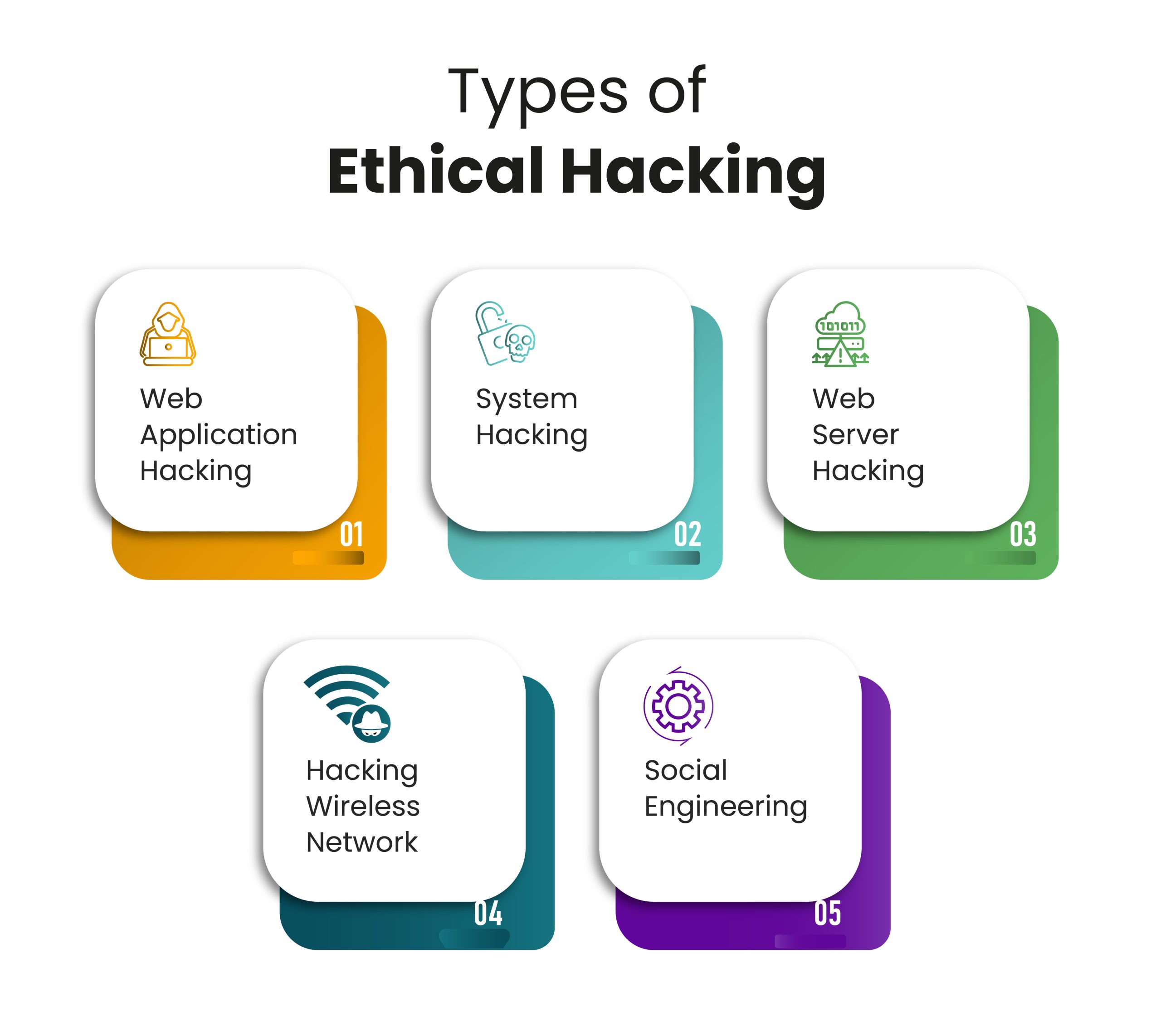
Phases Of Ethical Hacking Hith Blog Hackerinthehouse This blog is written for to know the system hacking works, i am explaining how to hack system using metaspolit, anyone who want learn ethical hacking can read this article before get started let me remind you what you need kali linux need to be installed metaspolit framework in kali linux have metasploitable installed. Ethical hacking plays a crucial role in contemporary cybersecurity by enabling organizations to detect and mitigate security risks proactively, preventing potential exploits by malicious actors. There are five phases of ethical hacking: reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. the primary goal of ethical hacking is to discover potential security risks before malicious attackers exploit them. ethical hackers require strong technical expertise in computer networks, systems, and security procedures. Understanding the numerous intricacies of cybersecurity can often feel daunting. yet, the term that often boggles people's minds is 'ethical hacking'. this blog post aims to demystify the fundamental phases of ethical hacking, in hope of providing a robust knowledge base for those interested in the field of cybersecurity. first off, let's briefly touch upon what ethical hacking indeed is.
Phases Of Ethical Hacking Infosectrain There are five phases of ethical hacking: reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. the primary goal of ethical hacking is to discover potential security risks before malicious attackers exploit them. ethical hackers require strong technical expertise in computer networks, systems, and security procedures. Understanding the numerous intricacies of cybersecurity can often feel daunting. yet, the term that often boggles people's minds is 'ethical hacking'. this blog post aims to demystify the fundamental phases of ethical hacking, in hope of providing a robust knowledge base for those interested in the field of cybersecurity. first off, let's briefly touch upon what ethical hacking indeed is. Penetration testing is how ethical hackers work. they think like bad hackers and attack their own systems. this helps them understand their strengths and weaknesses and protect their organizational assets. a pen test is comprised of multiple stages. you cannot simply get into a system by using a tool unless the target is hopelessly vulnerable. Knowledge of coding in relevant programming languages. an understanding of computer networks, both wired and wireless. basic hardware knowledge. creative and analytical thinking abilities. database proficiency. a solid foundation in information security principles. most ethical hackers also have a degree in a technology related field, such as.

What Are The 5 Phases Of Ethical Hacking Penetration testing is how ethical hackers work. they think like bad hackers and attack their own systems. this helps them understand their strengths and weaknesses and protect their organizational assets. a pen test is comprised of multiple stages. you cannot simply get into a system by using a tool unless the target is hopelessly vulnerable. Knowledge of coding in relevant programming languages. an understanding of computer networks, both wired and wireless. basic hardware knowledge. creative and analytical thinking abilities. database proficiency. a solid foundation in information security principles. most ethical hackers also have a degree in a technology related field, such as.

Comments are closed.