Pdf Ethical Hacking Tools Techniques And Approaches
Pdf Ethical Hacking Tools Techniques And Approaches Ethical hacking also known as penetration testing or intrusion testing or red teaming has become a major concern for businesses and governments. companies are worried about the possibility of. Techniques of ethical hacking: information gathering vulnerability scanning exploitation test analysis nmap nmap is a best tool ever that are used in the second phase of ethical hacking means port scanning, nmap was originally command line tool that has been developed for only unix linux based operating system but now its windows version is.

Ethical Hacking Tutorial In Pdf Sensitive information for ill gotten gains — usually from the as an unauthorized user. hackers go for almost any system they can compromise. some prefer prestigious, well protected but hacking into anyone’s system increases an attacker’s hacker circles. malicious internal users (or internal attackers) try to compromise. Part i hacker techniques and tools 1 chapter 1 hacking: the next generation 3 profiles and motives of different types of hackers 4 controls 6 the hacker mindset 6 motivations of hackers 7 a look at the history of computer hacking 9 ethical hacking and penetration testing 10 the role of ethical hacking 11 ethical hackers and the c i a triad 13. Ethical hackers are employed for threat evaluation and security. it is important to note that an ethical hacker has the consent of the organization that hired them. ethical hackers use the same techniques and tools as attackers. ethical hackers must possess the following skills: thorough knowledge of both software and hardware, a good understanding. Certified ethical hacking the 5 phases every hacker must follow phase 1—reconnaissance reconnaissance refers to the preparatory phase where an attacker gathers as much information as possible about the target prior to launching the attack. also in this phase, the attacker draws on competitive intelligence to learn more about the target.

Pdf Ethical Hacking Tools Techniques And Approaches Ethical hackers are employed for threat evaluation and security. it is important to note that an ethical hacker has the consent of the organization that hired them. ethical hackers use the same techniques and tools as attackers. ethical hackers must possess the following skills: thorough knowledge of both software and hardware, a good understanding. Certified ethical hacking the 5 phases every hacker must follow phase 1—reconnaissance reconnaissance refers to the preparatory phase where an attacker gathers as much information as possible about the target prior to launching the attack. also in this phase, the attacker draws on competitive intelligence to learn more about the target. Professional process to model techniques of real world attackers on a defined target to find and exploit vulnerabilities for the purpose of improving security. makes use of and includes ethical hacking techniques. has a more limited focus and is a subset of ethical hacking. must remain within the defined scope and rules of. O 1 ethical hacking, ethics, and legalitycopyrighted materialmost people think hackers have extraordinary skill and knowl edge that allow t. em to hack into computer systems and find valuable information. the term hacker conjures up images of a young compute. whiz who types a few commands at a computer screen—and poof! the computer s.

Ethical Hacking Tools And Software Every Hacker Must Know Dataflair Professional process to model techniques of real world attackers on a defined target to find and exploit vulnerabilities for the purpose of improving security. makes use of and includes ethical hacking techniques. has a more limited focus and is a subset of ethical hacking. must remain within the defined scope and rules of. O 1 ethical hacking, ethics, and legalitycopyrighted materialmost people think hackers have extraordinary skill and knowl edge that allow t. em to hack into computer systems and find valuable information. the term hacker conjures up images of a young compute. whiz who types a few commands at a computer screen—and poof! the computer s.

Ethical Hacking Techniques And Tools
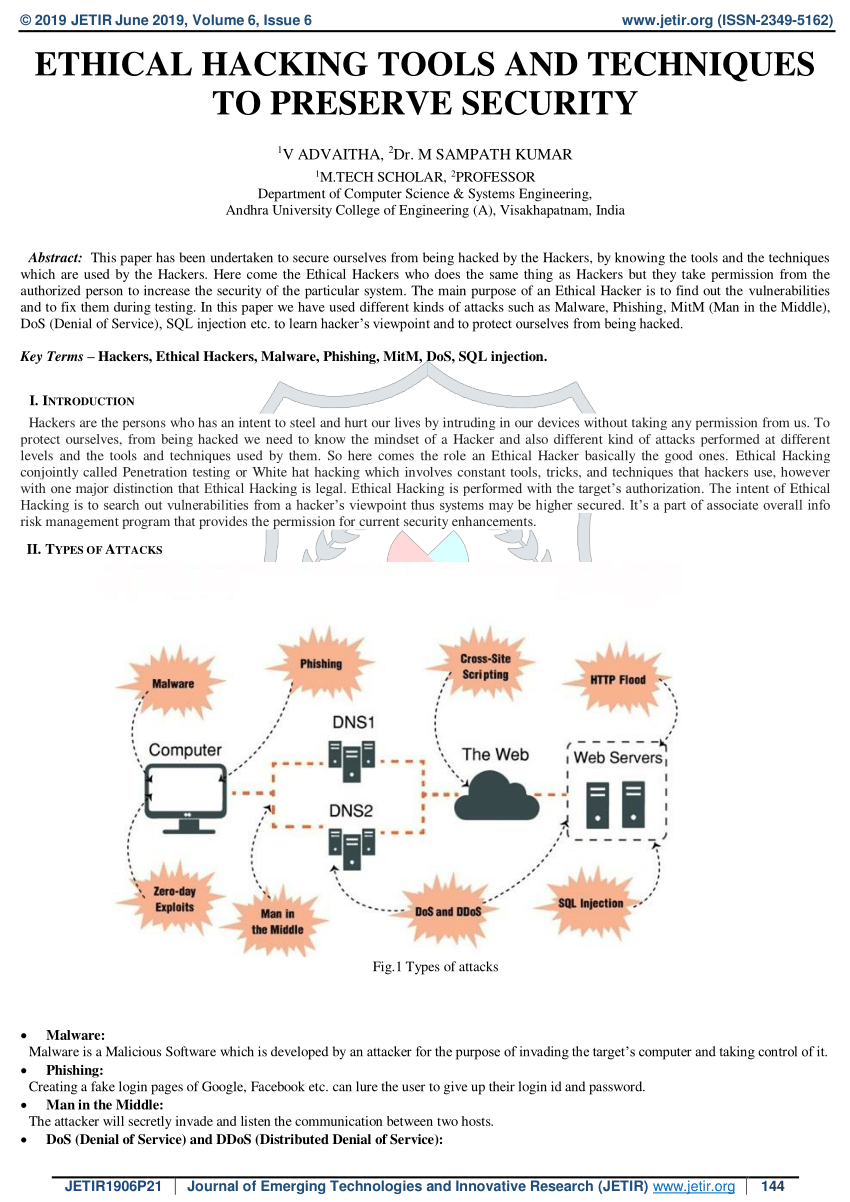
Pdf Ethical Hacking Tools And Techniques To Preserve Security

Comments are closed.