Nist Cybersecurity Framework Successful Implementation Guide Rules Pdf

Nist Cybersecurity Framework Successful Implementation Guide Rules Pdf The cybersecurity framework (csf) 2.0 is designed to help organizations of all sizes and sectors — including industry, government, academia, and nonprofit — to manage and reduce their cybersecurity risks. it is useful regardless of the maturity level and technical sophistication of an organization’s cybersecurity programs. Id.ra 01: vulnerabilities in assets are identified, validated, and recorded. ex1: use vulnerability management technologies to identify unpatched and misconfigured software. ex2: assess network and system architectures for design and implementation weaknesses that affect cybersecurity.

Nist Cybersecurity Framework Implementation Tier Categories Rules Pdf The nist cybersecurity framework (csf) 2.0 provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. it offers a taxonomy of high level cybersecurity outcomes that can be used by any organization — regardless of its size, sector, or maturity — to better understand, assess, prioritize, and communicate its cybersecurity efforts. the csf does. On march 20, 2024, nist hosted a webinar titled “overview of the nist cybersecurity framework 2.0 small business quick start guide.”. the video recording and slides are available here. aspen institute hosted a discussion on csf 2.0, including the under secretary for standards and technology and nist director laurie locascio. the video. This document intends to provide direction and guidance to those organizations – in any sector or community – seeking to improve cybersecurity risk management via utilization of the nist framework for improving critical infrastructure cybersecurity (cybersecurity framework or the framework). cybersecurity is an important and amplifying component of an organization’s overall risk. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. together, these functions provide a comprehensive view for managing cybersecurity risk. this resource & overview guide offers details about each function to serve as potential starting points. the csf 2.0 is comprised of:.

Pdf A Guide To Successfully Implementing The Nist Cybersecurity This document intends to provide direction and guidance to those organizations – in any sector or community – seeking to improve cybersecurity risk management via utilization of the nist framework for improving critical infrastructure cybersecurity (cybersecurity framework or the framework). cybersecurity is an important and amplifying component of an organization’s overall risk. The csf 2.0 is organized by six functions — govern, identify, protect, detect, respond, and recover. together, these functions provide a comprehensive view for managing cybersecurity risk. this resource & overview guide offers details about each function to serve as potential starting points. the csf 2.0 is comprised of:. Abstract. the nist cybersecurity framework (csf) 2.0 can help organizations manage and reduce their cybersecurity risks as they start or improve their cybersecurity program. the csf outlines specific outcomes that organizations can achieve to address risk. The framework is organized by five key functions– identify, protect, detect, respond, recover. these five widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time. the activities listed under each function may offer a good starting point for your organization:.
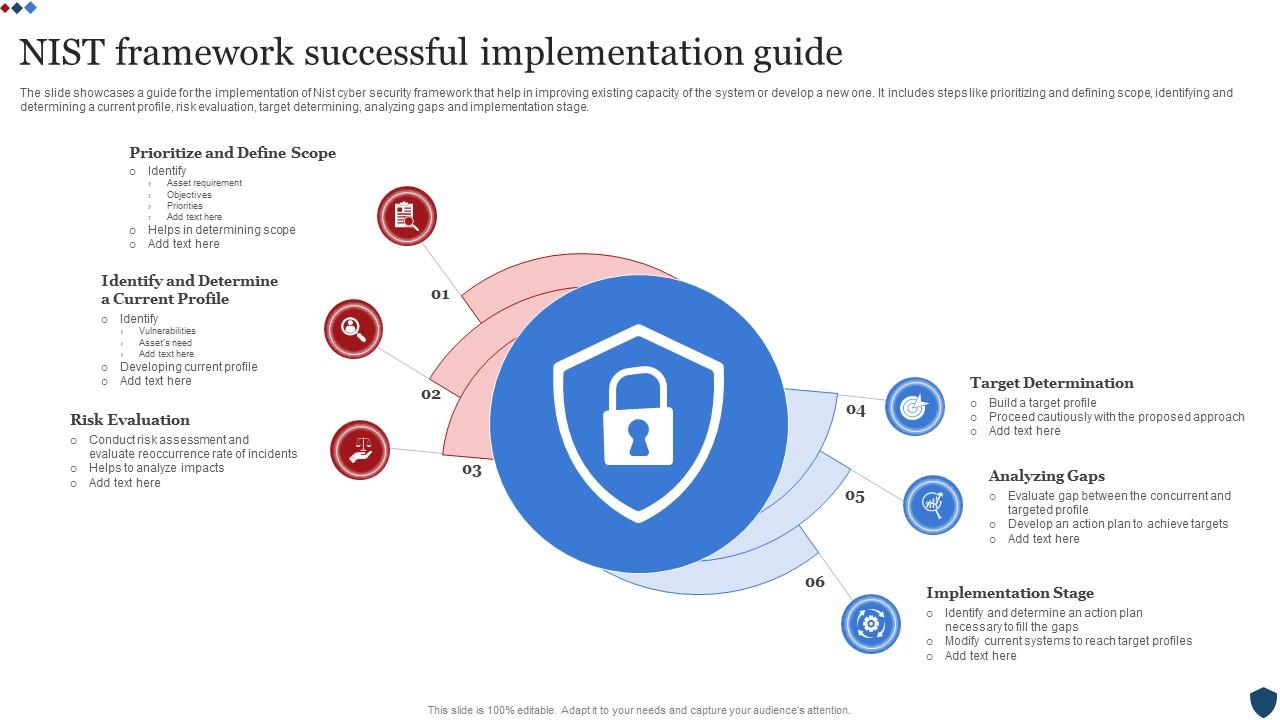
Nist Framework Successful Implementation Guide Abstract. the nist cybersecurity framework (csf) 2.0 can help organizations manage and reduce their cybersecurity risks as they start or improve their cybersecurity program. the csf outlines specific outcomes that organizations can achieve to address risk. The framework is organized by five key functions– identify, protect, detect, respond, recover. these five widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time. the activities listed under each function may offer a good starting point for your organization:.

Comments are closed.