Jamf Private Access Threat Defense Webinar

Jamf Private Access Threat Defense Webinar Youtube Jamf private access & threat defensethe webinar was recorded before jnuc 2021. the name wandera is no longer included in the product names but the same great. The technology that drives security. jamf threat defense (protect): the mobile threat defense (mtd) focuses on protecting endpoints from security threats, both on device and in network and supports managed unmanaged mobile oses, such as ios & android. jamf data policy (manage): this service focuses on managing data usage outside of the perimeter.

Webinar A Deep Dive Into Jamf Private Access Datajar Jamf’s latest software acquisitions jamf threat defense*, jamf data policy* and jamf private access* are security focused offerings that protect devices, users and data from malware and security threats. additionally, they allow you to achieve & maintain compliance while securing network communications based on powerful, zero trust. Jamf connect now includes the capabilities of jamf private access zero trust network access (ztna). jamf protect now includes the capabilities of jamf threat defense and jamf data policy. while jamf has always been and still is apple first, our device and os capabilities for our security products include android and windows. With more and more organizations moving data to the cloud, accessing that cloud data from mobile devices is critical to enable productivity from anywhere. however, enabling this access can greatly expand cybersecurity risks for organizations. to help protect against today’s cyberattacks, mobile threat defense is a critical aspect of data and. Jamf defends the users, devices and applications that keep your business running. it can cover compatible smartphones, tablets, jetpack devices and laptops, and it provides a unified analytics and policy engine that lets you configure policy once and apply it everywhere. from rapid deployments to single pane of glass administration, the.
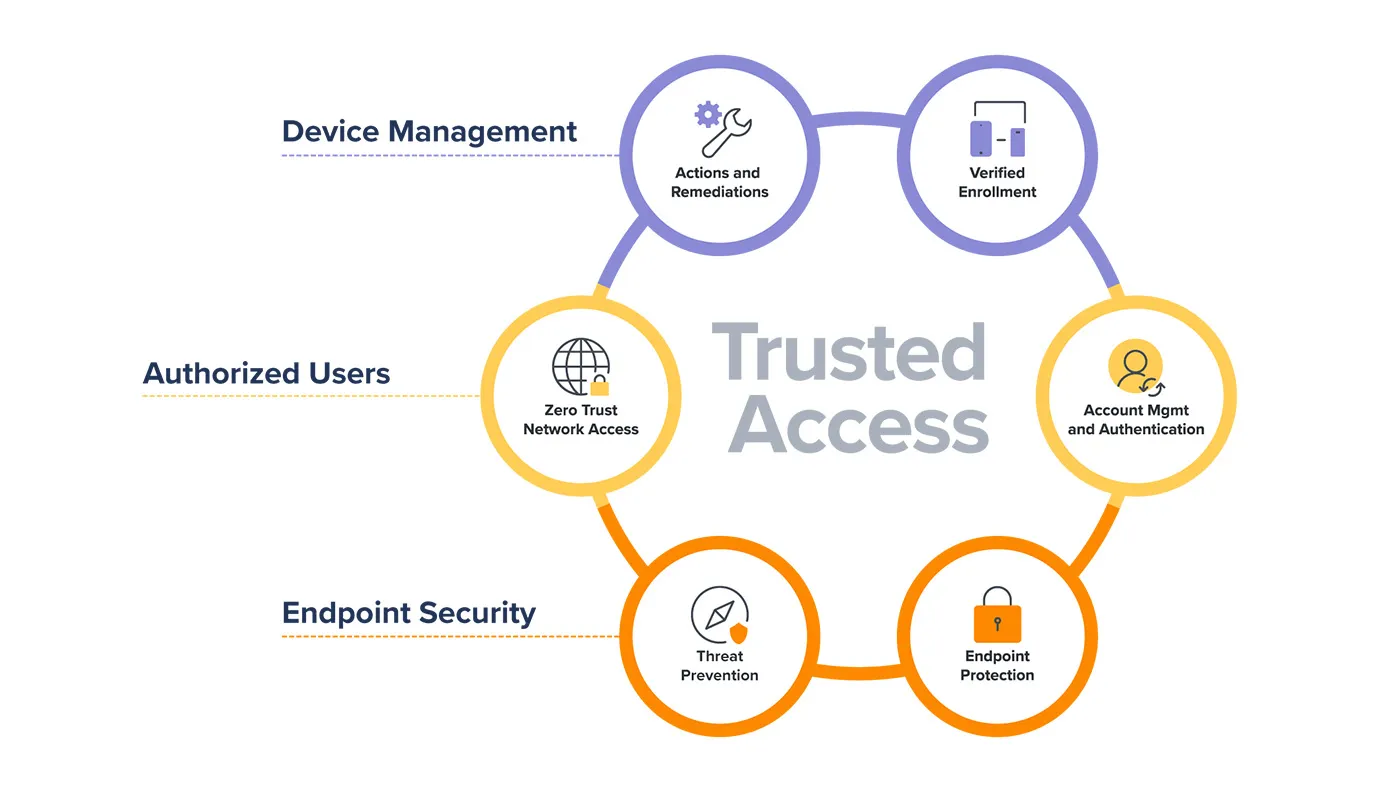
Meet Trusted Access Endpoint Security And Mobile Threat Defense From Jamf With more and more organizations moving data to the cloud, accessing that cloud data from mobile devices is critical to enable productivity from anywhere. however, enabling this access can greatly expand cybersecurity risks for organizations. to help protect against today’s cyberattacks, mobile threat defense is a critical aspect of data and. Jamf defends the users, devices and applications that keep your business running. it can cover compatible smartphones, tablets, jetpack devices and laptops, and it provides a unified analytics and policy engine that lets you configure policy once and apply it everywhere. from rapid deployments to single pane of glass administration, the. Jamf also announced the launch of jamf trust, an intuitive app for employees that powers workflows related to jamf’s security products, including jamf threat defense, jamf safe internet, jamf data policy, and jamf private access. jamf trust will give users access to powerful security capabilities without impacting device performance or. Jamf also announces the launch of jamf trust, an intuitive app for employees that powers workflows related to jamf’s security products, including jamf threat defense, jamf safe internet, jamf data policy, and jamf private access. jamf trust will give users access to powerful security capabilities without impacting performance or productivity.

Jamf Threat Defense Jamf Data Policy Jamfのモバイルセキュリティ製品 Jamf also announced the launch of jamf trust, an intuitive app for employees that powers workflows related to jamf’s security products, including jamf threat defense, jamf safe internet, jamf data policy, and jamf private access. jamf trust will give users access to powerful security capabilities without impacting device performance or. Jamf also announces the launch of jamf trust, an intuitive app for employees that powers workflows related to jamf’s security products, including jamf threat defense, jamf safe internet, jamf data policy, and jamf private access. jamf trust will give users access to powerful security capabilities without impacting performance or productivity.

Comments are closed.