It Security Risk Assessment Template
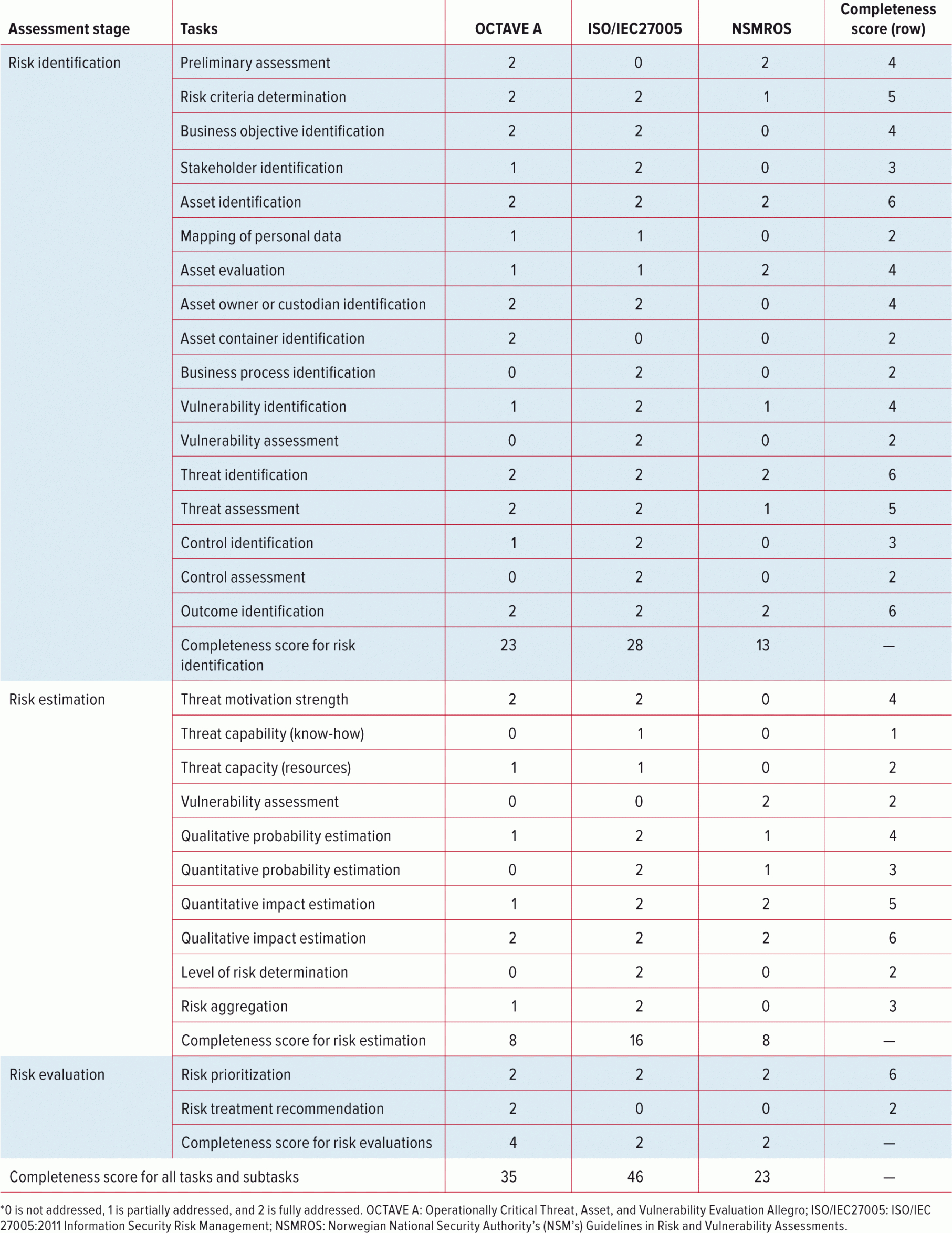
Security Risk Assessment Checklist Template Download and customize various templates for it risk assessment and management, such as checklists, matrices, policies, plans, and questionnaires. learn how to use these templates and access more resources and tips from it experts. Download and customize various templates for cybersecurity risk assessment, report, checklist, mitigation plan, and breakdown structure. learn how to apply iso 27001, nist cybersecurity framework, and other standards to your infosec strategy.

It Security Risk Assessment Template Download and customize these templates in pdf, word, or google docs formats to identify and mitigate cyber risks. learn how to use them effectively and efficiently for your organization or business. Learn the steps and methods to identify, estimate, and prioritize cyber risks to your organization's information systems and data. download a free pdf guide and a vendor risk assessment template from upguard. 2. nist cybersecurity framework (csf) risk assessment template. the nist cybersecurity framework is intended to simplify any security assessment and governance process. it is based on many international practices and standards, including nist 800 53 and iso 27001. A comprehensive template to help you identify, evaluate and mitigate it security risks. it covers tasks such as defining the scope, identifying assets, threats, vulnerabilities, impacts, strategies, and more.
Free 11 Sample It Risk Assessment Templates In Pdf Ms Word Excel 2. nist cybersecurity framework (csf) risk assessment template. the nist cybersecurity framework is intended to simplify any security assessment and governance process. it is based on many international practices and standards, including nist 800 53 and iso 27001. A comprehensive template to help you identify, evaluate and mitigate it security risks. it covers tasks such as defining the scope, identifying assets, threats, vulnerabilities, impacts, strategies, and more. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Learn about three templates for conducting a comprehensive cybersecurity risk assessment based on cis, nist and iso frameworks. compare the features, benefits and drawbacks of each template and how to choose the right one for your organization.
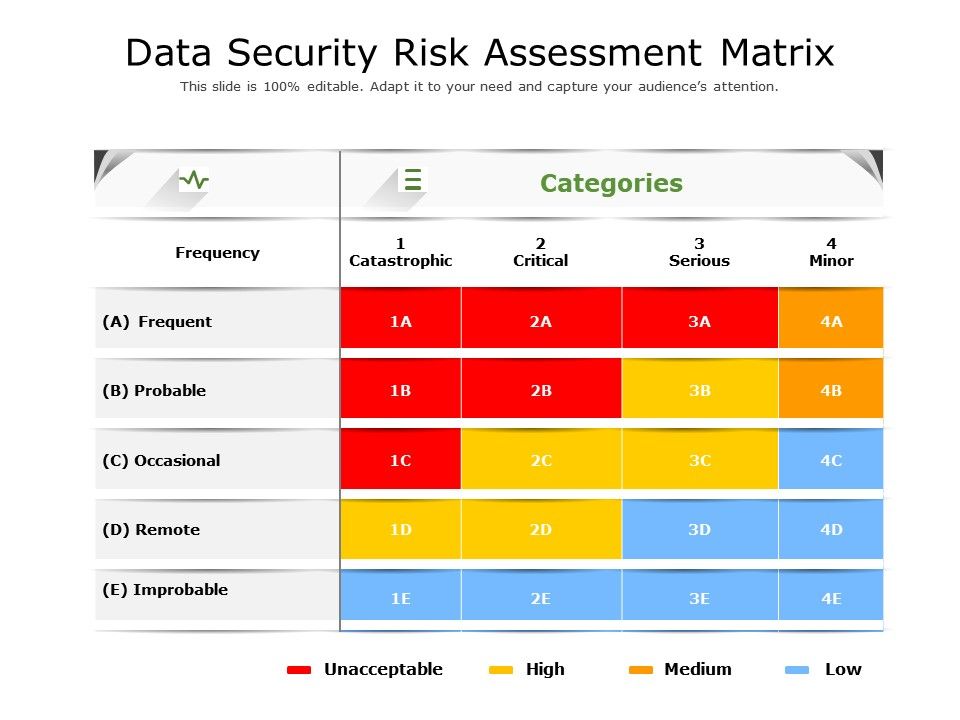
It Security Risk Assessment Template Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Learn about three templates for conducting a comprehensive cybersecurity risk assessment based on cis, nist and iso frameworks. compare the features, benefits and drawbacks of each template and how to choose the right one for your organization.

Comments are closed.