Ipex Internet Protocol Encapsulation Of X In Undefined By

Ipex Internet Protocol Encapsulation Of X In Undefined By Describe the issue i'm getting an undefined symbol issue when trying to load ipex with oneapi 2024.0. is this a known issue? (venv) (base) [bbrock@pcl pvc01 pytorch pvc]$ python c "import torch; import intel extension for pytorch as ipe. You signed in with another tab or window. reload to refresh your session. you signed out in another tab or window. reload to refresh your session. you switched accounts on another tab or window.
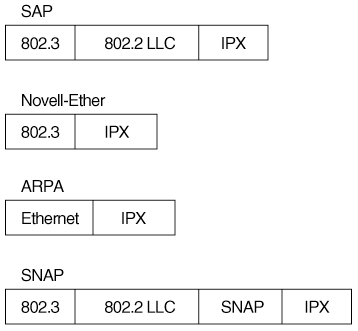
Configuring Ipx Addresses Cisco Router Configuration 2nd Edition Over the past few years, the number of rfcs that define and use ipsec and internet key exchange (ike) has greatly proliferated. this is complicated by the fact that these rfcs originate from numerous ietf working groups: the original ipsec wg, its various spin offs, and other wgs that use ipsec and or ike to protect their protocols' traffic. this document is a snapshot of ipsec and ike. Encapsulation is the computer networking process of concatenating layer specific headers or trailers with a service data unit (i.e. a payload) for transmitting information over computer networks. [2][3][4] deencapsulation (or de encapsulation) is the reverse computer networking process for receiving information; it removes from the protocol. Ipsec protocols. ah and or esp are the two protocols that we use to actually protect user data. both of them can be used in transport or tunnel mode, let’s walk through all the possible options. authentication header protocol. ah offers authentication and integrity but it doesn’t offer any encryption. Ipsec (internet protocol security) includes protocols for establishing mutual authentication between agents at the beginning of a session and negotiating cryptographic keys to be used during the session. it is widely used in virtual private networks (vpns), enabling secure data transmission over unsecured networks by creating encrypted tunnels.

Ipe 定义 互联网协议 Encapsulator Internet Protocol Encapsulator Ipsec protocols. ah and or esp are the two protocols that we use to actually protect user data. both of them can be used in transport or tunnel mode, let’s walk through all the possible options. authentication header protocol. ah offers authentication and integrity but it doesn’t offer any encryption. Ipsec (internet protocol security) includes protocols for establishing mutual authentication between agents at the beginning of a session and negotiating cryptographic keys to be used during the session. it is widely used in virtual private networks (vpns), enabling secure data transmission over unsecured networks by creating encrypted tunnels. Ity of service by the internet. it includes discussions on the implementation of mechanisms of traffic differentiators and policy and traffic policers and regu lators. the discussion includes diffserv, intserv, and a combination of both as developed by recent research. chapter 7 describes ip multicast and anycast. Generally, encapsulation is a process by which a lower layer protocol receives data from a higher layer protocol and then places the data into the data portion of its frame. thus, encapsulation is the process of enclosing one type of packet using another type of packet. encapsulation at the lowest levels of the open systems interconnection (osi.

Ip In Ip Encapsulation Ultimate Guide Ity of service by the internet. it includes discussions on the implementation of mechanisms of traffic differentiators and policy and traffic policers and regu lators. the discussion includes diffserv, intserv, and a combination of both as developed by recent research. chapter 7 describes ip multicast and anycast. Generally, encapsulation is a process by which a lower layer protocol receives data from a higher layer protocol and then places the data into the data portion of its frame. thus, encapsulation is the process of enclosing one type of packet using another type of packet. encapsulation at the lowest levels of the open systems interconnection (osi.

Comments are closed.