Implementing An Information Security Standard Step By Step Guide

Implementing An Information Security Standard Step By Step Guide Are you looking to implement iso iec 27001 for your organization? watch our detailed guide to prepare your business for successful implementation. learn abou. Introduction the iso 27001 process involves a series of steps, from establishing the context of the organization to conducting risk assessments and implementing controls. iso 27001 is an internationally recognized standard for information security management systems. implementing this standard is crucial for organizations looking to protect their sensitive data and minimize cyber risks.

Implementing Information Security Based On Iso 27001 Iso 27002 A Step 4: define the isms scope. the next step is to gain a broader sense of the isms’s framework. this process is outlined in clauses 4 and 5 of the iso 27001 standard. this step is crucial in defining the scale of your isms and the level of reach it will have in your day to day operations. as such, you must recognise everything relevant to. Od that is used to modify or manage an information security risk. they can include things like practices, processes, policies, procedures, programs, tools, techniques, technologies, devices, and organizational str. ctures. they are determined during the process of risk treatme. y be used.key requirements of iso iec 27001:2022c. Iso 27001 implementation checklist (free pdf download) catherine chipeta. updated oct 02, 2024. download the pdf guide. free trial. iso iec 27001, commonly referred to as iso 27001, is the most widely adopted international standard for managing data security and information security through an information security management system (isms). Each iso 27001 implementation needs to start with the following steps: obtaining management support. setting up project management. defining the isms scope. writing a top level information security policy. defining the risk assessment methodology. performing risk assessment and risk treatment.
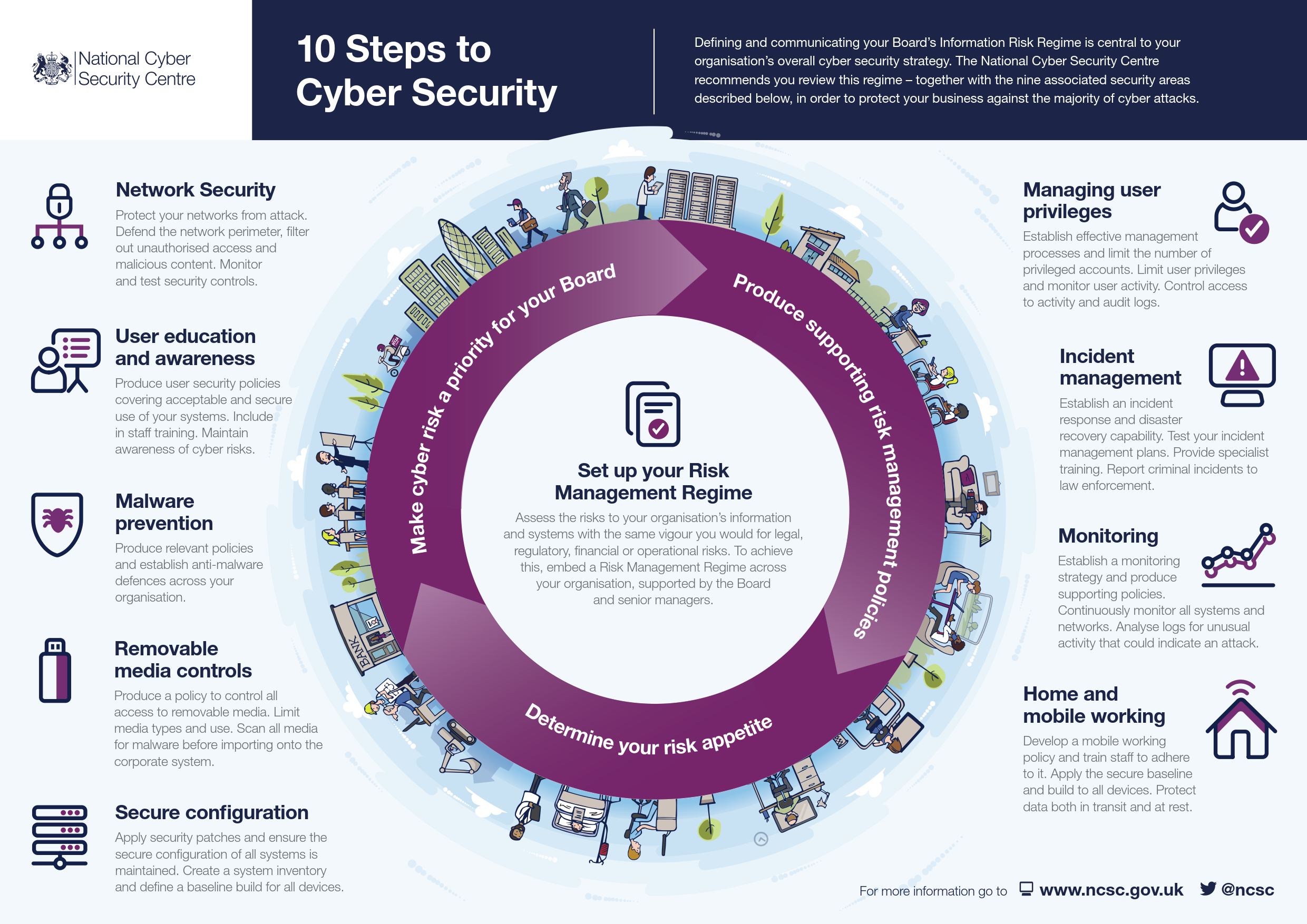
Infographic Ten Steps To Cyber Security Safety4sea Iso 27001 implementation checklist (free pdf download) catherine chipeta. updated oct 02, 2024. download the pdf guide. free trial. iso iec 27001, commonly referred to as iso 27001, is the most widely adopted international standard for managing data security and information security through an information security management system (isms). Each iso 27001 implementation needs to start with the following steps: obtaining management support. setting up project management. defining the isms scope. writing a top level information security policy. defining the risk assessment methodology. performing risk assessment and risk treatment. This blog explains our tried and tested, nine step approach to implementing iso 27001: (this is the methodology we’ve used to help more than 800 organisations around the world achieve compliance with the standard!) 1. project mandate. the implementation project should begin by appointing a project leader. Create your organisation overview. document internal external issues and interested parties. decide and document the iso 27001 scope. record the laws and regulations that apply to your business. document and control physical and virtual assets. document and record your data assets.

Comments are closed.