Ids E Ips

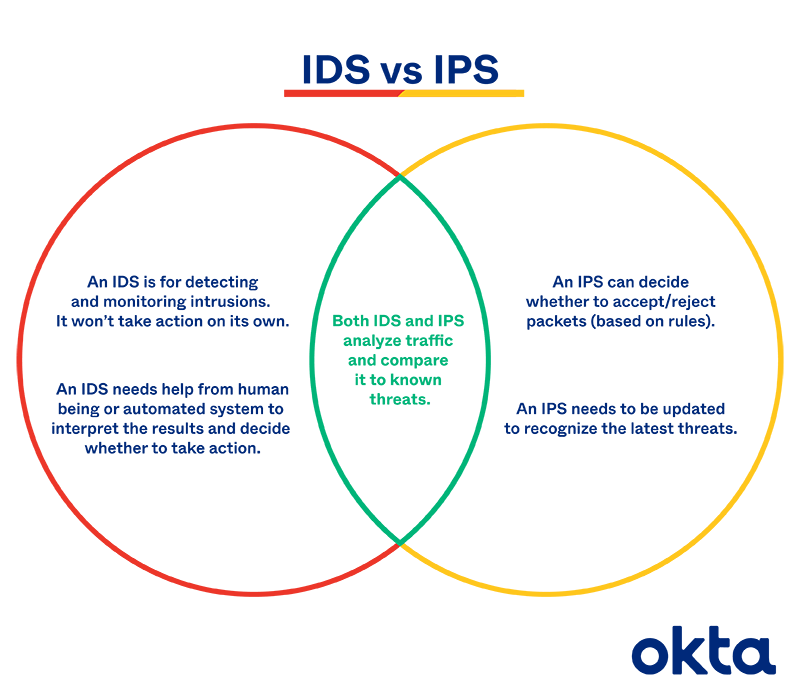
Ids Vs Ips What S The Difference And Why You Need Them Ids vs. ips vs. firewall faqs. the firewall, ips, and ids differ in that the firewall acts as a filter for traffic based on security rules, the ips actively blocks threats, and the ids monitors and alerts on potential security breaches. a firewall sets the boundaries for network traffic, blocking or allowing data based on predetermined protocols. An intrusion detection system (ids) monitors traffic on your network, analyzes that traffic for signatures matching known attacks, and when something suspicious happens, you're alerted. in the meantime, the traffic keeps flowing. an intrusion prevention system (ips) also monitors traffic. but when something unusual happens, the traffic stops.
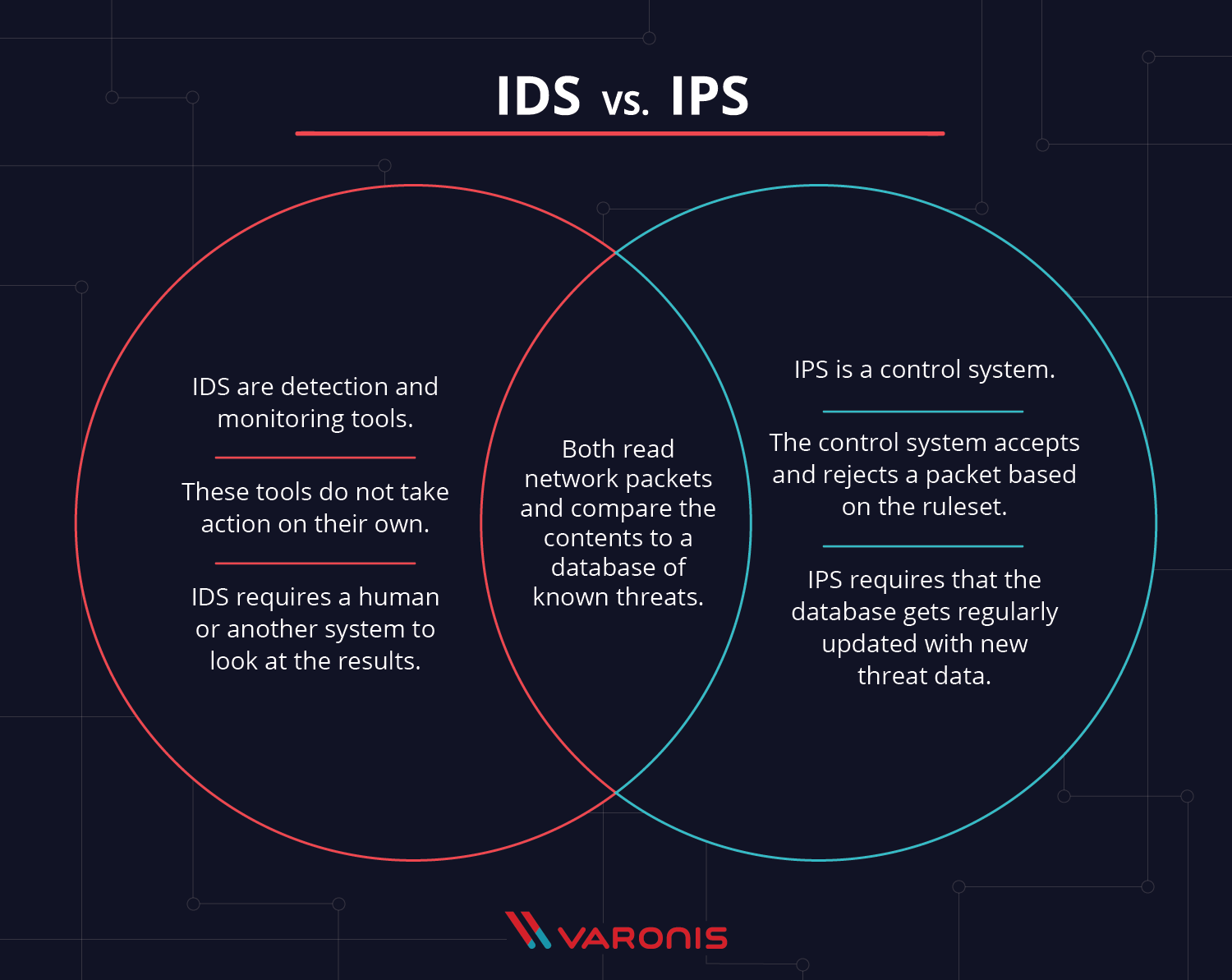
Ids Et Ips En Quoi Sont Ils Différents Functionality: ids tools are restricted to detecting threats, while ips tools can both detect and prevent them. response: ids tools send alerts when a threat is detected, while ips tools can automatically block threats based on predefined security policies or rules. workflow: ids tools passively monitor data flow, while ips tools actively. An intrusion detection system (ids) is responsible for identifying attacks and techniques and is often deployed out of band in a listen only mode so that it can analyze all traffic and generate intrusion events from suspect or malicious traffic. an intrusion prevention system (ips) is deployed in the path of traffic so that all traffic must. An intrusion prevention system (ips) is an active security system that detects potential threats and takes automated actions to prevent or block them in real time. ips uses the same techniques as ids, such as signature based detection, anomaly detection, and heuristics, to identify threats. when an ips identifies a malicious or unauthorized. The difference in ids and ips deployments is most distinguishable in their network based types, i.e., nids and nips. nids sensors are normally deployed in passive mode, while nips sensors are normally deployed inline. an ids requires security staff to act on its detections, whereas an ips can act autonomously.
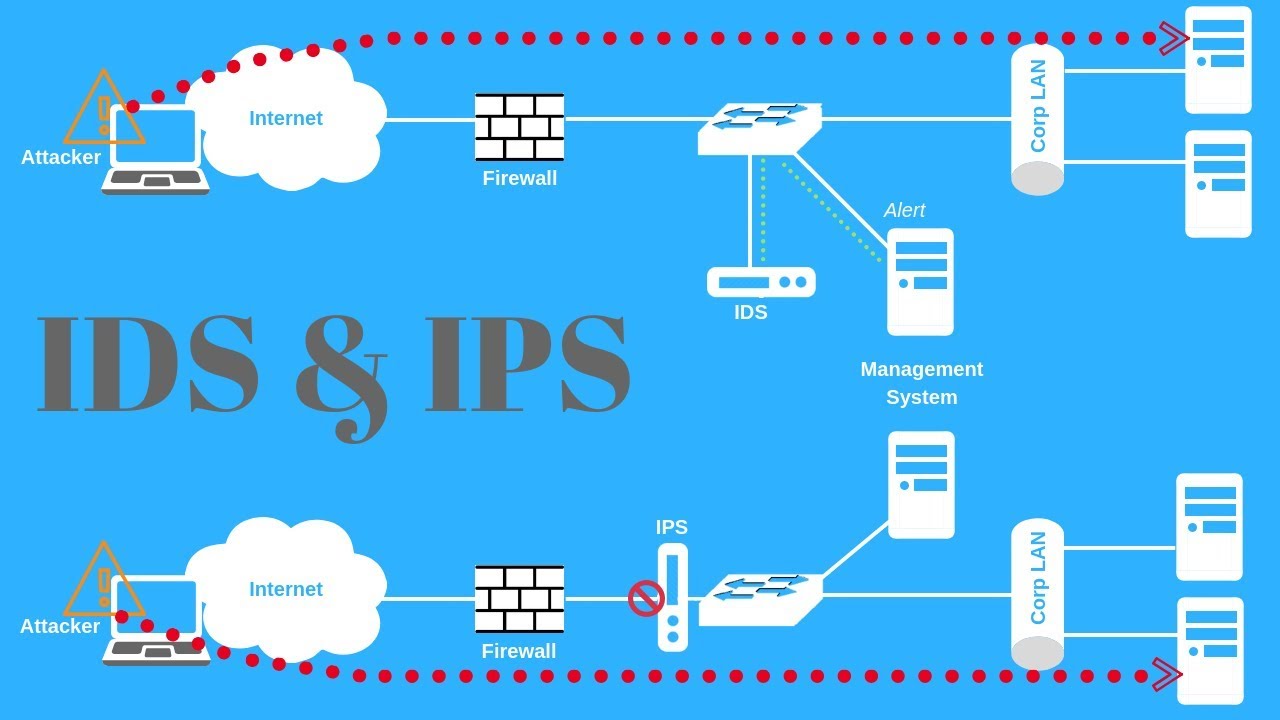
Ids Vs Ips Key Differences Rule Structure Pros And Cons An intrusion prevention system (ips) is an active security system that detects potential threats and takes automated actions to prevent or block them in real time. ips uses the same techniques as ids, such as signature based detection, anomaly detection, and heuristics, to identify threats. when an ips identifies a malicious or unauthorized. The difference in ids and ips deployments is most distinguishable in their network based types, i.e., nids and nips. nids sensors are normally deployed in passive mode, while nips sensors are normally deployed inline. an ids requires security staff to act on its detections, whereas an ips can act autonomously. An intrusion detection system (ids) is designed to monitor network traffic for suspicious or malicious activities. we can divide it into two types. network based ids (nids) and host based ids (hids). Ips can detect threats and stop attacks in real time. historically, ips ids only reacted to cyber breaches, but today ips is a key component of full network security suites, including threat monitoring, firewalls, intrusion detection, antivirus, antimalware, ransomware prevention, spam detection, and security analytics.
Ips Vs Ids The Difference Between Intrusion Prevention And Detection An intrusion detection system (ids) is designed to monitor network traffic for suspicious or malicious activities. we can divide it into two types. network based ids (nids) and host based ids (hids). Ips can detect threats and stop attacks in real time. historically, ips ids only reacted to cyber breaches, but today ips is a key component of full network security suites, including threat monitoring, firewalls, intrusion detection, antivirus, antimalware, ransomware prevention, spam detection, and security analytics.
Ips Vs Ids Top Essential Differences Of Ips Vs Ids In Network Security
Ids Vs Ips Definitions Comparisons Why You Need Both Okta

Comments are closed.