How To Configure Palo Alto Site To Site Vpn Using Ipsec Getlabsdone
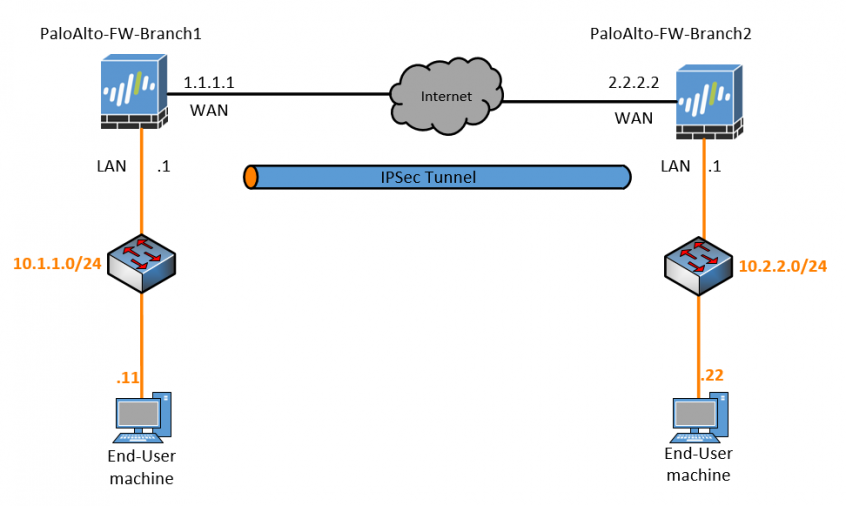
How To Configure Palo Alto Site To Site Vpn Using Ipsec Getlabsdone Let’s go ahead and create the tunnel interface and connect the tunnel interface to the ipsec zone. on the same network tab, click on interfaces and click on tunnel tab. click on the add button to create a new tunnel. in the virtual router, you can add your virtual router and the zone which we have created. To set up site to site vpn: make sure that your ethernet interfaces, virtual routers, and zones are configured properly. for more information, see configure interfaces and zones. create your tunnel interfaces. ideally, put the tunnel interfaces in a separate zone, so that tunneled traffic can use different policy rules.
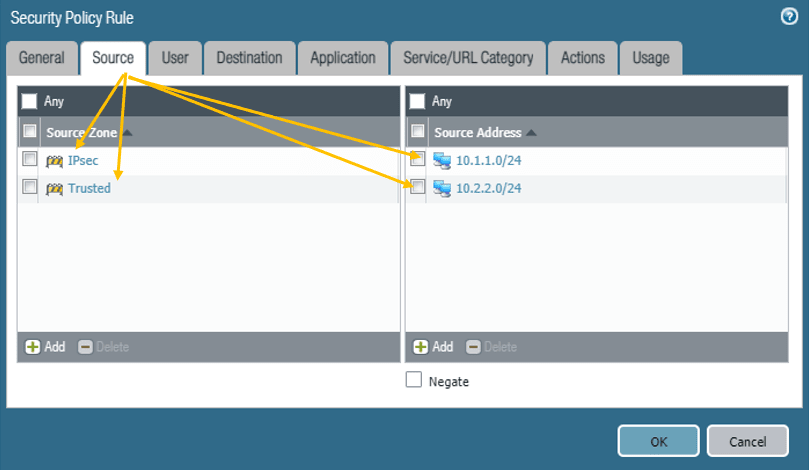
How To Configure Palo Alto Site To Site Vpn Using Ipsec Getlabsdone For communication between two sites, we will have to add a static route on the paloalto to send the traffic to the asa firewall ipsec tunnel. virtual router > default > static routes. ipv4, click on add to add the routes. name: to site1 asa. Strata cloud manager. prisma access (panorama managed) select networkipsec tunnels and then add a new tunnel configuration. on the general tab, enter a name for the tunnel. select the tunnel interface on which to set up the ipsec tunnel. to create a new tunnel interface: select tunnel interface new tunnel interface. Site to site vpn configuration examples. enforce security rule description, tag, and audit comment. move or clone a security rule or object to a different virtual system. configure your environment to access an external dynamic list. configure your environment to access an external dynamic list from the edl hosting service. Finally create the tunnel interface, which will also act as bgp interface for the ipsec tunnels, so we need to also configure an ip address. so i am going to use the link local address 169.254.1.0 30 for the first tunnel and 169.254.2.0 30 for the second tunnel. click on interfaces > tunnel.
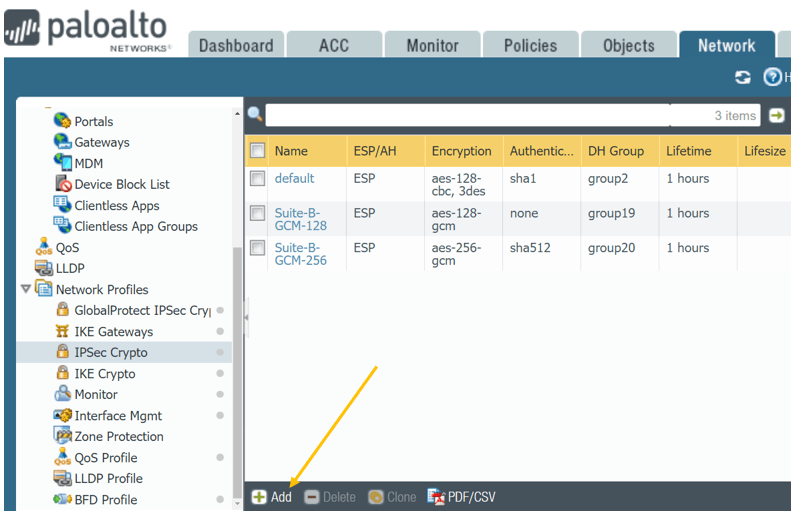
How To Configure Palo Alto Site To Site Vpn Using Ipsec Getlabsdone Site to site vpn configuration examples. enforce security rule description, tag, and audit comment. move or clone a security rule or object to a different virtual system. configure your environment to access an external dynamic list. configure your environment to access an external dynamic list from the edl hosting service. Finally create the tunnel interface, which will also act as bgp interface for the ipsec tunnels, so we need to also configure an ip address. so i am going to use the link local address 169.254.1.0 30 for the first tunnel and 169.254.2.0 30 for the second tunnel. click on interfaces > tunnel. Step 5. under network > ipsec tunnels, click add to create a new ipsec tunnel. in the general window use the tunnel interface, the ike gateway and ipsec crypto profile from above to set up the parameters to establish ipsec vpn tunnels between firewalls. note: if the other side of the tunnel is a peer that supports policy based vpn, you must. Select the tunnel interface, the ike gateway, and the ipsec crypto profile to make sure the proxy id is added, otherwise phase 2 will not come up. route add the route of the internal network of the other side pointing towards the tunnel interface and select none:.

Comments are closed.