Figure 1 From Detection Of Individual Anomalous Arrival Trajectories

Figure 1 From Detection Of Individual Anomalous Arrival Trajectories Figure 1. toy example of anomalous trajectory with in air holding "detection of individual anomalous arrival trajectories within the terminal airspace using persistent homology". However, the detection of isolated anomalous trajectories within a large aviation data set is difficult through classical methods. we propose using tools from topological data analysis to identify.
Figure 1 From Anomaly Detection In Ship Trajectories Semantic Scholar 2.1 trajectory anomaly detection existing work for anomaly detection in trajectories can be grouped into two broad categories: heuristic based methods [5, 13, 17, 34, 41] and learning based methods [26,27]. heuristic based methods primarily rely on hand crafted features to represent normal routes and employ distance or density met. Insights into the individual’s behavior or preferences. thus, tra jectory anomaly detection is a pivotal problem in monitoring and analyzing abnormal patterns. detecting anomalous trajectories can reveal changes in daily routines and provide valuable information for policymakers. trajectory anomaly detection has been gaining attention re. (blue line), respectively. we can see that the trajectory t 1 (red dashed line) is an anomaly because it does not follow the normal routes r 1 and r 2. another case shown in figure 1 is that the normal trajectories between s 2 and d 2 usually follow r 3 and r 4 (solid lines), while an anomalous trajectory t 2 (red dashed line) switches its. In this paper, we propose a lightweight anomaly detection model specifically designed to detect anomalies in human trajectories. we propose a neural collaborative filtering approach to model and predict normal mobility. our method is de signed to model users’ daily patterns of life without requiring prior knowledge, thereby enhancing.
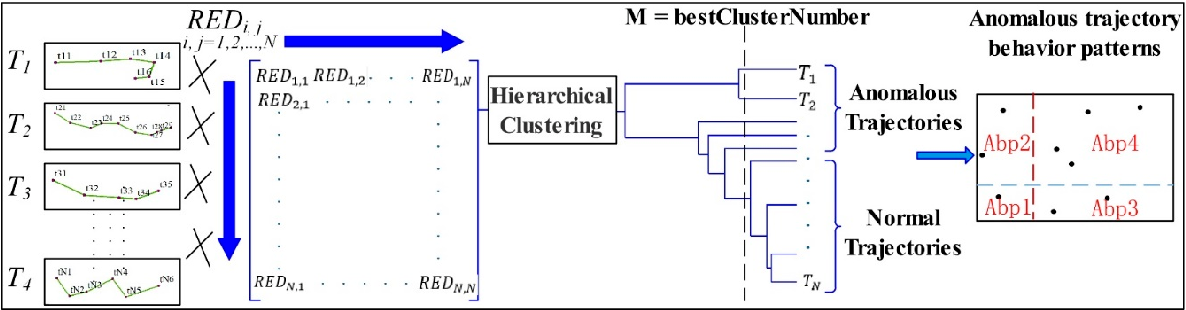
Figure 1 From Detecting Anomalous Trajectories And Behavior Patterns (blue line), respectively. we can see that the trajectory t 1 (red dashed line) is an anomaly because it does not follow the normal routes r 1 and r 2. another case shown in figure 1 is that the normal trajectories between s 2 and d 2 usually follow r 3 and r 4 (solid lines), while an anomalous trajectory t 2 (red dashed line) switches its. In this paper, we propose a lightweight anomaly detection model specifically designed to detect anomalies in human trajectories. we propose a neural collaborative filtering approach to model and predict normal mobility. our method is de signed to model users’ daily patterns of life without requiring prior knowledge, thereby enhancing. 4.2.1. performance evaluation on anomalous trajectory detection. we evaluate the results on od pair with the above baselines. taking the instance of od 2, the results of anomalous trajectory detection in od 2 are shown in figure 5. as shown in the figure, the mafrc atd model shows the highest detection rate under a given false alarm rate. Anomalous trajectory recognition problem in an open world scenario (atro), rather than traditional anomalous tra jectory detection (atd). however, atro is a challenging task due to the facts that: (1) as a trajectory is a collection containing massive gps points, multiple behavioral intents behind trajectories are unexplored, such as the.

Anomalous Trajectory Detection Example Download Scientific Diagram 4.2.1. performance evaluation on anomalous trajectory detection. we evaluate the results on od pair with the above baselines. taking the instance of od 2, the results of anomalous trajectory detection in od 2 are shown in figure 5. as shown in the figure, the mafrc atd model shows the highest detection rate under a given false alarm rate. Anomalous trajectory recognition problem in an open world scenario (atro), rather than traditional anomalous tra jectory detection (atd). however, atro is a challenging task due to the facts that: (1) as a trajectory is a collection containing massive gps points, multiple behavioral intents behind trajectories are unexplored, such as the.

Comments are closed.