Ethical Hacking Phases Design Jason Macleod Msc Jd Llm Cissp
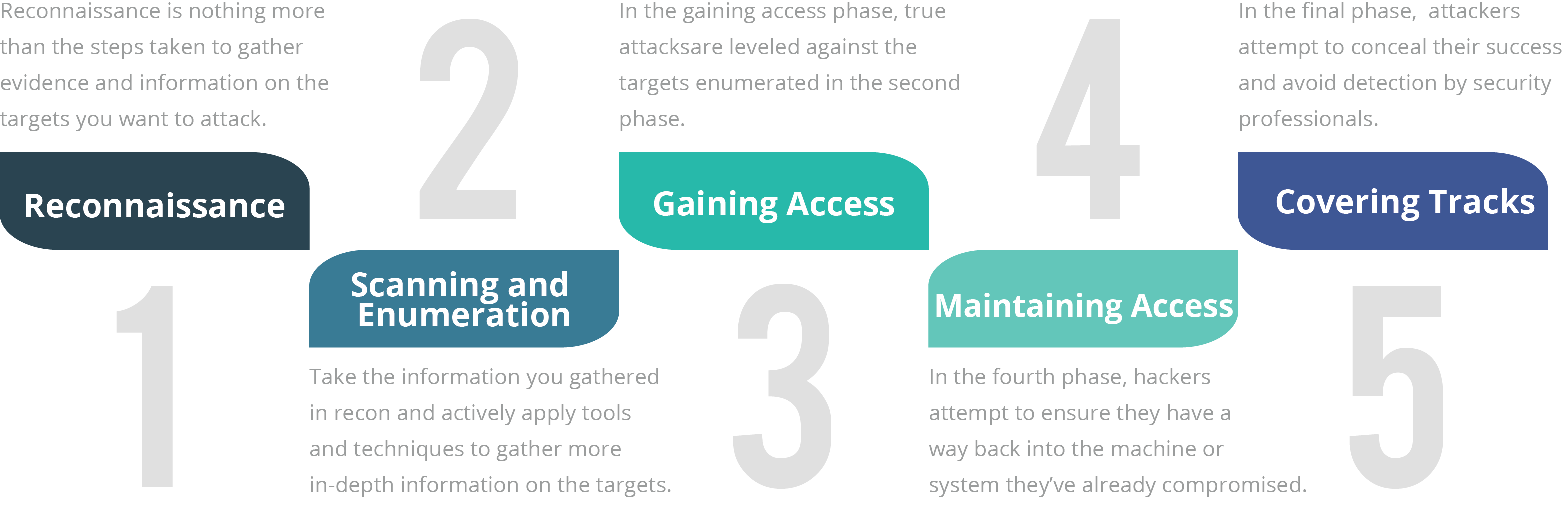
Ethical Hacking Phases Design Jason Macleod Msc Jd Llm Cissp Although there are many different terms for these phases and some of them run concurrently and continuously throughout a test, ec council has defined the standard hack as having five phases. whether the attacker is ethical or malicious, these five phases capture the full breadth of the attack. I am also a graduate of berkeley law (ll.m) and the university of oxford (msc). i am a member of the new hampshire bar, vermont bar, and the washington dc bar. i have been a visiting scholar at dartmouth college since 2021. read more about me here. listen to my dj mixes. (c) jason d. macleod 2022. the digital threat solutions specialist at.

Phases Of Ethical Hacking Hith Blog Hackerinthehouse View jason’s full profile. cyber @ city of bellevue | jd, msc, llm | cissp, ceh, cipp us · a magna cum laude graduate of the university of washington, with law degrees from berkeley law and. February 5, 2016 comments off on phases of ethical hacking jason macleod. ← previous image. next image → (c) jason d. macleod 2022. I am a member of the new hampshire bar, vermont bar, and the washington dc bar. i am an accomplished dj who has spun at over 250 events. visit my music site to listen to over 20 mixes. jason macleod | msc, jd, llm., cipp us, ceh, cissp | academic writing spanning political economy, climate change, critical race theory, postcolonial theory, intl. Tableau viz: global instances of violence (1989 2014) with 103,665 conflict entries, the uppsala conflict data program conflict map provides detailed info including exact location of each conflict.
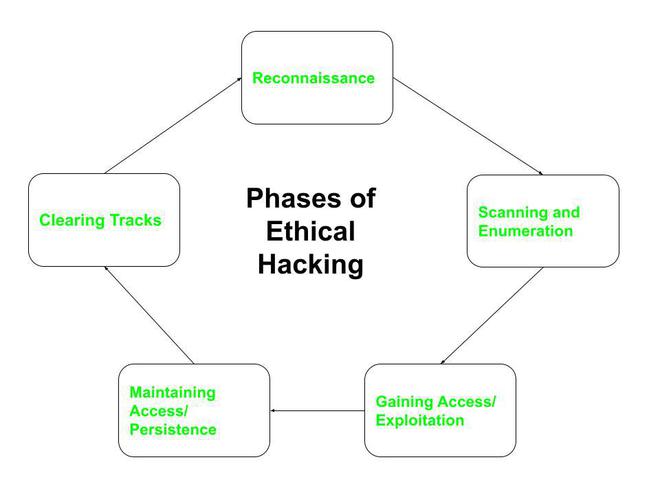
5 Phases Of Hacking Geeksforgeeks I am a member of the new hampshire bar, vermont bar, and the washington dc bar. i am an accomplished dj who has spun at over 250 events. visit my music site to listen to over 20 mixes. jason macleod | msc, jd, llm., cipp us, ceh, cissp | academic writing spanning political economy, climate change, critical race theory, postcolonial theory, intl. Tableau viz: global instances of violence (1989 2014) with 103,665 conflict entries, the uppsala conflict data program conflict map provides detailed info including exact location of each conflict. Marx, capitalism, globalization, and climate change: revolutionary ideas for climate change mitigation. this paper explores theories of marx, environmentalism, ecology, radical ecology, and anarchism. the paper critiques capitalist societies, production, consumption and waste patterns, and argues for a dramatic shift in society and being. Aquinas’ treatment on law shaped by reason and for the benefit of the common good reveals analogous contemporary principles and problems. he notes that ”the chief and main concern of law properly so called is the plan of the common good" and that interests of the individual are subordinate to this common good of the.
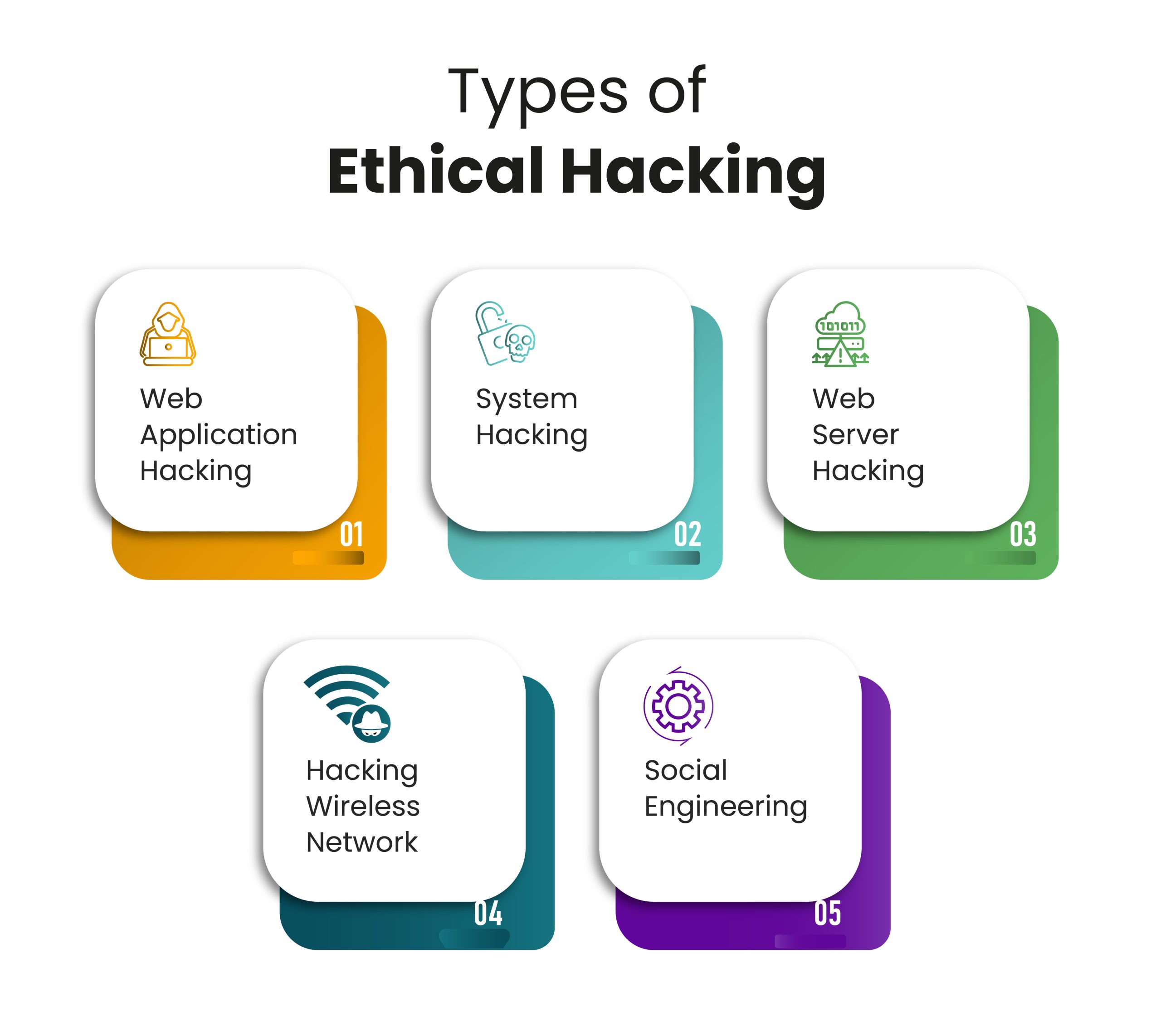
Phases Of Ethical Hacking Infosectrain Marx, capitalism, globalization, and climate change: revolutionary ideas for climate change mitigation. this paper explores theories of marx, environmentalism, ecology, radical ecology, and anarchism. the paper critiques capitalist societies, production, consumption and waste patterns, and argues for a dramatic shift in society and being. Aquinas’ treatment on law shaped by reason and for the benefit of the common good reveals analogous contemporary principles and problems. he notes that ”the chief and main concern of law properly so called is the plan of the common good" and that interests of the individual are subordinate to this common good of the.
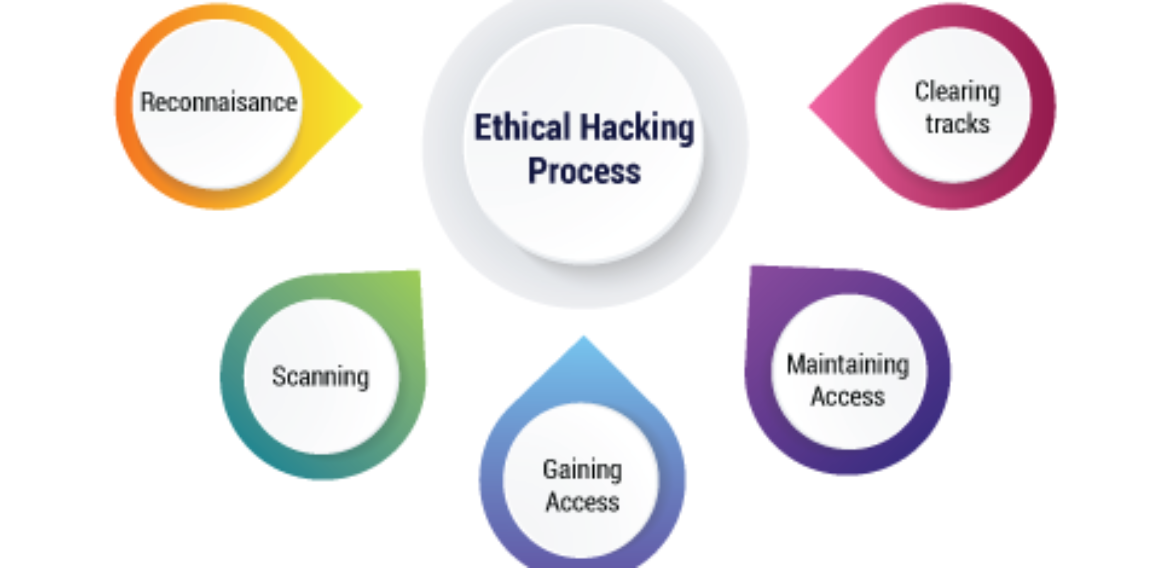
Phases Of Ethical Hacking A Complete Guide To Ethical Hacking Process

The Five Stages Of Ethical Hacking

Comments are closed.