Ethical Hacking Hacking Web Hacker How Hacking Actually Looks Like

Ethical Hacking Hacking Web Hacker How Hacking Actually Looks Like 4. bash scripting. bash is a command line interface language used to make instructions and requests to operating systems like linux. as a hacker, learning how to create bash scripts will help you harness the full power of the linux os by automating tasks and enabling you to work with tools. 5. When not building networks and researching the latest developments in network security, he can be found writing technical articles and blog posts at infosec resources and elsewhere. website. penetration testing and ethical hacking are often used interchangeably when people talk about networking and cybersecurity. currently, the demand for cyberse.
Hacking Vs Ethical Hacking Check Key Differences And Similarities An ethical hacker follows the steps and thought process of a malicious attacker to gain authorized access and test the organization’s strategies and network. an attacker or an ethical hacker follows the same five step hacking process to breach the network or system. the ethical hacking process begins with looking for various ways to hack into. White hat hacking. white hat hackers, also known as ethical hackers, use their computer skills for good. these hackers specialize in penetration testing, which is designed to expose serious flaws by pushing computer systems to their limits. more and more companies are employing white hats to catch security issues before black hats (malicious. Ethical hacking is the use of hacking techniques by friendly parties in an attempt to uncover, understand and fix security vulnerabilities in a network or computer system. ethical hackers have the same skills and use the same tools and tactics as malicious hackers, but their goal is always to improve network security without harming the network. An ethical hacker is a security expert who works to gain unauthorized access to a network, system, application, data, or device in an attempt to identify potential security vulnerabilities. ethical hacking is a means of finding and exploiting potential weak points in a computer network or system in order to fix these issues before a cyberattack.
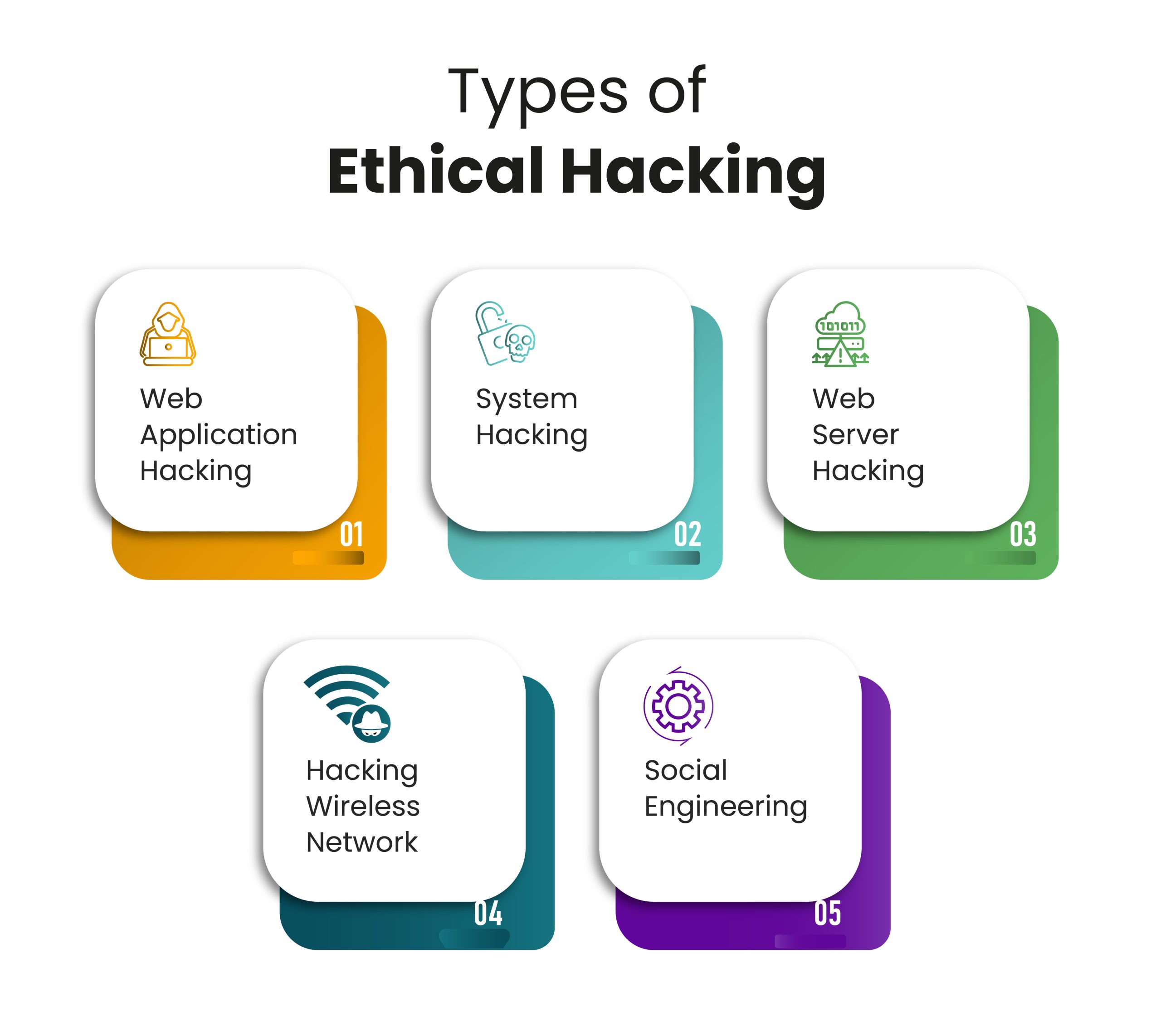
Phases Of Ethical Hacking Infosectrain Ethical hacking is the use of hacking techniques by friendly parties in an attempt to uncover, understand and fix security vulnerabilities in a network or computer system. ethical hackers have the same skills and use the same tools and tactics as malicious hackers, but their goal is always to improve network security without harming the network. An ethical hacker is a security expert who works to gain unauthorized access to a network, system, application, data, or device in an attempt to identify potential security vulnerabilities. ethical hacking is a means of finding and exploiting potential weak points in a computer network or system in order to fix these issues before a cyberattack. Although ethical hacking is a type of penetration testing, it uses attack simulations and methods to assess the system and network, reinforcing that there’s more to ethical hacking than just penetration testing. many ethical hackers need to be multifaced in not only thinking like a hacker but moving like one as well. The term ethical hacking, also called white hat hacking, refers to the use of hacking skills and techniques with good intentions and with the full consent and approval of the target. ethical hackers use their tools and knowledge to probe an it system, database, network, or application for security vulnerabilities.

Comments are closed.