Establishing An Effective Threat Management Program Part 3 Of 5
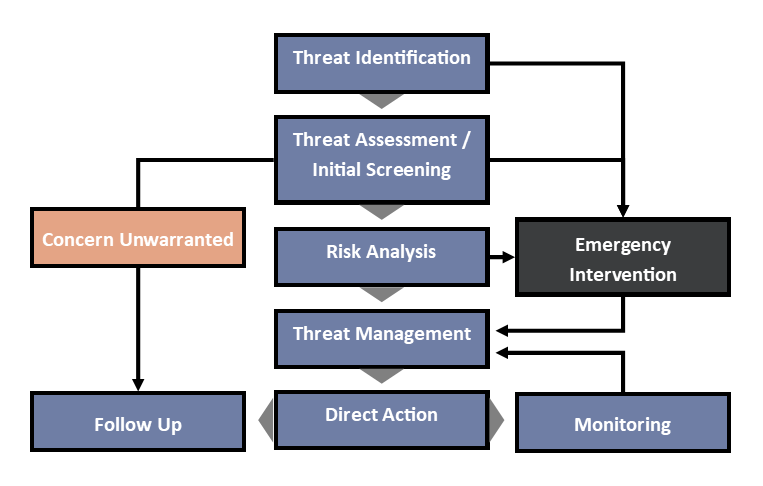
Establishing An Effective Threat Management Program Part 3 Of 5 Read the other parts of this 5 part series on developing your threat management program: part 1: defining and categorizing threats for your organization. part 2: designing the ability to properly detect a threat. part 4: best practices for threat management. part 5: building your threat management program. An effective threat management program: identifies and focuses on critical assets, personnel, data, and services that the organization defines as valuable. monitors the environment to detect and identify threats proactively. assesses threats to determine the individual level of risk within the identified areas of concern.

Establishing An Effective Threat Management Program Part 3 Of 5 Read the other parts of this 5 part series on developing your threat management program: part 1: defining and categorizing threats for your organization. part 2: designing the ability to properly detect a threat. part 3: properly assessing a threat and analyzing its risk. part 5: building your threat management program. Organizations; and the private sector establish or enhance an insider threat prevention and mitigation program. moreover, this guide accomplishes this objective in a scalable manner that considers the level of maturity and size of the organization. it also contains valuable measures for building and using effective threat management teams. By combing through industry frameworks and best practices, 1, 2, 3 more than 50 controls and components spanning program, technical and process topics can be identified (figure 1). a maturity analysis can show which processes and capabilities might already exist that can be tapped into as part of a cohesive insider threat program. Screen text: course objectives: identify the policies and standards that inform the establishment of an insider threat program. identify key challenges to detecting the insider threat. identify key steps to establishing an insider threat program. identify the minimum standards for insider threat programs and key resources for implementation.

Threat Management Security Solutions Optiv By combing through industry frameworks and best practices, 1, 2, 3 more than 50 controls and components spanning program, technical and process topics can be identified (figure 1). a maturity analysis can show which processes and capabilities might already exist that can be tapped into as part of a cohesive insider threat program. Screen text: course objectives: identify the policies and standards that inform the establishment of an insider threat program. identify key challenges to detecting the insider threat. identify key steps to establishing an insider threat program. identify the minimum standards for insider threat programs and key resources for implementation. A model critical multidisciplinary teams assessment and management to terrorism prevention the primary goal of tatm is to evaluate potential threats and employ threat management strategies to mitigate threat concerns related to an individual’s radicalization or mobilization to violence. highly effective teams collaborate, coordinate,. Introduction. this job aid gives department of defense (dod) staf and contractors an overview of the insider threat program requirements for industry as outlined in the national industrial security program operating manual (nispom) that became efective as a federal rule in accordance with 32 code of federal regulations part 117, also known as.

Comments are closed.