End Of Life Software Definition Risks Solutions
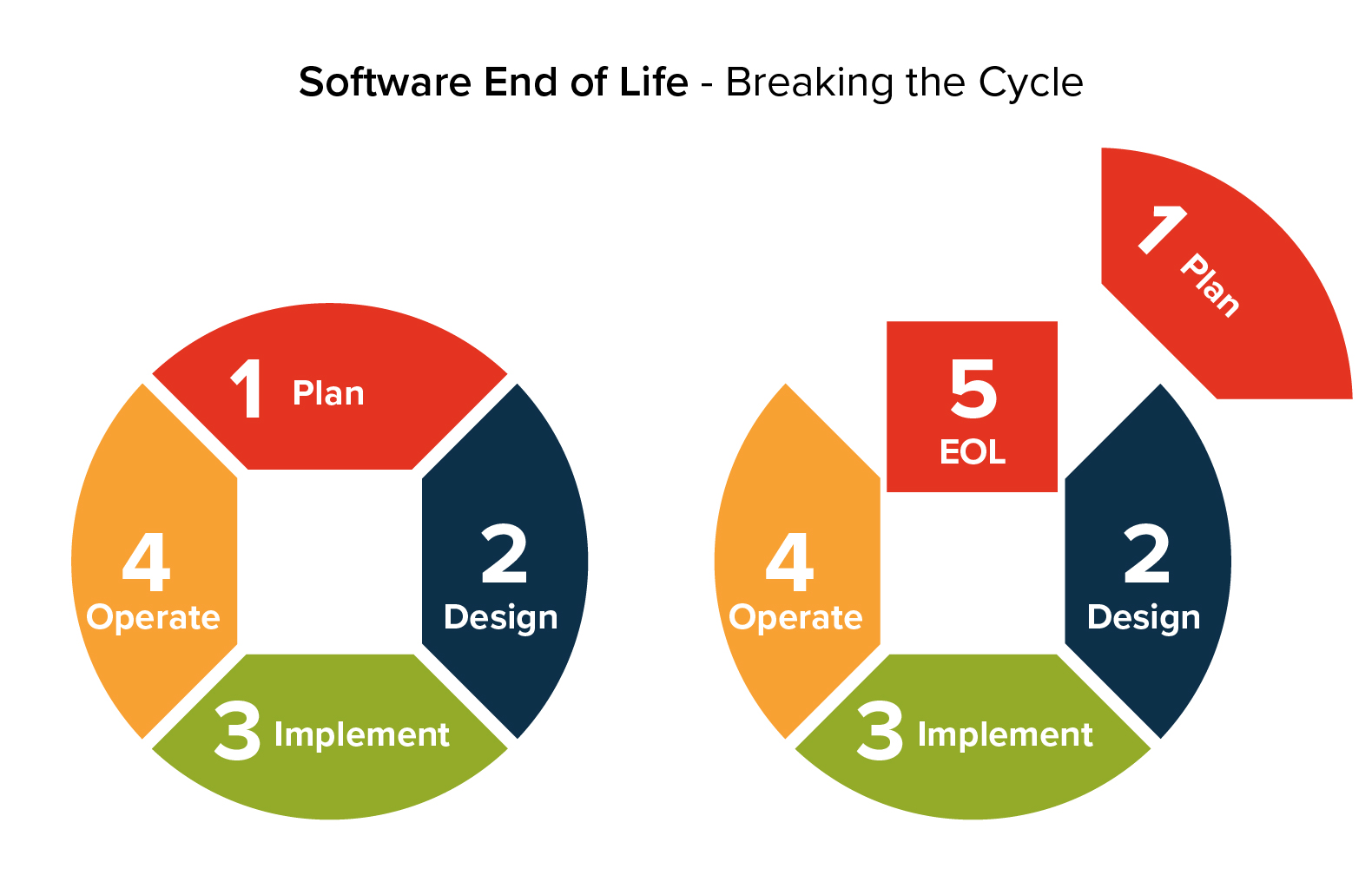
End Of Life Software Definition Risks Solutions 4 risks or issues using eol software. there are many serious risks you’re taking by using eol software: 1. data breach or injection. if you keep using eol software, you are risking being hacked since new security patches are not issued. if some hacker finds a way to exploit a particular vulnerability in your os, and the software developer is. Isolating end of life software protects your systems from security vulnerabilities and other risks. by restricting the access, you can reduce the surface layer of the attack, limiting the number of entry and exit points to a network or system. as a result, inbound and outbound traffic can be controlled more effectively.

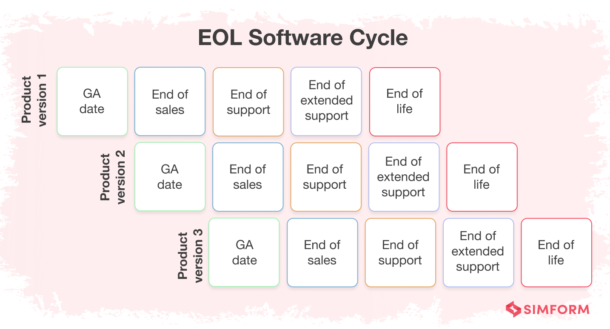
End Of Life Software Definition Risks Solutions End of life (eol) software is software that is no longer being supported or maintained by the vendor. this means that the vendor will not release any new security updates or bug fixes for the software. eol software can be a security risk, as it is more vulnerable to attack. it can also be difficult to maintain, as there may be no documentation. This blog post aims to shed light on the definition, risks, and solutions concerning eol software. what is end of life (eol)? eol marks a significant phase in the lifecycle of software or hardware, signifying the point at which the developer or company ceases to provide technical support, security patches, and updates. Understanding the risks of end of life software . software forms the backbone of business operations, and many risks associated with using end of life software exist. end of life software definition: software is deemed eol when it has reached the end of its support lifecycle (i.e., it no longer receives updates or support from its developers. End of life software can be a prominent obstacle to your business growth as it lacks integration and security capabilities. overcome eol software risks with a strategic plan, prioritizing critical systems, evaluating upgrade options, and engaging with software vendors. consider custom enterprise software development, cloud solutions, and.

End Of Life Software Definition Risks Solutions Understanding the risks of end of life software . software forms the backbone of business operations, and many risks associated with using end of life software exist. end of life software definition: software is deemed eol when it has reached the end of its support lifecycle (i.e., it no longer receives updates or support from its developers. End of life software can be a prominent obstacle to your business growth as it lacks integration and security capabilities. overcome eol software risks with a strategic plan, prioritizing critical systems, evaluating upgrade options, and engaging with software vendors. consider custom enterprise software development, cloud solutions, and. Risk of end of life software. the risks of using eol software are manifold and significant. security vulnerabilities are perhaps the most pressing concern, as any unpatched flaws become permanent weaknesses that threat actors can exploit. being in an eol state vastly force multiplies one’s potential attack surface vulnerability. Wannacry exploited windows xp’s end of life by using a vulnerability in the xp operating system. the attackers used a file called eternalblue, which allowed the malware to spread from system to system without user interaction. the malware then encrypted the user’s data and demanded a ransom, payable in bitcoin, to unlock it.
End Of Life Software Risks Dangers What To Do Next Ciso Street Risk of end of life software. the risks of using eol software are manifold and significant. security vulnerabilities are perhaps the most pressing concern, as any unpatched flaws become permanent weaknesses that threat actors can exploit. being in an eol state vastly force multiplies one’s potential attack surface vulnerability. Wannacry exploited windows xp’s end of life by using a vulnerability in the xp operating system. the attackers used a file called eternalblue, which allowed the malware to spread from system to system without user interaction. the malware then encrypted the user’s data and demanded a ransom, payable in bitcoin, to unlock it.
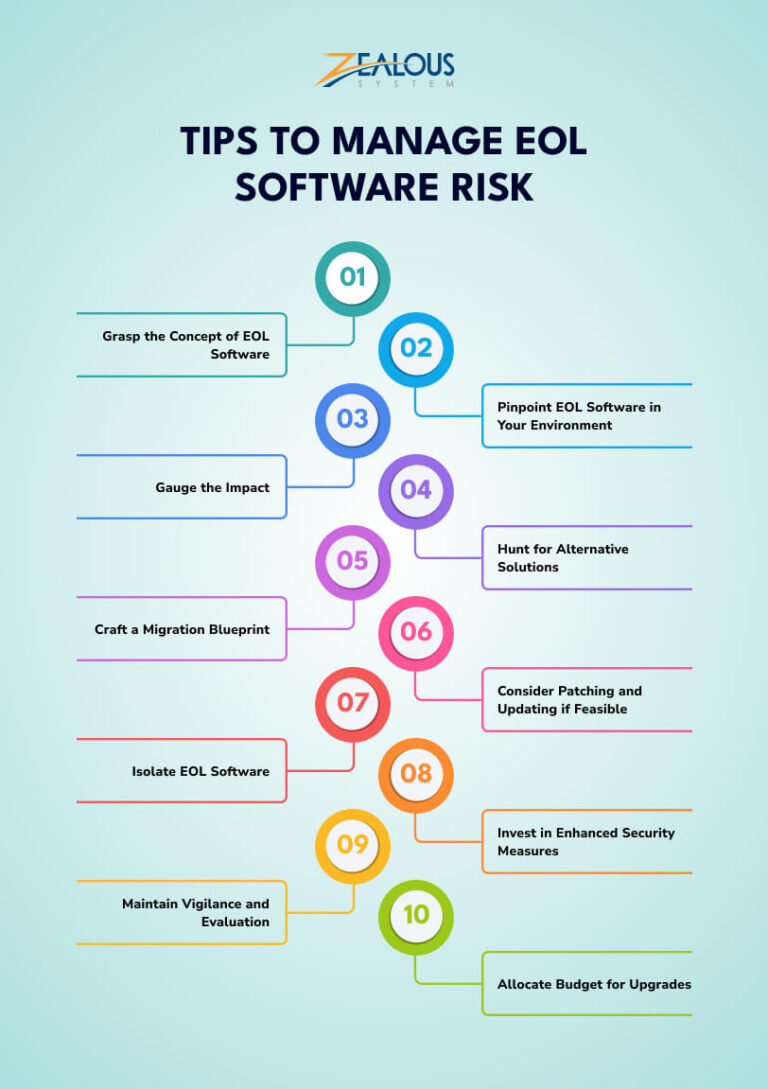
End Of Life Software Definition Examples Risks Strategies

Comments are closed.