Different Types Of Hackers More Details Are Explained Here

Different Types Of Hackers Explained 2024 The most common hacking techniques they will use include phishing, trojan horse, spyware, adware, brute force, identity theft, ransomware, man in the middle, logic bombs, clickjacking, denial of service, and so on. if you wonder about more information about white hat hackers and black hat hackers, you can read this article: [explained] white. Other types of hackers. there are generally 7 types of hackers, after the main 3 types, they are: script kiddies: they are the most dangerous people in terms of hackers. a script kiddie is an unskilled person who uses scripts or downloads tools available for hacking provided by other hackers.
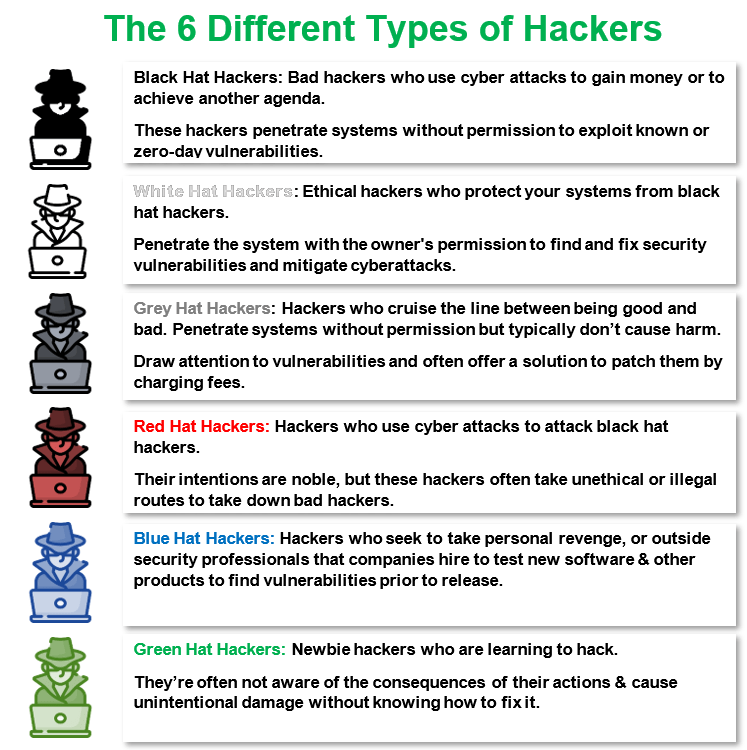
Different Types Of Hackers The 6 Hats Explained Infosec Insights That’s the crucial difference between a white hat vs a black hat hacker. black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of. Different types of hackers: the 6 hats explained. in cyber security. (75 votes, average: 4.77 out of 5) black hat, white hat, grey hat, red hat, blue hat, and green hat. no, these aren’t items in an apparel store’s catalog — they’re the different types of hackers you’ll find in the cybersecurity industry. the term “hacker” is. Understanding the different types of hackers is crucial for navigating the intricate landscape of cybersecurity. in this comprehensive guide, we will delve into the various categories of hackers, exploring what sets them apart and the impact they have on the digital world. 1. white hat hackers. white hat hackers, also known as ethical hackers. One of the most well known types of hackers is the white hat hacker. these individuals, also known as ethical hackers, use their skills to identify vulnerabilities in computer systems and networks in order to protect them from malicious attacks. on the other end of the spectrum, black hat hackers engage in illegal activities, exploiting.

Different Types Of Hackers More Details Are Explained Here Understanding the different types of hackers is crucial for navigating the intricate landscape of cybersecurity. in this comprehensive guide, we will delve into the various categories of hackers, exploring what sets them apart and the impact they have on the digital world. 1. white hat hackers. white hat hackers, also known as ethical hackers. One of the most well known types of hackers is the white hat hacker. these individuals, also known as ethical hackers, use their skills to identify vulnerabilities in computer systems and networks in order to protect them from malicious attacks. on the other end of the spectrum, black hat hackers engage in illegal activities, exploiting. Also known as threat actors, black hat hackers are the stereotypical cybercriminals who attempt to break into personal devices and networks using ransomware, spyware, phishing techniques, and other methods. the objective of black hat hacking is often to collect sensitive data to exploit or sell for profit. you may recall hearing about the nba. It combines with other attacks like code injection, network attacks, and malware to make the hack possible. there are various types of phishing attacks, such as email phishing, spear phishing, whaling, smishing, vishing, and angler phishing. also read: ways to avoid vishing attacks.

Hackers Explained Tech Precision Pty Ltd Also known as threat actors, black hat hackers are the stereotypical cybercriminals who attempt to break into personal devices and networks using ransomware, spyware, phishing techniques, and other methods. the objective of black hat hacking is often to collect sensitive data to exploit or sell for profit. you may recall hearing about the nba. It combines with other attacks like code injection, network attacks, and malware to make the hack possible. there are various types of phishing attacks, such as email phishing, spear phishing, whaling, smishing, vishing, and angler phishing. also read: ways to avoid vishing attacks.
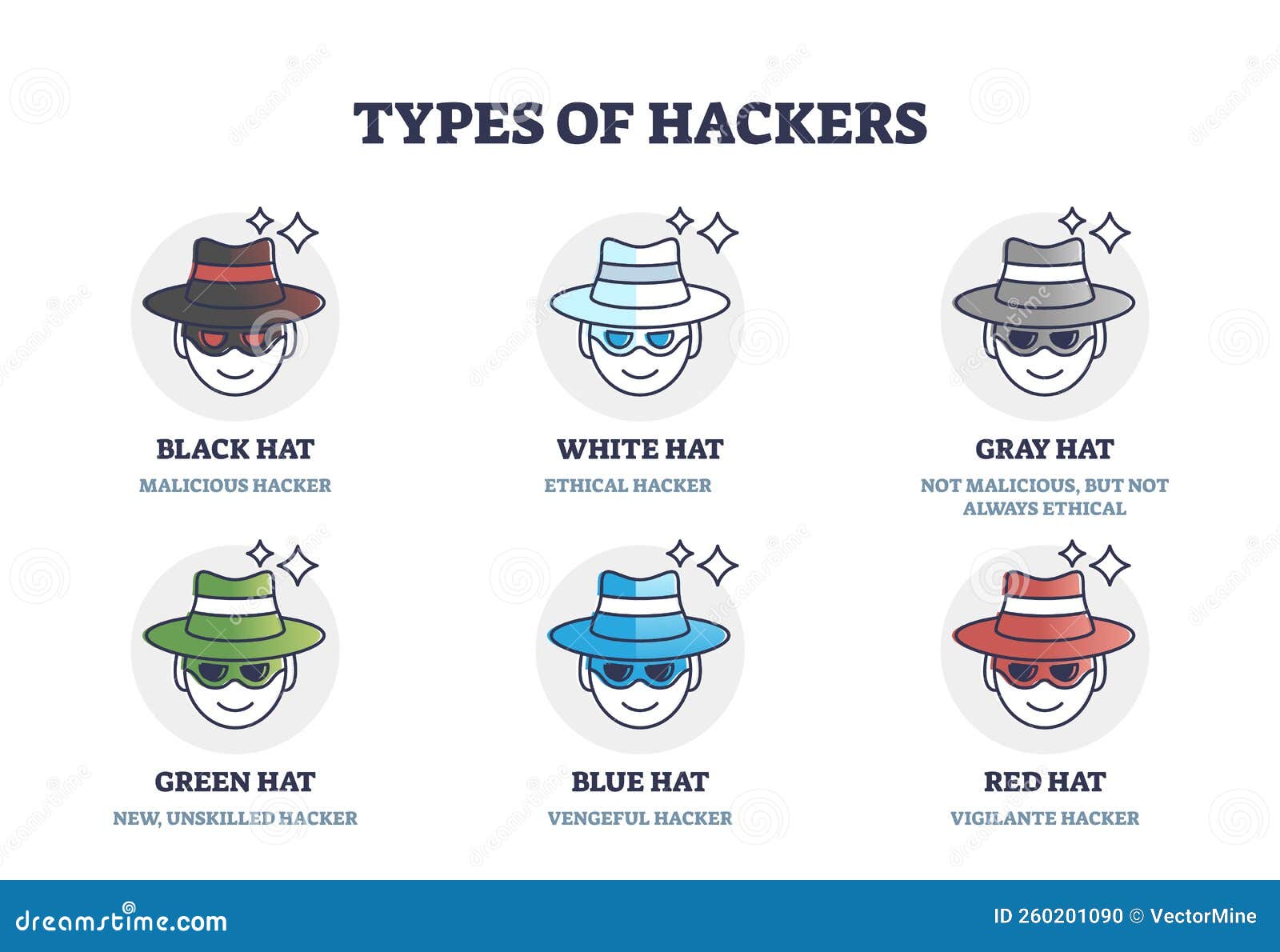
Types Of Hackers Description With Hat Color Classification Outline

Comments are closed.