Data Protection And Container Security In 5g Edge Deployments
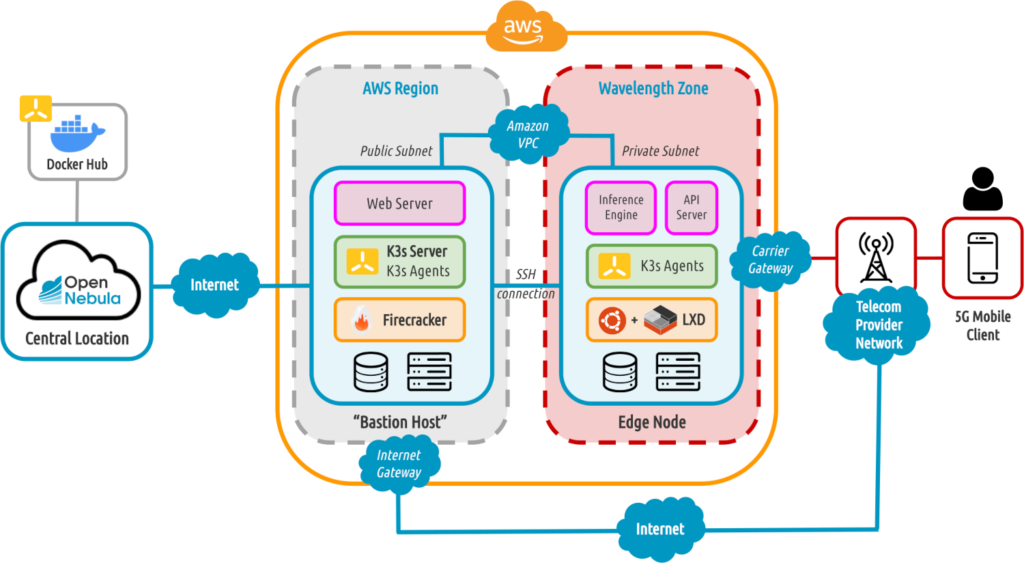
Building 5g Edge Clouds For Containers With Opennebula And Aws Wavelength 5g networks running on the edge will move applications and data closer to the user to reduce latency and improve performance, but these advancements will int. Heavy reading says the next largest growth segment will be the media and entertainment sector, with 66% of respondents indicating they would deploy 5g edge services to these verticals in the next two years. as the compiled data illustrates, the initial edge focus for service providers is to lower costs and increase performance.
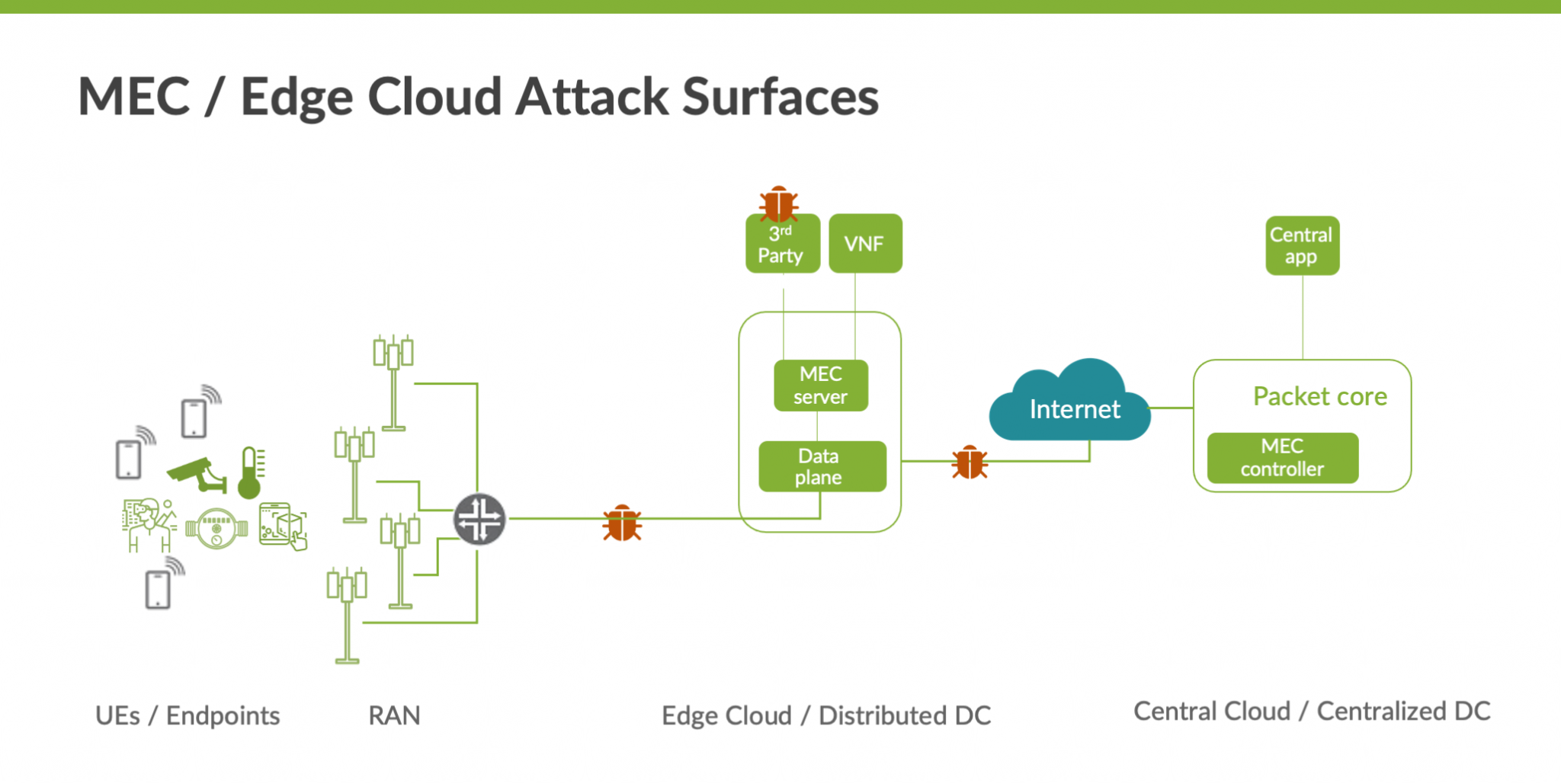
5g Edge Cloud And Multi Access Edge Computing Mec Security Official In this presentation, you’ll see how you can secure your far edge openshift environments and keep containerized data protected in 5g deployments. data protection and container security in 5g edge deployments. Multi access edge computing (mec) envisages such an edge computing platform. in this survey, we are revealing security vulnerabilities of key 5g based use cases deployed in the mec context. probable security flows of each case are specified, while countermeasures are proposed for mitigating them. User plane is a crucial piece of the puzzle, making it possible to have the higher levels of distribution required to address new use cases and enterprise requirements. for a successful 5g edge user plane journey, the new products must be fast to deploy and manage, allow for automation and have an extra degree of security and privacy. It is an opportunity to protect services and consumers from many of today’s threats. 5g comes with many built in security controls by design, developed to enhance the protection of both individual consumers and mobile networks; this is more efficient that post deployment add on or extras.
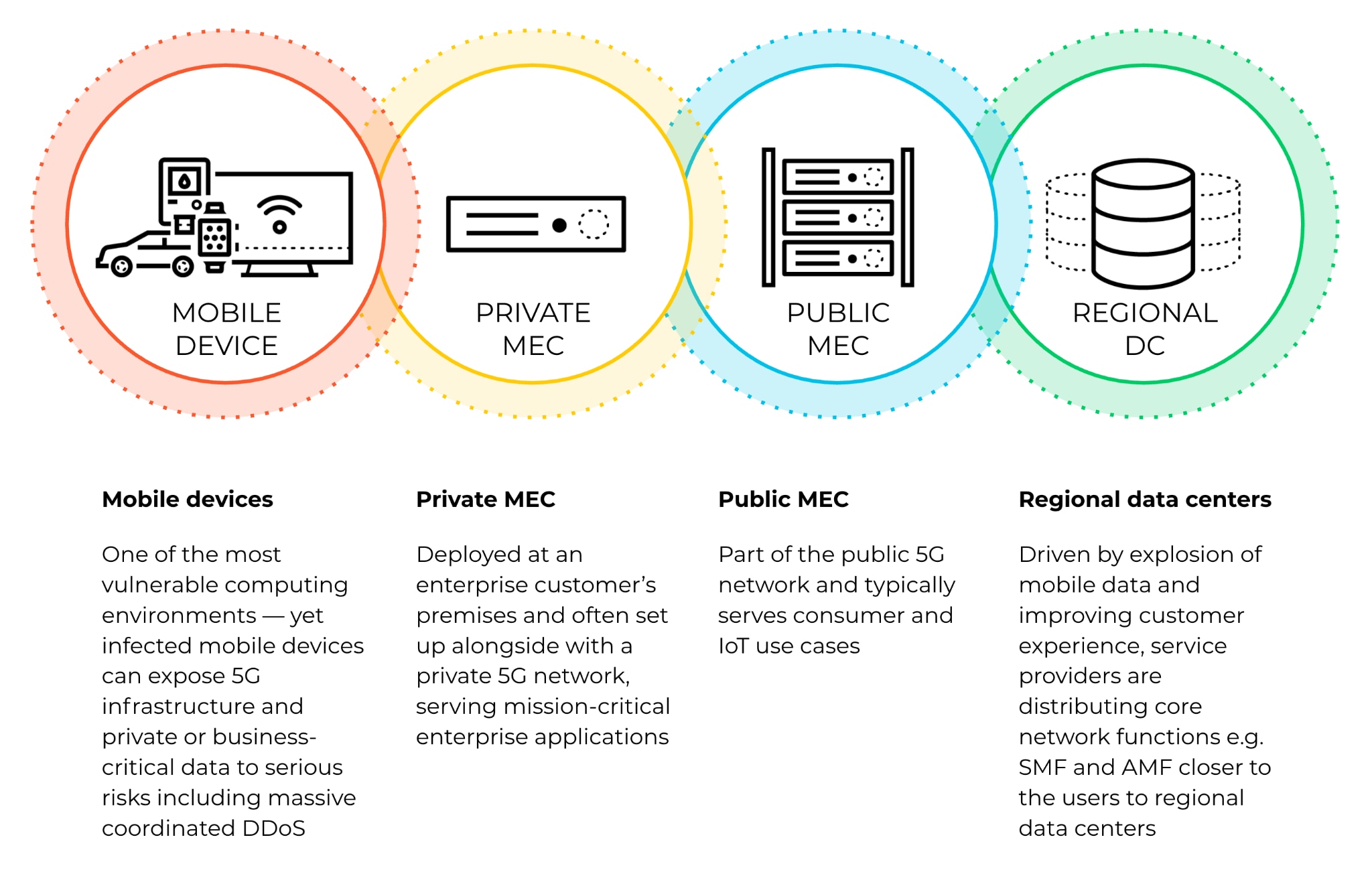
The Four 5g Edge Environments And How To Secure Them Palo Alto User plane is a crucial piece of the puzzle, making it possible to have the higher levels of distribution required to address new use cases and enterprise requirements. for a successful 5g edge user plane journey, the new products must be fast to deploy and manage, allow for automation and have an extra degree of security and privacy. It is an opportunity to protect services and consumers from many of today’s threats. 5g comes with many built in security controls by design, developed to enhance the protection of both individual consumers and mobile networks; this is more efficient that post deployment add on or extras. Mitigating risks in 5g mec security. according to a 2020 study from analysys mason, 87% of global respondents say edge computing is a strategic priority, and 5g rollouts are playing a role in driving that strategy. however, 80% are concerned about mobile edge computing 5g security, as well as the vulnerabilities in iot and mobile cloud. In 5g the control plane signaling data is encrypted via transport layer security (tls)9. work is underway within the gsma10 to define the implementation specifics for how tls is implemented in the control plane, and internet between networks. the algorithms required are specified by the 3gpp.11.
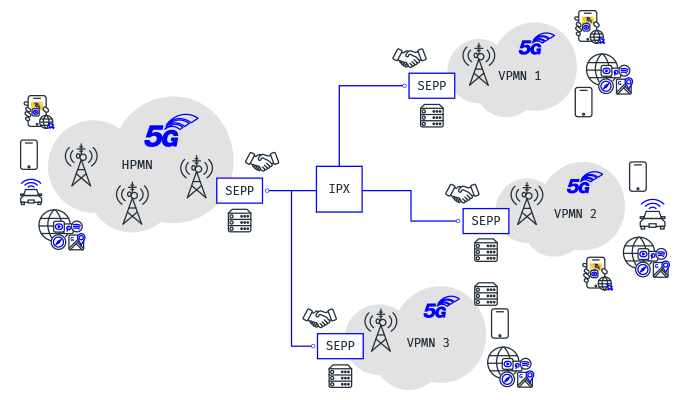
What Is 5g Security Edge Protection Proxy Sepp Moniem Tech Mitigating risks in 5g mec security. according to a 2020 study from analysys mason, 87% of global respondents say edge computing is a strategic priority, and 5g rollouts are playing a role in driving that strategy. however, 80% are concerned about mobile edge computing 5g security, as well as the vulnerabilities in iot and mobile cloud. In 5g the control plane signaling data is encrypted via transport layer security (tls)9. work is underway within the gsma10 to define the implementation specifics for how tls is implemented in the control plane, and internet between networks. the algorithms required are specified by the 3gpp.11.
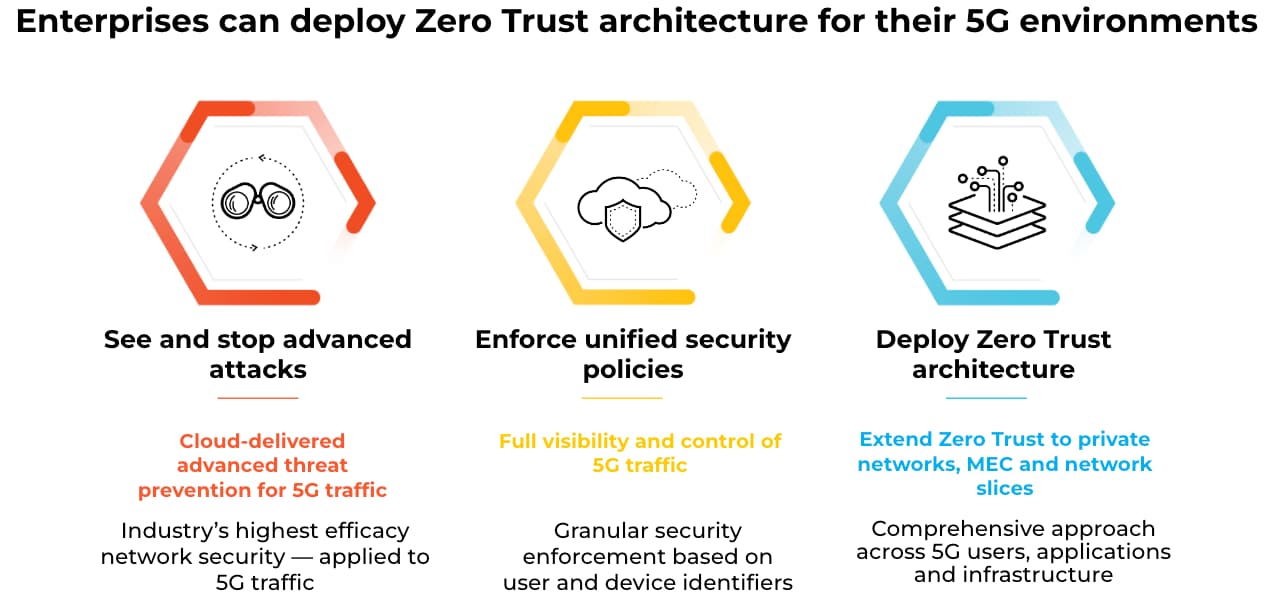
Securing 5g And Edge Computing Environments With Zero Trust

Exium Commercial Applications Intel Network Builders

Comments are closed.