Cybersecurity Architecture Networks
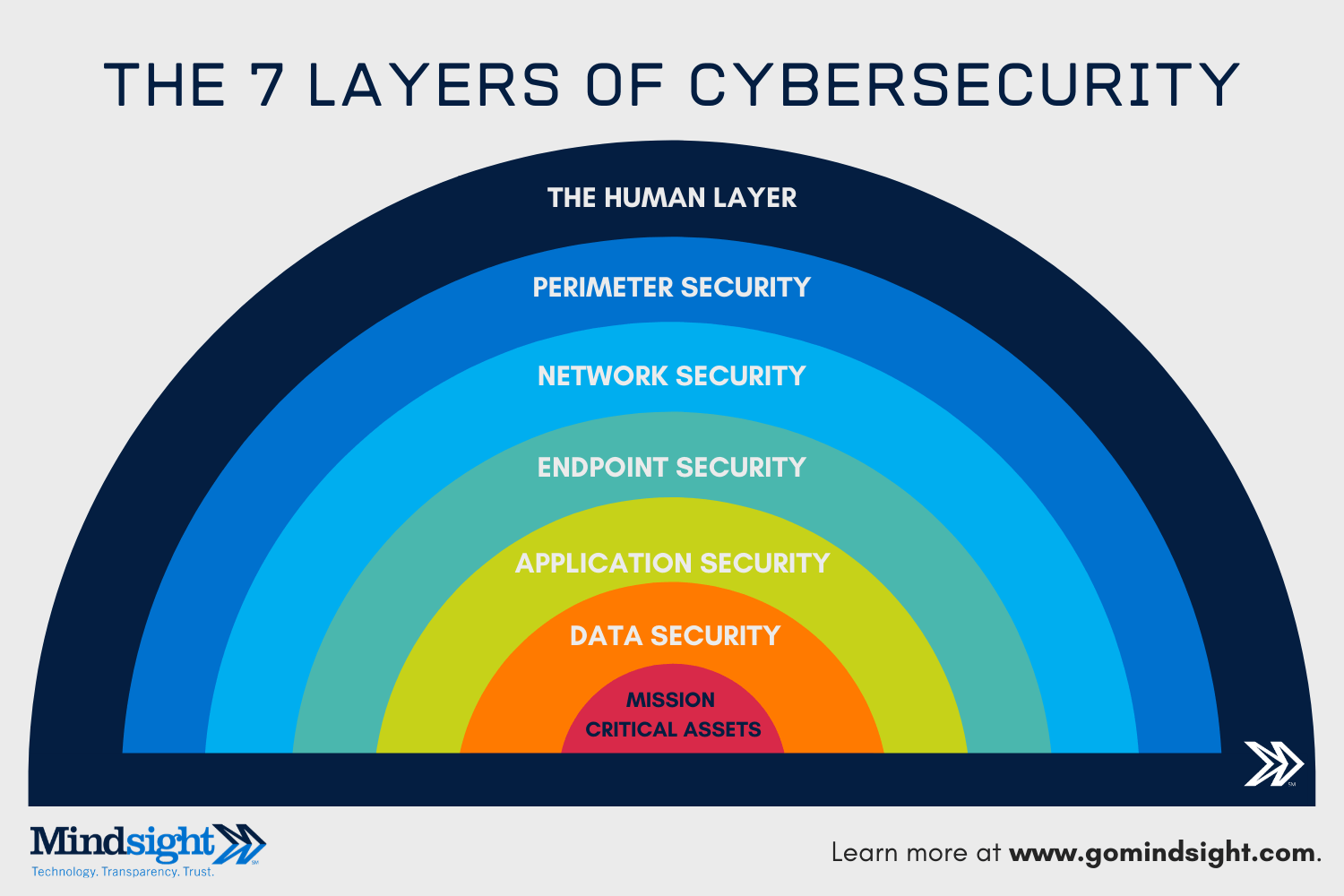
What Are The 7 Layers Of Security A Cybersecurity Report Mindsight Security architecture is the strategic design of systems, policies and technologies to protect it and business assets from cyberthreats. a well designed security architecture aligns cybersecurity with the unique business goals and risk management profile of the organization. security teams and hackers are often locked in an arms race. Network security architecture is a strategy that provides formal processes to design robust and secure networks. effective implementation improves data throughput, system reliability, and overall.

Understanding The 3 Phases Of Cybersecurity Architecture Ardoq Cybersecurity architects evaluate your existing security process and controls to find gaps and vulnerabilities to mitigate them before they become costly incidents. a well designed architecture is the key to a better posture that minimizes threats, builds customer trust, and facilitates growth. join sprinto’s 450 satisfied compliance conquerors. Cybersecurity architecture, simply put, is a framework that defines the structure of an organization's cybersecurity posture, which includes consideration for its policies, standards, and business objectives. it accounts for the organization's computers, network devices, network interconnects, security capabilities, and the data that resides. The 3 phases of cybersecurity architecture. security architects tailor their security approach to best fit their organization and sector, keeping in mind the risk calculations. most plans have 3 common elements: phase 1: develop policies, standards, and best practices. phase 2: implementation of phase 1. phase 3: monitoring of phases 1 and 2. Zero trust (zt) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network based perimeters to focus on users, assets, and resources. a zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. zero trust assumes there is no implicit trust.

Sse The Mvp Of The Cybersecurity Mesh Architecture Csa The 3 phases of cybersecurity architecture. security architects tailor their security approach to best fit their organization and sector, keeping in mind the risk calculations. most plans have 3 common elements: phase 1: develop policies, standards, and best practices. phase 2: implementation of phase 1. phase 3: monitoring of phases 1 and 2. Zero trust (zt) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network based perimeters to focus on users, assets, and resources. a zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. zero trust assumes there is no implicit trust. Gartner defines it as follows: cybersecurity mesh, or cybersecurity mesh architecture (csma), is a collaborative ecosystem of tools and controls to secure a modern, distributed enterprise. it builds on a strategy of integrating composable, distributed security tools by centralizing the data and control plane to achieve more effective. A network security architecture provides a basis for an organization’s cyber defenses and helps to protect all of the company’s it assets. here, we discuss the components of a network security architecture, how it benefits businesses, and different models for creating a secure network architecture. request a demo read the frost & sullivan.

Cyber Security Architecture Gartner defines it as follows: cybersecurity mesh, or cybersecurity mesh architecture (csma), is a collaborative ecosystem of tools and controls to secure a modern, distributed enterprise. it builds on a strategy of integrating composable, distributed security tools by centralizing the data and control plane to achieve more effective. A network security architecture provides a basis for an organization’s cyber defenses and helps to protect all of the company’s it assets. here, we discuss the components of a network security architecture, how it benefits businesses, and different models for creating a secure network architecture. request a demo read the frost & sullivan.

Comments are closed.