Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration

Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration Encryption services esp (encapsulating security payload) and ip protocol of 50. this document will outline basic negotiation and configuration for crypto map based ipsec vpn configuration. this document is intended as an introduction to certain aspects of ike and ipsec, it will contain certain simplifications and. The example in this chapter illustrates the configuration of a site to site vpn that uses ipsec and the generic routing encapsulation (gre) protocol to secure the connection between the branch office and the corporate network. figure 7 1 shows a typical deployment scenario. figure 7 1 site to site vpn using an ipsec tunnel and gre.

Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration 2 replies. aditya ganjoo. cisco employee. options. 07 05 2016 09:52 pm. hi rodrigo, static crypto map identifies peer and traffic to be encrypted explicitly. typically used to accommodate a few tunnels with different profiles and characteristics (different partners, sites, location) so when you have the information of both the peers that what. Crypto map based ipsec vpn fundamentals negotiation and configuration. this document will outline basic negotiation and configuration for crypto map based ipsec vpn configuration. this document is intended as an introduction to certain aspects of ike and ipsec, it will contain certain simplifications and. This article is a reference guide that includes general information, configuration, or troubleshooting documents related to vpn technologies in cisco secure firewall, cisco secure client (including anyconnect), and cisco ios ios xe. the documents in this list can be consulted before engaging cisco tac. From cisco ios xe release 17.6 through 17.9, both tunnel and transport modes are supported for crypto map based vpn solutions. from cisco ios xe release 17.10, only transport mode is supported for crypto map based vpn solutions.
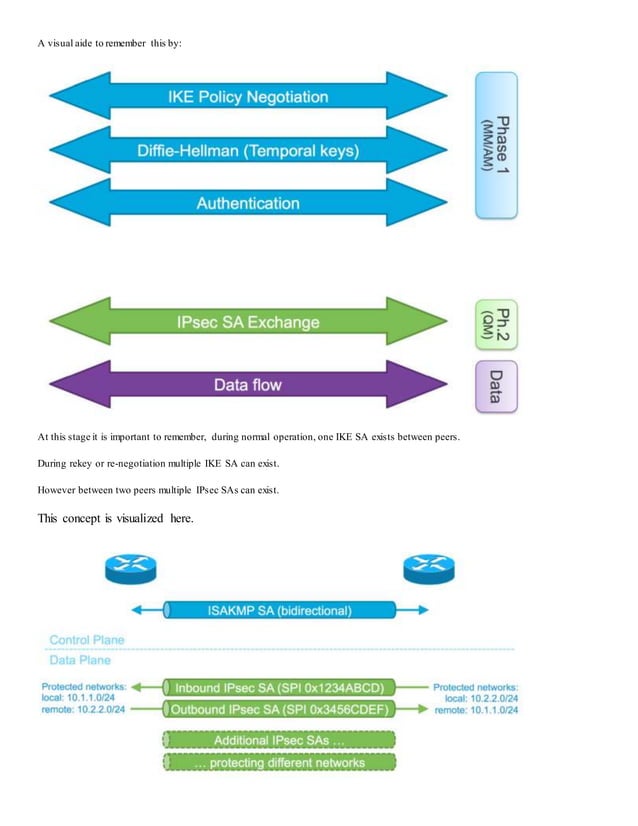
Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration This article is a reference guide that includes general information, configuration, or troubleshooting documents related to vpn technologies in cisco secure firewall, cisco secure client (including anyconnect), and cisco ios ios xe. the documents in this list can be consulted before engaging cisco tac. From cisco ios xe release 17.6 through 17.9, both tunnel and transport modes are supported for crypto map based vpn solutions. from cisco ios xe release 17.10, only transport mode is supported for crypto map based vpn solutions. This lab session i will be configuring and reviewing all aspects of site to site vpn configuration! will be going through a refresher on pretty basic vpn configuration including the following topics: define and configure the phase 1 and phase 2 settings for ipsec vpn; crypto map configuration to define correct “interesting traffic”. Remote access vpns for firepower threat defense. in our case, we have an existing remote access vpn configured with the access interface in the outside zone set to support the incoming connections: to change the transport protocol for the ra vpn, we edit the access interface and select “enable ipsec ikev2” in lieu of the default “enable.

Learn The Basics Of Ipsec Vpn Configuration This lab session i will be configuring and reviewing all aspects of site to site vpn configuration! will be going through a refresher on pretty basic vpn configuration including the following topics: define and configure the phase 1 and phase 2 settings for ipsec vpn; crypto map configuration to define correct “interesting traffic”. Remote access vpns for firepower threat defense. in our case, we have an existing remote access vpn configured with the access interface in the outside zone set to support the incoming connections: to change the transport protocol for the ra vpn, we edit the access interface and select “enable ipsec ikev2” in lieu of the default “enable.

Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration

Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration

Comments are closed.