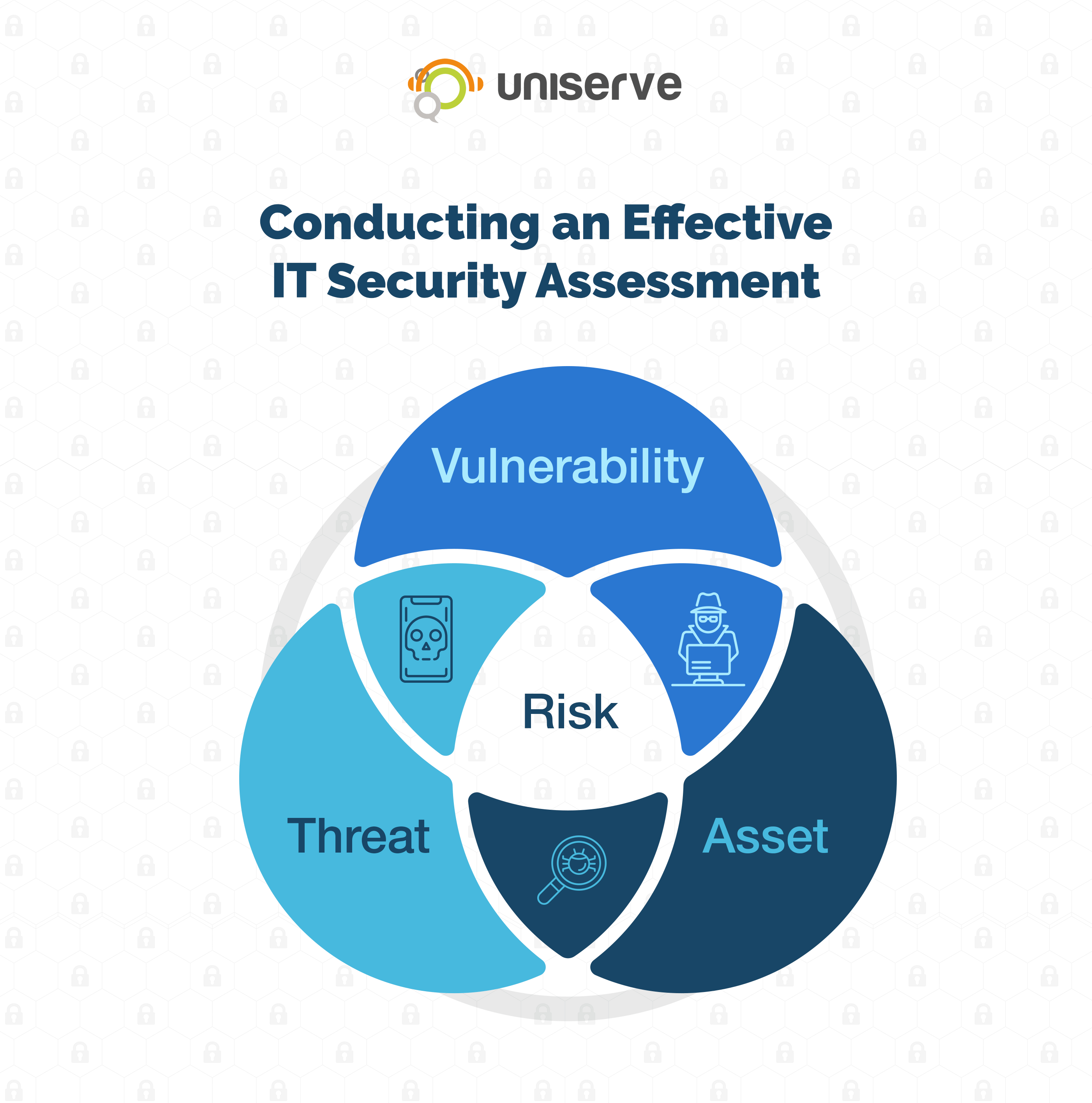
Conducting An Effective It Security Risk Assessment
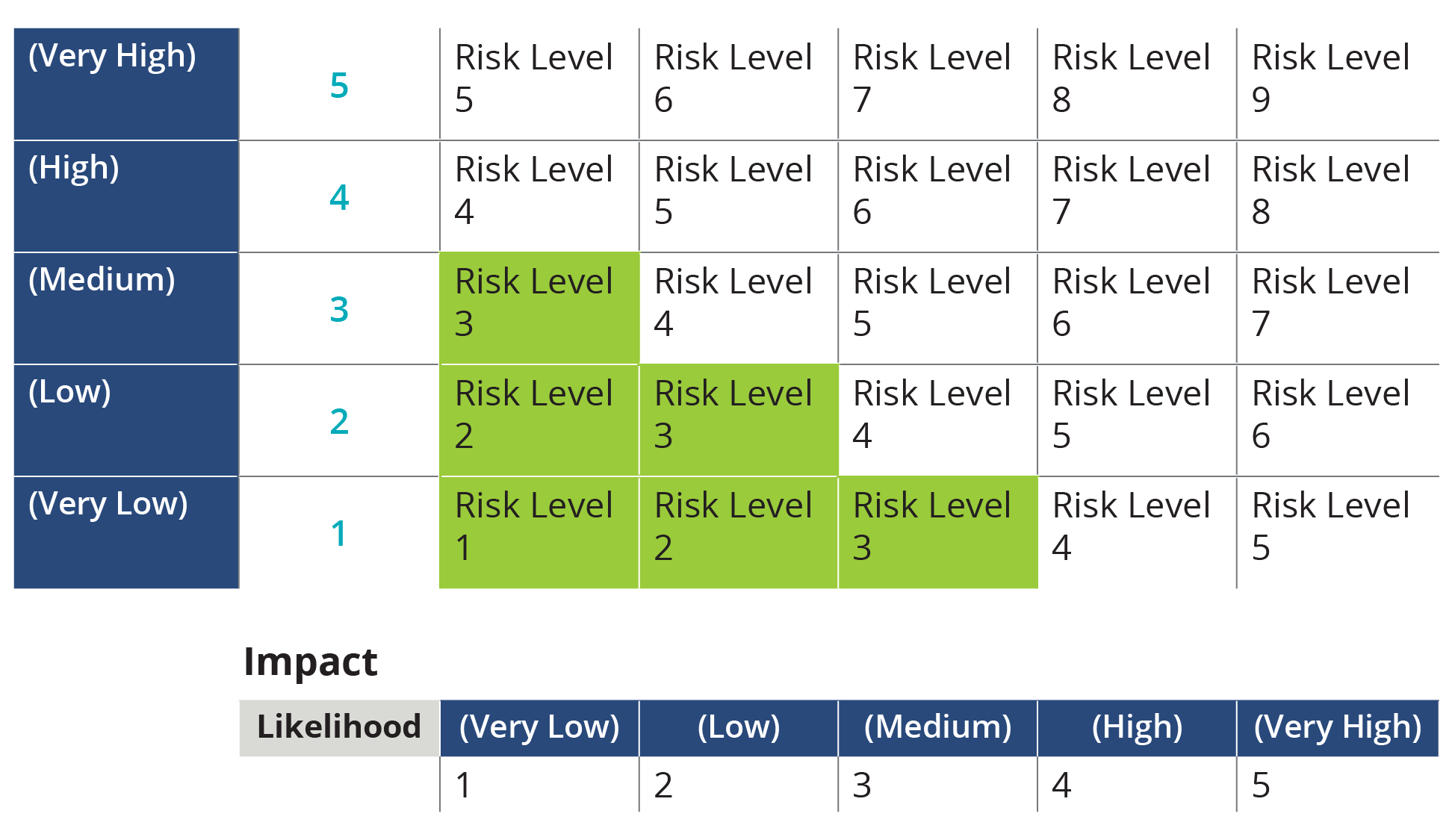
Conducting An Effective It Security Risk Assessment Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Here are seven key steps for conducting a comprehensive cyber risk assessment. 1. perform a data audit and prioritize based on value. establishing a comprehensive and current asset inventory is a foundational element of every company’s cybersecurity program.
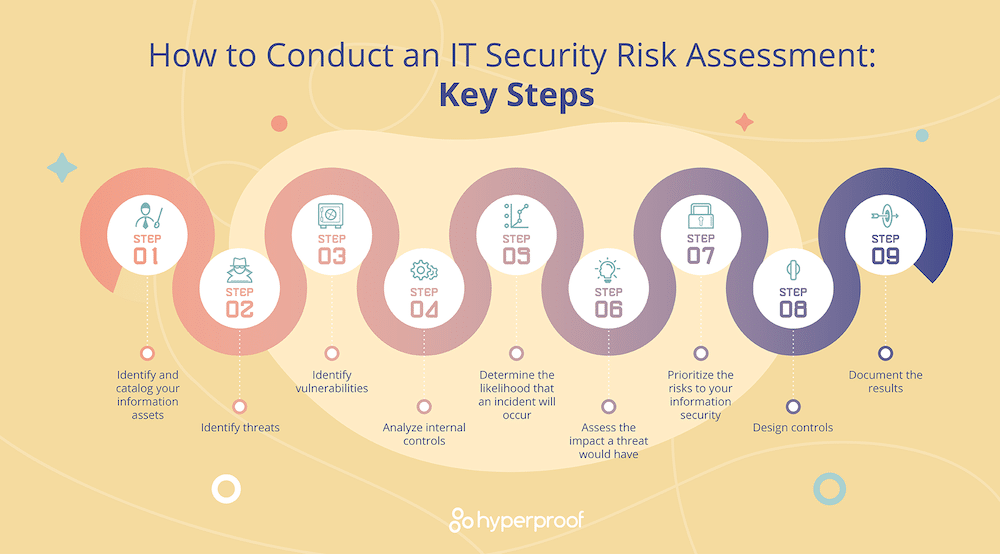
Conducting An Information Security Risk Assessment Hyperproof With this need to regularly assess risk, it is imperative that organizations have a strong risk assessment plan and methodology that addresses the assets, their value, the business processes that rely on them, the organization’s risk appetite and risk mitigation options. the conducting an it security risk assessment white paper explains how. 1. identify and prioritize assets. the first step is to survey your it environment and catalog the information and systems within it. a good place to start is to run an asset discovery scan, using some form of network of vulnerability scanning tool. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment. Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses.

Conducting An Effective It Security Risk Assessment Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment. Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses. Free trial. formulating an it security risk assessment methodology is a key part of building a robust information security risk management program. the two most popular types of risk assessment methodologies used by assessors are: qualitative risk analysis: a scenario based methodology that uses different threat vulnerability scenarios to try. The first step in conducting a cybersecurity risk assessment is to clearly define the scope and objectives of the assessment. this involves identifying what assets, systems, and processes will be evaluated. your scope should encompass all critical assets, including hardware, software, data, and personnel that are vital to your business operations.
Conducting A Successful Security Risk Assessment Free trial. formulating an it security risk assessment methodology is a key part of building a robust information security risk management program. the two most popular types of risk assessment methodologies used by assessors are: qualitative risk analysis: a scenario based methodology that uses different threat vulnerability scenarios to try. The first step in conducting a cybersecurity risk assessment is to clearly define the scope and objectives of the assessment. this involves identifying what assets, systems, and processes will be evaluated. your scope should encompass all critical assets, including hardware, software, data, and personnel that are vital to your business operations.

Comments are closed.