Conducting A Successful Security Risk Assessment Isg
Conducting A Successful Security Risk Assessment Isg Iso iec 27001:2013 (iso 27001) defines best practices for building and managing an information security management system (isms), a risk based approach to securing corporate information assets that addresses people, processes and technology. clause 6.1.2 of iso 27001 explains that the risk assessment process must, among other things, establish. Isg offers a comprehensive process for security risk assessment for your specific security needs and situation. do you know your building's risk level? skip navigation 866.393.4474.
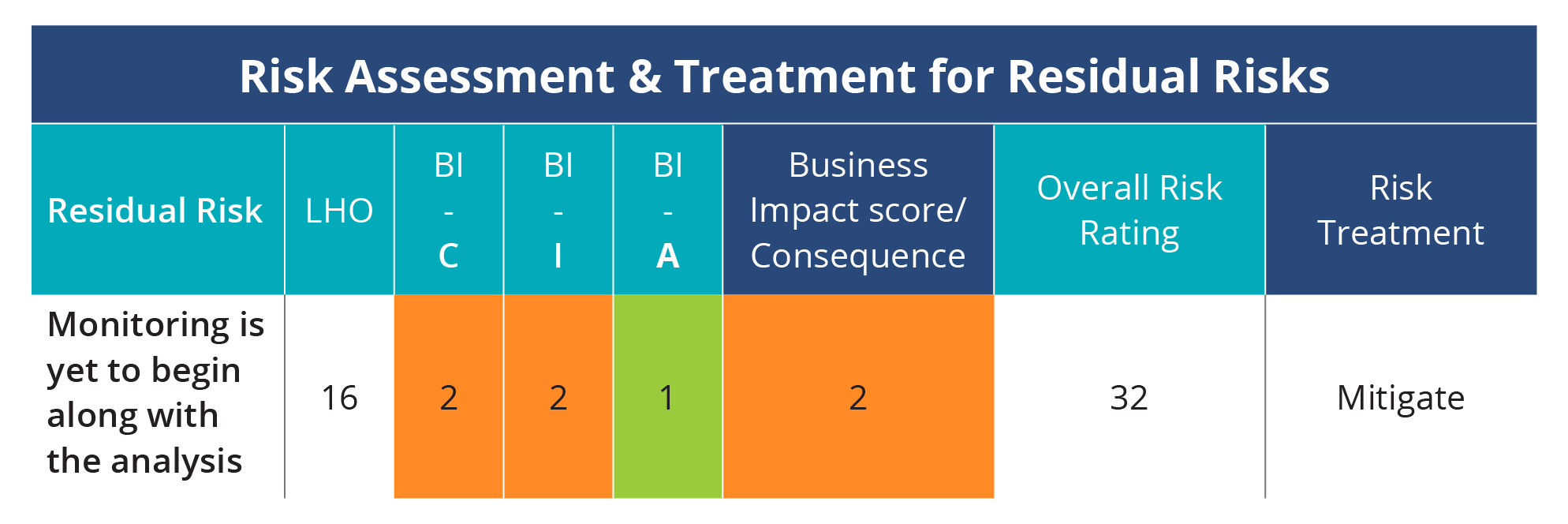
Conducting A Successful Security Risk Assessment Isg Summary. security risk assessments are essential to support business decisions. this guidance provides security and risk management technical professionals with best practices for achieving security risk assessments that drive optimization and efficiency in managing risk. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Conclusion. a successful security risk assessment is not a one time event but an ongoing process that requires vigilance, adaptability, and a proactive approach. by following the four steps outlined in this blog—identifying and prioritizing risks, conducting a vulnerability assessment, implementing security controls, and continuously. Reviewed by jason firch. may 21, 2022. there are 8 steps to conducting a security risk assessment including: mapping your assets. identifying security threats and vulnerabilities. determining and prioritizing risks. analyzing and developing security controls. documenting results. creating a remediation plan.

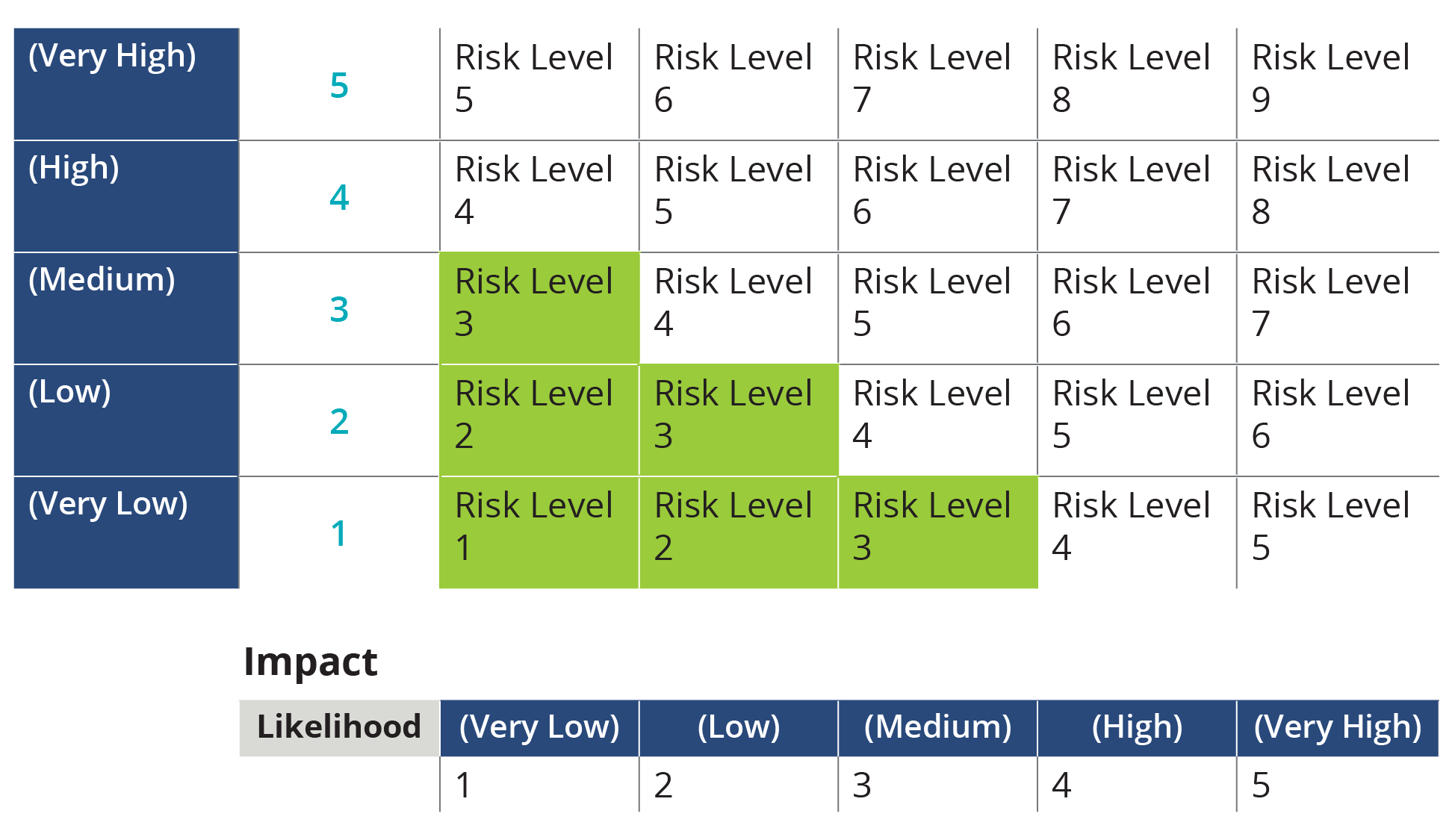
Conducting A Successful Security Risk Assessment Isg Conclusion. a successful security risk assessment is not a one time event but an ongoing process that requires vigilance, adaptability, and a proactive approach. by following the four steps outlined in this blog—identifying and prioritizing risks, conducting a vulnerability assessment, implementing security controls, and continuously. Reviewed by jason firch. may 21, 2022. there are 8 steps to conducting a security risk assessment including: mapping your assets. identifying security threats and vulnerabilities. determining and prioritizing risks. analyzing and developing security controls. documenting results. creating a remediation plan. Figure 1: five level scale for conducting qualitative risk assessments. to calculate that level of risk, we’ll utilize nist sp 800 30 again, which breaks down how the overall risk level is achieved as a calculation of the level of impact and the likelihood of occurrence on the same five point scale. Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses.

Comments are closed.