Ceh Classes Stages Phases Of Ethical Hacking
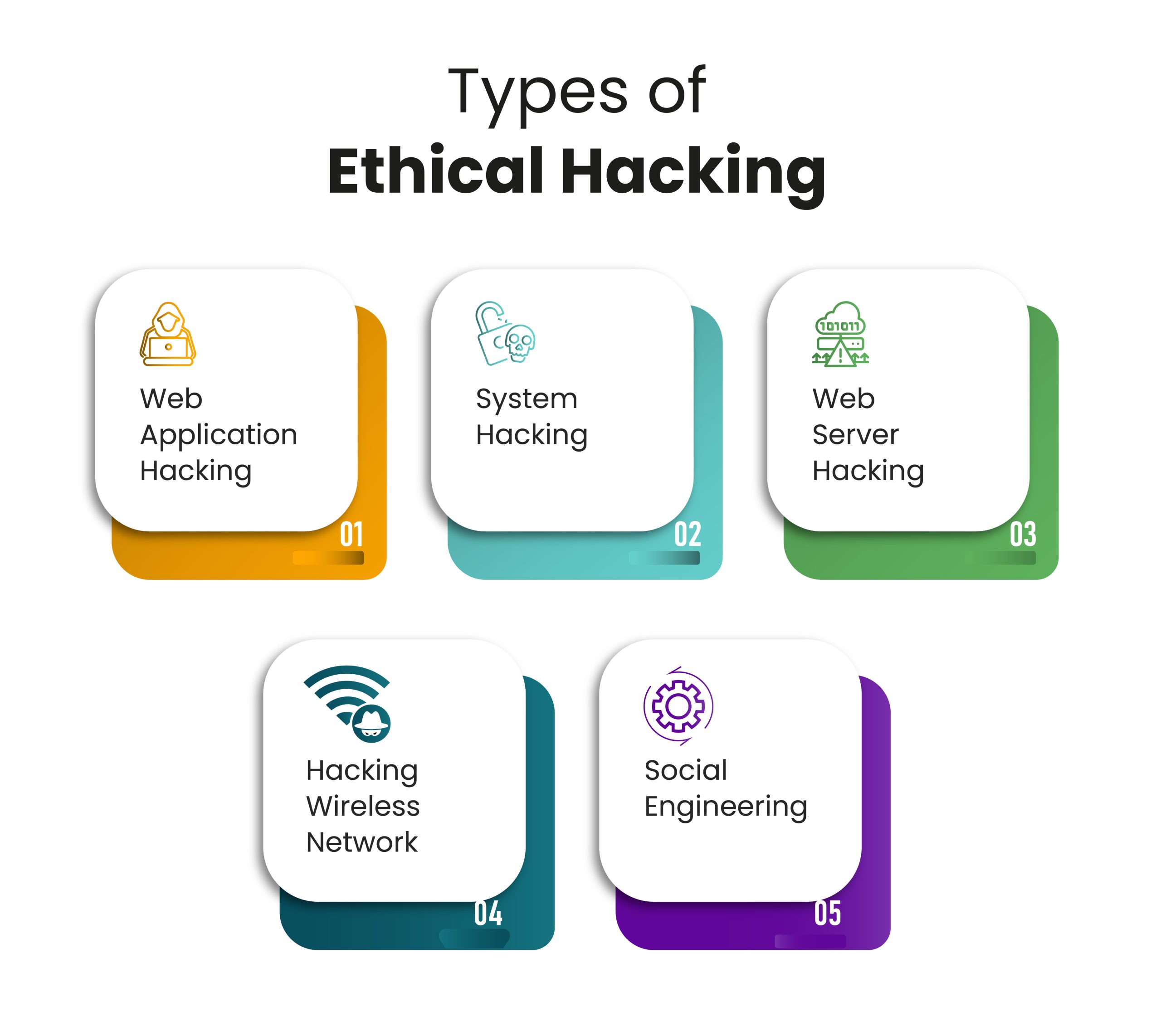
Phases Of Ethical Hacking Infosectrain Gain a competitive edge with ceh. from the creators of certified ethical hacker (ceh) comes the new and evolved version 13 with added ai capabilities. structured across 20 learning modules covering over 550 attack techniques, ceh provides you with the core knowledge you need to thrive as a cybersecurity professional. Certified ethical hacking the 5 phases every hacker must follow phase 5 covering tracks an attacker would like to destroy evidence of his her presence and activities for various reasons such as maintaining access and evading punitive action. erasing evidence of a compromise is a requirement for any attacker who would like to remain obscure.

Phases Of Ethical Hacking Hith Blog Hackerinthehouse The certified ethical hacker (ceh) provides an in depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. it will teach you how hackers think and act so you will be better positioned to set up your security infrastructure and defend against attacks. by providing an understanding of system. An ethical hacker follows the steps and thought process of a malicious attacker to gain authorized access and test the organization’s strategies and network. an attacker or an ethical hacker follows the same five step hacking process to breach the network or system. the ethical hacking process begins with looking for various ways to hack into. Ceh practical is a 6 hour, rigorous exam that requires you to demonstrate the skills and abilities in various ethical hacking techniques such as: port scanning tools (e.g., nmap, hping) vulnerability detection. attacks on a system (e.g., dos, ddos, session hijacking, web server and web application attacks, sql injection, wireless threats). In this course. 1. hacking phases. in this video, you will learn how to identify the five phases of hacking. free access. 2. ethical hacking concepts. after completing this video, you will be able to recall and identify the skills that are commonly needed by ethical hackers. free access.
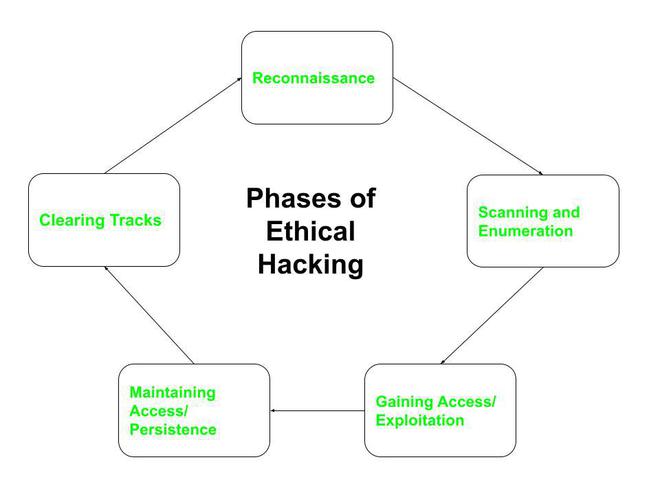
5 Phases Of Hacking Geeksforgeeks Ceh practical is a 6 hour, rigorous exam that requires you to demonstrate the skills and abilities in various ethical hacking techniques such as: port scanning tools (e.g., nmap, hping) vulnerability detection. attacks on a system (e.g., dos, ddos, session hijacking, web server and web application attacks, sql injection, wireless threats). In this course. 1. hacking phases. in this video, you will learn how to identify the five phases of hacking. free access. 2. ethical hacking concepts. after completing this video, you will be able to recall and identify the skills that are commonly needed by ethical hackers. free access. The certified ethical hacker (ceh) certification guide. the certified ethical hacker, or ceh certification, shows employers and other professionals that you keep up with the latest technology and strategies to protect it systems and networks from threats. learn how to apply the five phases of ethical hacking. master over 500 attack techniques. Ethical hacking: understanding ethical hacking. by dale meredith. a certified ethical hacker is a security professional who understands how to look for weaknesses in target systems and uses the same knowledge and tools as a malicious hacker. this course will teach you the foundations of this knowledge needed for the ceh 312 50 exam.

Ceh Classes Stages Phases Of Ethical Hacking Youtube The certified ethical hacker (ceh) certification guide. the certified ethical hacker, or ceh certification, shows employers and other professionals that you keep up with the latest technology and strategies to protect it systems and networks from threats. learn how to apply the five phases of ethical hacking. master over 500 attack techniques. Ethical hacking: understanding ethical hacking. by dale meredith. a certified ethical hacker is a security professional who understands how to look for weaknesses in target systems and uses the same knowledge and tools as a malicious hacker. this course will teach you the foundations of this knowledge needed for the ceh 312 50 exam.

Comments are closed.