8 Different Types Of Hackers And What They Do Best Explained

The Different Types Of Hacking Techniques Explained A Helpful Guide Grey hat hacking: a blend of both worlds. the “grey” in grey hat hacking signifies the borderland these hackers inhabit. they straddle the line as far as legality and ethics open in new. grey hat hackers are not affiliated with any organization, though they may work in the technology industry by day. They are inspired by the hackers and ask them few questions about. while hackers are answering their question they will listen to its novelty. blue hat hackers: they are much like the white hat hackers, they work for companies for security testing of their software right before the product launch. blue hat hackers are outsourced by the company.
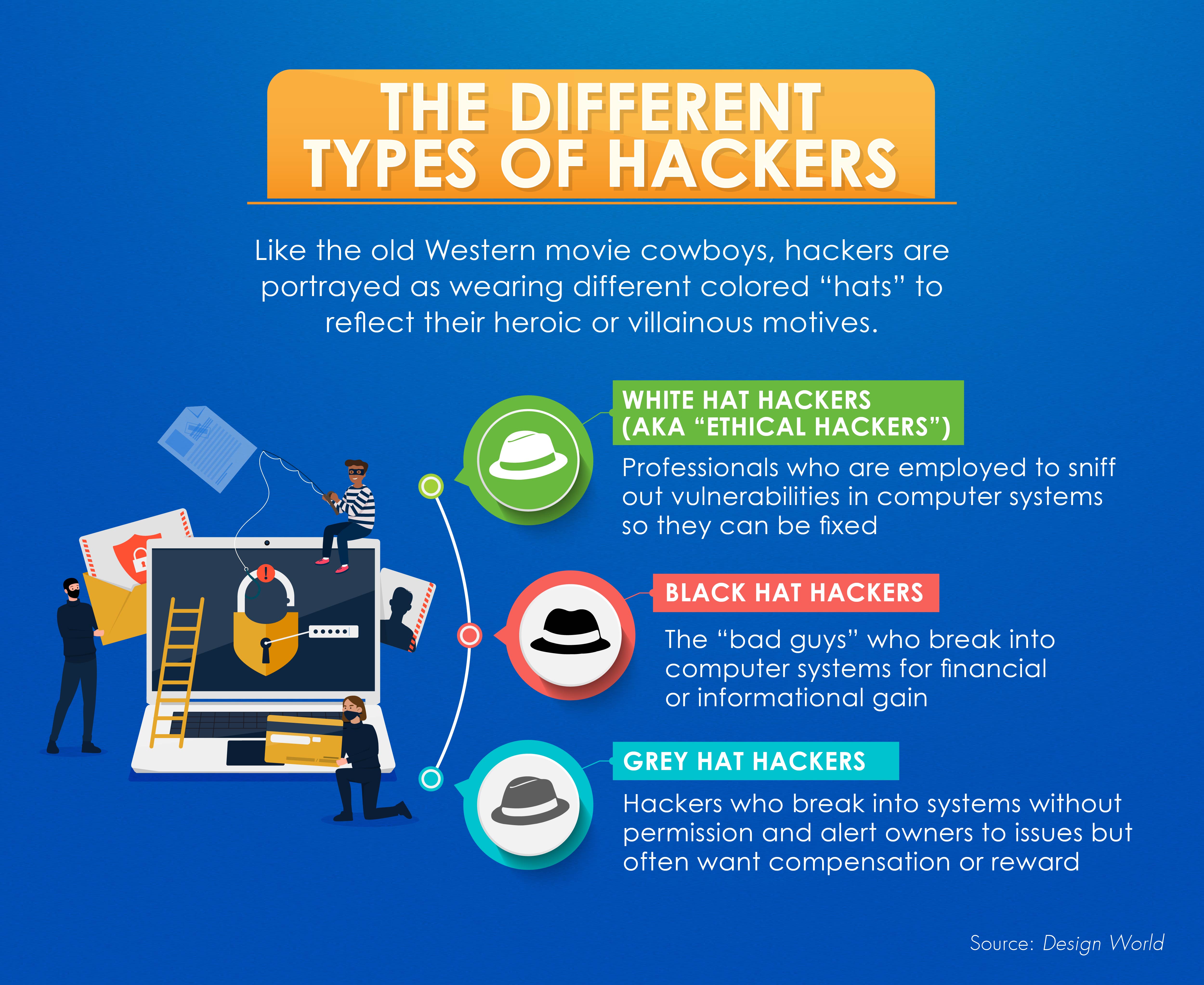
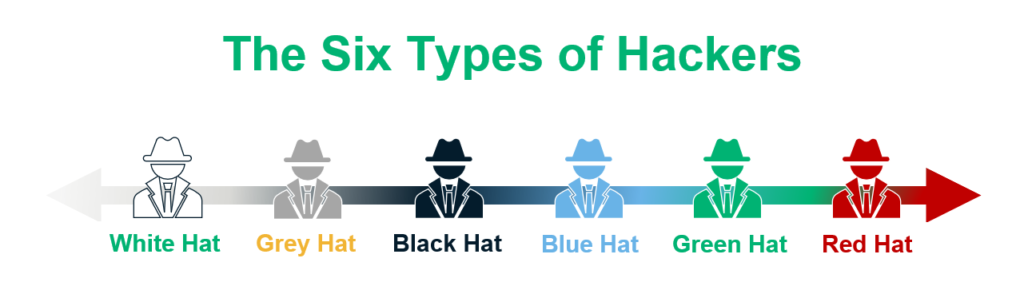
Types Of Hackers The Hats They Wear And What They Do Maryville Online Different types of hackers: the 6 hats explained. (75 votes, average: 4.77 out of 5) black hat, white hat, grey hat, red hat, blue hat, and green hat. no, these aren’t items in an apparel store’s catalog — they’re the different types of hackers you’ll find in the cybersecurity industry. the term “hacker” is often portrayed. Understanding the different types of hackers is crucial for navigating the intricate landscape of cybersecurity. in this comprehensive guide, we will delve into the various categories of hackers, exploring what sets them apart and the impact they have on the digital world. 1. white hat hackers. white hat hackers, also known as ethical hackers. That’s the crucial difference between a white hat vs a black hat hacker. black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of. The world of hacking is a complex and multifaceted landscape with various types of hackers operating within it. each type brings their own motivations, skill sets, and ethical considerations to the table. understanding the different categories of hackers is essential for comprehending the risks and challenges associated with cybersecurity.

Different Types Of Hackers Explained 2024 That’s the crucial difference between a white hat vs a black hat hacker. black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of. The world of hacking is a complex and multifaceted landscape with various types of hackers operating within it. each type brings their own motivations, skill sets, and ethical considerations to the table. understanding the different categories of hackers is essential for comprehending the risks and challenges associated with cybersecurity. Also known as threat actors, black hat hackers are the stereotypical cybercriminals who attempt to break into personal devices and networks using ransomware, spyware, phishing techniques, and other methods. the objective of black hat hacking is often to collect sensitive data to exploit or sell for profit. you may recall hearing about the nba. They are responsible for the majority of data breaches and are primarily motivated by money. they’re known for atm fraud (‘jackpotting’), credit card and gift card theft, ransomware, and data theft (among other attacks). the most common attack from cyber criminals is mass phishing campaigns, as these can be used to distribute ransomware.
Different Types Of Hackers The 6 Hats Explained Infosec Insights Also known as threat actors, black hat hackers are the stereotypical cybercriminals who attempt to break into personal devices and networks using ransomware, spyware, phishing techniques, and other methods. the objective of black hat hacking is often to collect sensitive data to exploit or sell for profit. you may recall hearing about the nba. They are responsible for the majority of data breaches and are primarily motivated by money. they’re known for atm fraud (‘jackpotting’), credit card and gift card theft, ransomware, and data theft (among other attacks). the most common attack from cyber criminals is mass phishing campaigns, as these can be used to distribute ransomware.

The Complete Guide To Ethical Hacking University Of Denver Boot Camps

Comments are closed.